Domain shadowing is a technique listed by MITRE ATT&CK as T1584.001 sub-technique of T1584

This technique is not to be confused with subdomain hijacking
What is a domain shadowing attack?

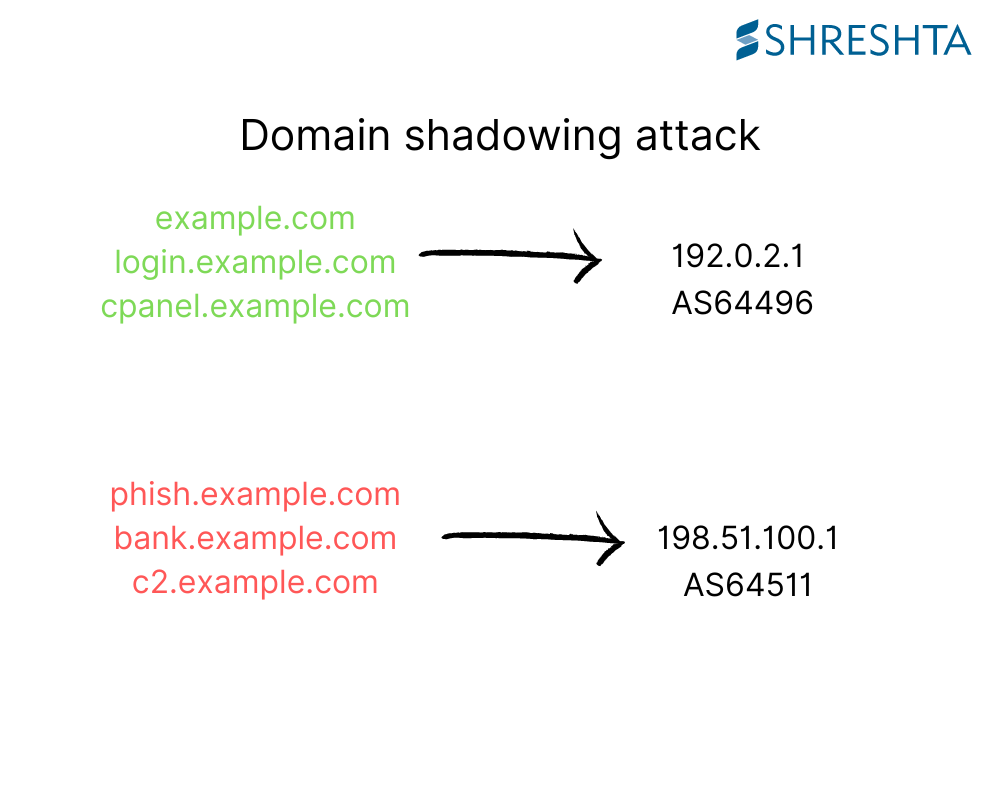
Threat actors gain control of the DNS control panel of legitimate domain names by brute force and stealthily insert subdomains pointing to the attackers’ network infrastructure.
The DNS records of the apex domain name are untouched.
Why does domain shadowing attack occur?
Our hypothesis for the most likely scenario is that the attackers use brute force on the registrants’ domain name control panel. Once successful, stealthy create subdomains under legitimate domain names, which point to the attackers’ infrastructure.
Here are the reasons why this attack is possible,
- Weak passwords
- 2FA is either not available or not enabled
- Registrars provide no monitoring/alerting system to notify when a modification is made to the DNS zone of the domain name.
Threat actors perspective
Creating and using subdomains under legitimate domain names for malicious purposes, such as phishing, malware, etc, has many benefits from the threat actors’ perspective.
- Leveraging domain name reputation – By using the reputation of the legitimate domain name, threat actors can evade detection
- Minimize efforts and time – Eliminate efforts into buying a domain name(with stolen funds ofcourse!)
Shreshta threat intelligence team has been monitoring domain names under gTLDs and ccTLDs using our passive DNS product DNS Watchtower. In the past, we have also documented these attacks targeting domain names under .LK
Recommendations
As a domain name registrant, here are a few things that you can do to stop a domain shadowing attack,
- Enable 2-factor authentication(2FA) – If available, enable 2FA in the domain name control panel, which the registrar provides
- Password hygiene – Set a strong and unique password to the domain name control panel
- Monitor the DNS records – Periodically monitor the DNS zone
Monitoring the DNS records is not feasible for registrants since the registrars provide no alerting/monitoring feature. Our team has been working in this space. Stay tuned!
Update – March 13th 2024 – We’ve published a blog post with the details of ShadowFindr, a web tool we released last month.
