Before we deep dive into how attackers target .lk domains using domain shadowing attack, first, a primer on registration of a domain name under .lk namespace.
tl;dr registration of a domain name under .lk namespace is regulated
The domain registration policy says the LK registry may ask for documents supporting the request for a domain name registration. Depending on the category the domain registration would fall under, the list of documents would vary,

Figure 1: Screenshot of LK domain registration supporting documents list
The regulation makes it extremely hard for attackers to register a domain name for malicious purposes. Without the supporting documentation, the LK registry will not add the domain name in the .lk ccTLD.
That does not stop the attackers from abusing domain names under .lk. Attackers use innovative methods to target users.
Shreshta threat intelligence has uncovered attackers targeting .lk domains using domain shadowing attack.
For a detailed insight into domain shadowing, see our blog post
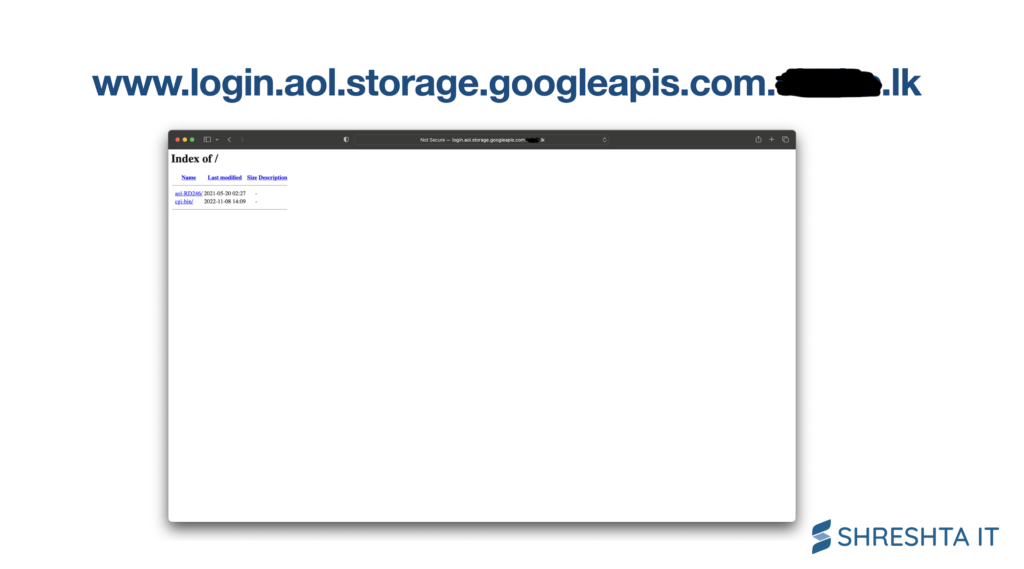
Figure 2: Screenshot of a opendir page accessible via a subdomain
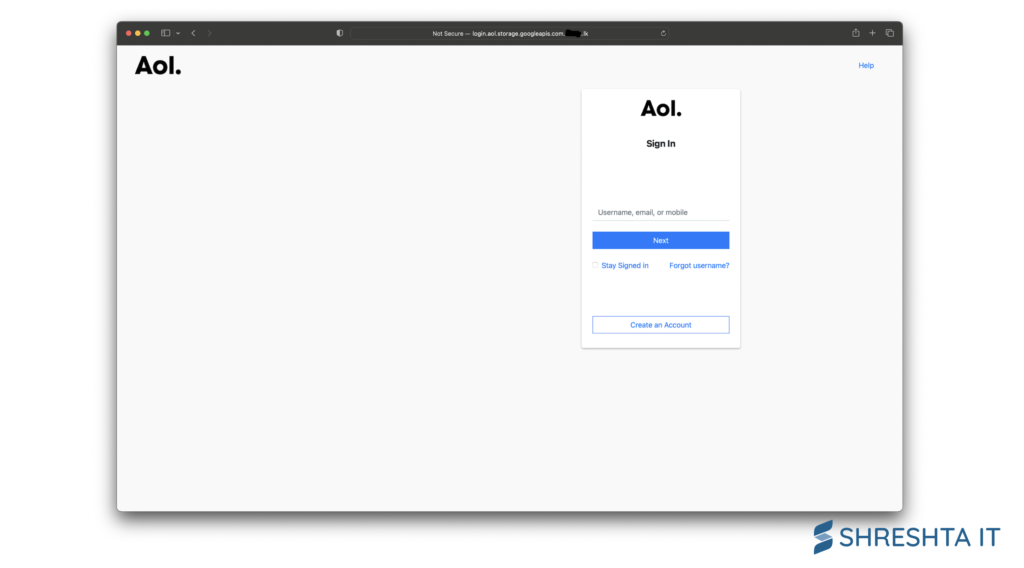
Figure 3: Screenshot of AOL phishing page under a benign domain name
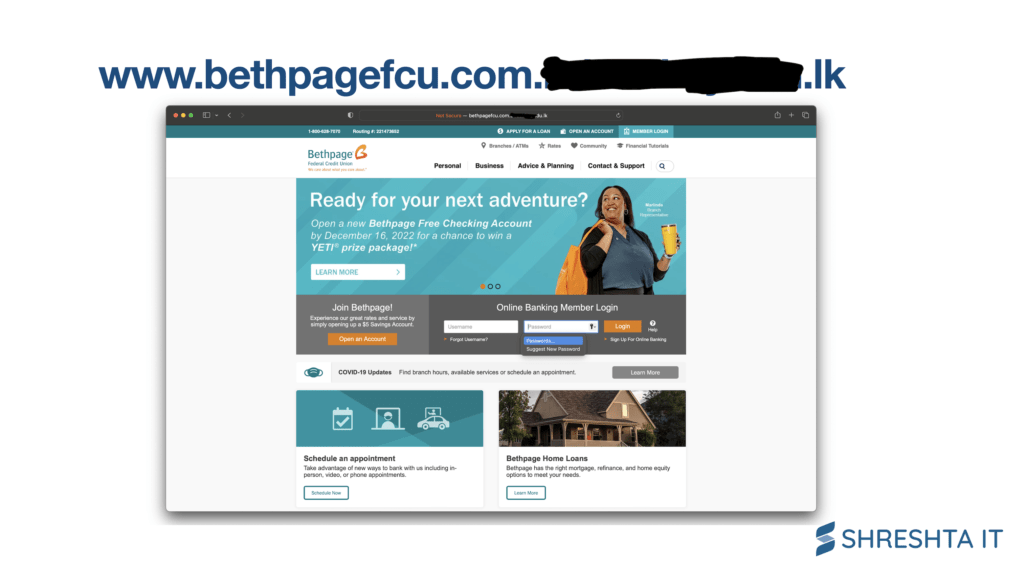
Figure 4: Screenshot of www.bethpagefcu.com phishing page under a benign domain name
Figure 5: Screenshot of www.maerkische-stanz-partner.de phishing page under a benign domain name
Figure 6: Screenshot of www.moncheflafee.fr phishing page under a benign domain name
Conclusion
How is this happening?
Our hypothesis for the most likely scenario is that the attackers use brute force on the registrants’ domain name control panel. Once successful, stealthy create subdomains under legitimate domain names, which point to the attackers’ infrastructure.
As a domain name registrant, here are a few things that you can do to stop a domain shadowing attack,
- Enable 2FA in the domain name control panel which is provided by the registrar
- Password hygiene
- Periodically monitor the DNS zones – there are a few free and paid services which enable you to do this
Get free access to Newly registered domain names (NRD) community feeds
Newly registered domain names or recently registered domains can be a potential security risk for organisations. They are often used to host phishing, malware, and other malicious content.
By monitoring or blocking NRDs, enterprises can eliminate the risk of cyber threats posed by NRDs.
Get no-cost access to our newly registered domain names(NRD) community feeds.