Executive Summary
While malicious and fake apps in the Google Play Store is common, Shreshta Threat Intelligence team has detected multiple fake Google Play Store websites which impersonate the Google Play Store.
This gives an impression to the user, that they are visiting the Google Play Store. If the user clicks on the Install button, the phishing website prompts the user to save an APK file on the mobile device and install it via sideload1.
1Sideload is installing an application on a mobile device without using the device’s official application distribution method.
Technical analysis of fake Google Play Store phishing websites
Google Play Store Phishing website #1
Figure 1 – Phishing website impersonating Google Play Store app Lucky Rabbit
Phishing website #2
Figure 2 – Phishing website impersonating Google Play Store app Fortune Tiger
Phishing website #3
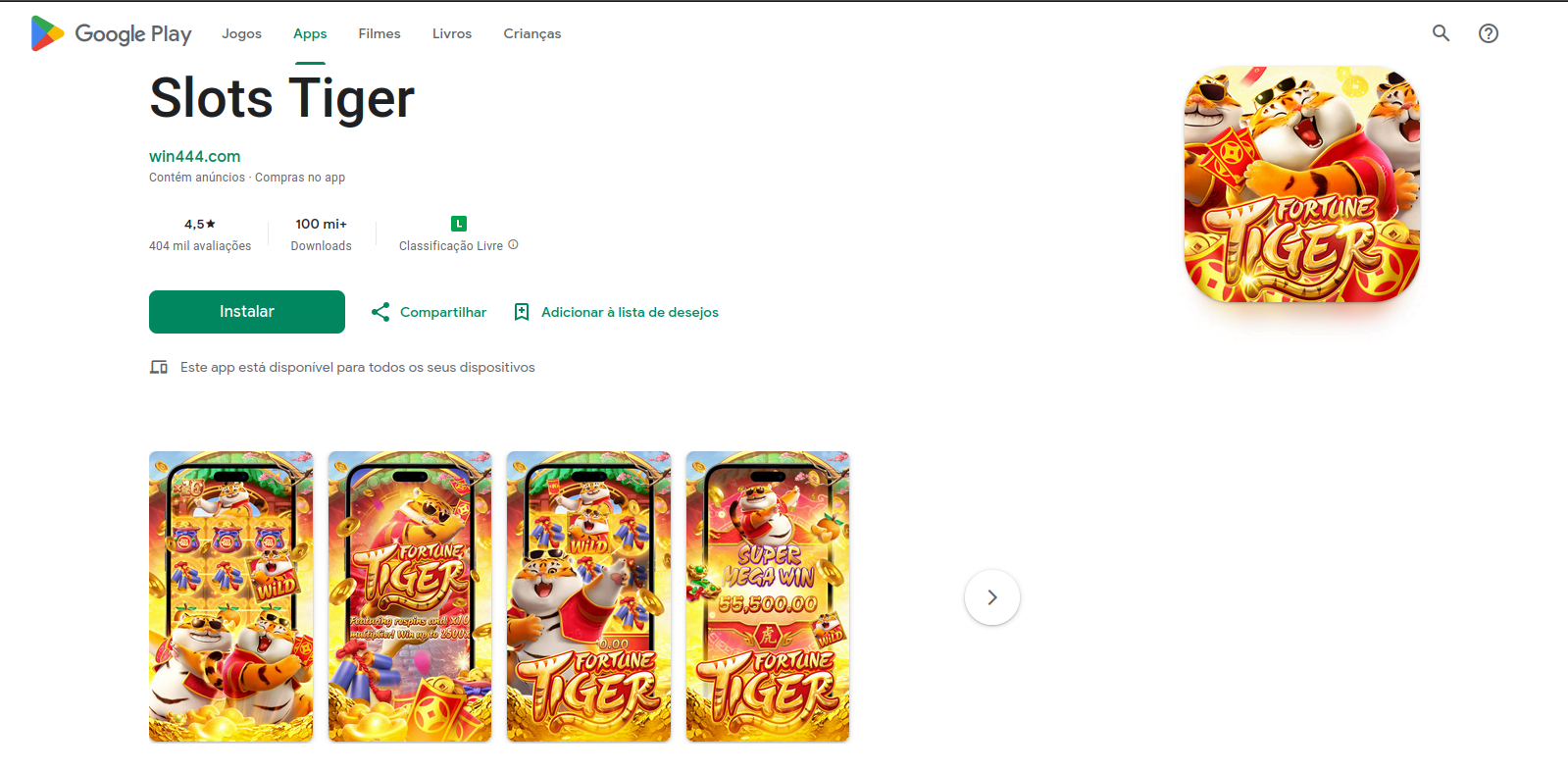
Figure 3 – Phishing website impersonating Google Play Store app Slots Tiger
Phishing website #4
Figure 4 – Phishing website impersonating Google Play Store app Fortune Tiger 136bet
Phishing website #5
Figure 5 – Phishing website impersonating Google Play Store app Fortune Tiger widlbet
Phishing website #6
Figure 6 – Phishing website impersonating Google Play Store app Fortune Games 888win
Phishing website #7
Figure 7 – Phishing website impersonating Google Play Store app Lucky Rabbit
Phishing website #8
Figure 8 – Phishing website impersonating Google Play Store app Lucky Rabbit
Phishing website #9
Figure 9 – Phishing website impersonating Google Play Store app Glimmer Teen Patti
Phishing website #10
Figure 10 – Phishing website impersonating Google Play Store
app Teen Patti Master
Phishing website #11
Figure 11 – Phishing website impersonating Google Play Store app Teen Patti Gold
Network Infrastructure Analysis
Figure 12 – Country-wise distribution of locations of the phishing websites
Figure 13 – Autonomous System wise distribution of the locations of the phishing websites
Safety Recommendations
- Configure Browse Safe DNS Servers on your devices to block phishing, malware, cryptojacking and other cyber threats.
- Download apps only from the official Google Play Store
- Any website which prompts downloading of an APK file should be treated as malicious
- If you become a victim of cybercrime, call the national (India) cybercrime helpline 1930 or file a complaint at https://cybercrime.gov.in/
- If you are an enterprise, protect your organisation in real-time from cyber threats such as phishing, malware, newly registered domain names and other malicious communication using Shreshta Protective DNS. Please email info@shreshtait.com for a free 30-day trial.
Conclusion
Our analysis of the fake Google Play Store websites shows that the threat actors use deception technique along with social engineering to lure users into installing fake and malicious apps.
Indicators of Compromise
https[:]//h27.in/aw/2kieo
https[:]//h27.in/c/red/m/hj60an?f=w&p=wa&tp=aw1
https[:]//h27.in/gold/13ksl
https[:]//h27.in/gold/cvr8eh
https[:]//h27.in/gold/s03q
https[:]//h27.in/m/sjcg
https[:]//h27.in/m/tbqy3
https[:]//h27.in/m/teuo01
https[:]//h27.in/m/ywrh8
https[:]//h27.in/sm/hf59i2
https[:]//h29.in/bws/kakx9
https[:]//h29.in/epic/kakx9
https[:]//h29.in/gold/kakx9
https[:]//h29.in/gold/twh1a
https[:]//h29.in/m/kakx9
https[:]//h29.in/m/twh1a
https[:]//h29.in/sm/kakx9
https[:]//h29.in/ysl/kakx9
https[:]//share.bigswinner.online/?appKey=nzwvop&af_status=share-link&clickLabel=MA==&agent=levana2
https[:]//share.bigswinner.online/?appKey=nzwvop&af_status=share-link&clickLabel=MA==&agent=levana3
https[:]//share.bigswinner.online/?appKey=nzwvop&af_status=share-link&clickLabel=MA==&agent=levana4
https[:]//share.bigswinner.online/?appKey=nzwvop&af_status=share-link&clickLabel=MA==&agent=levana5
https[:]//share.bigswinner.online/?appKey=nzwvop&af_status=share-link&clickLabel=MA==&agent=levana6
https[:]//share.bigswinner.online/?appKey=nzwvop&af_status=share-link&clickLabel=MA==&agent=levana7
https[:]//nn5.pw/aw/4r47j
https[:]//nn5.pw/aw/ddvpb
https[:]//h25.in/gold/13ksl
https[:]//h25.in/gold/qpqgd
https[:]//h25.in/m/13ksl
https[:]//h25.in/m/qpqgd
https[:]//h25.in/m/tutoa
https[:]//h25.in/sm/qpqgd
https[:]//h25.pw/aw/r0efo
https[:]//h25.pw/gold/alxwr
https[:]//share.getfun.in/?2jrliqec_2d833h
https[:]//share.getfun.in/?2jrm3qq2_2d833h
https[:]//hh7.pw/aw/mrj2y
https[:]//h26.in/c/blue/gold/ywrh8?f=w&p=wa&tp=gold1
https[:]//h26.in/c/red/m/6jv1di?f=w&p=default&l=en&tp=m31
https[:]//h26.in/gold/comsr
https[:]//h26.in/gold/mgmrq
https[:]//h26.in/gold/teuo01
https[:]//h26.in/m/comsr
https[:]//h26.in/m/mgmrq
Recommended Reading
A few other threat intelligence blog posts that you might be interested in,
