Security researchers at Shreshta have identified a phishing campaign targeting Indian citizens.
Executive Summary
The Income Tax Department (also referred to as IT Department or ITD) is a government agency undertaking direct tax collection of the Government of India. It functions under the Department of Revenue of the Ministry of Finance. The main responsibility of the Income Tax Department is to enforce various direct tax laws, most important among these being the Income-tax Act of 1961, to collect revenue for the government of India.1
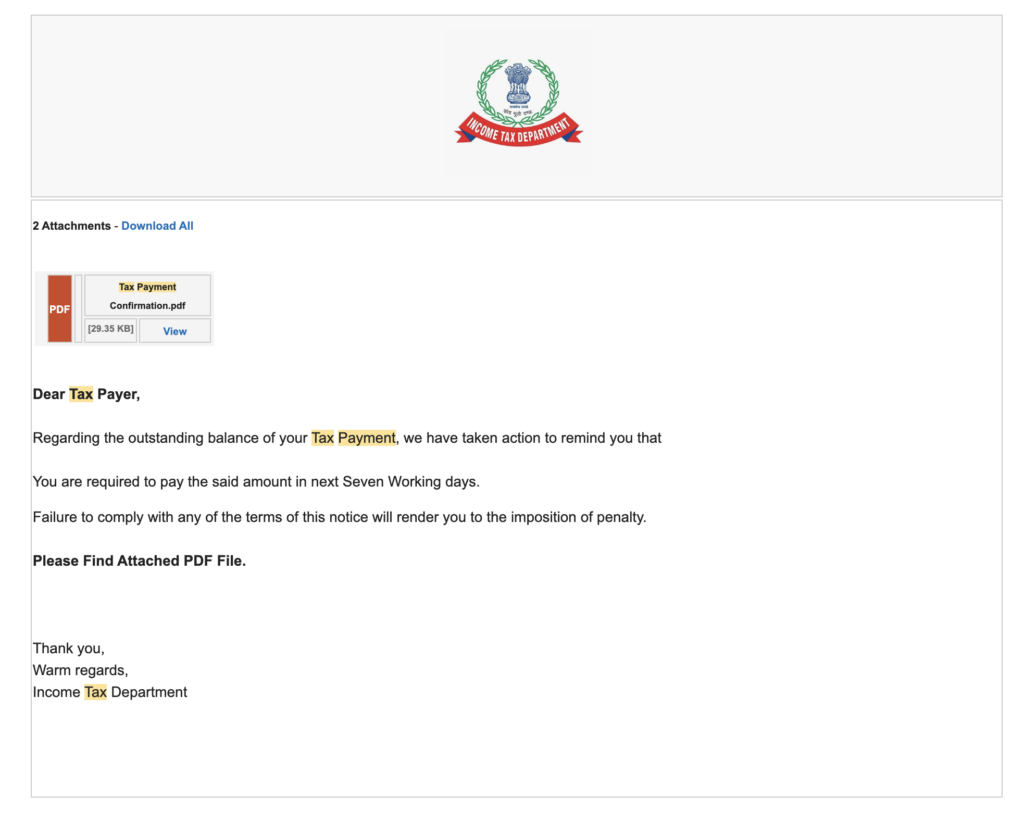
We have identified a phishing campaign targeting Income Tax users of India wherein the phishing email tempts the user to download a PDF zip file. The zip file contains an exe file, Kutaki keylogger.
Phishing email targeting Indian citizens – Income tax
Threat Indicators
-
- The phishing email lures the users to download a PDF file “Tax Payment Confirmation.pdf”
-
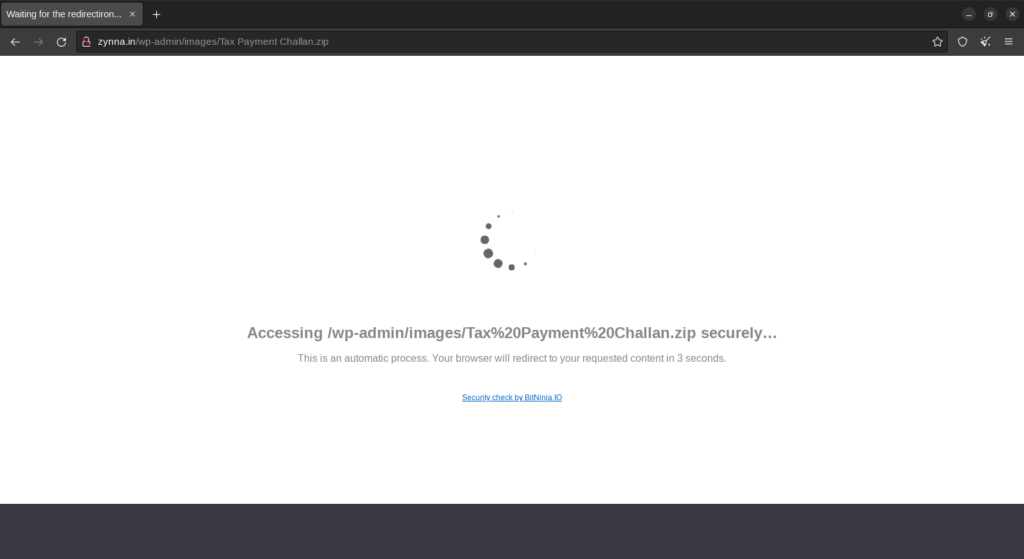
- When the users clicks on the PDF image in the phishing email, it downloads “Tax Payment Challan.zip” from kmtractors[.]in/img/images/itz[.]htm
-
- The threat actors have compromised a legitimate website(kmtractors[.]in) and uploaded a malware in one of their sub-directories
-
- Extracting “Tax Payment Challan.zip” saves “Tax Payment Challan.exe”
-
- “Tax Payment Challan.exe” is Kutaki keylogger
-
- The domain name kmtractors[.]in was registered by Endurance Digital Domain Technology LLP.
-
- Domain name registration date – 04-12-2010
-
- The domain kmtractors[.]in resolves to IP address 46.4.61.150
-
- File distribution originates from IP address 164.52.213.142
-
- The SHA256 hash of “Tax Payment Challan.zip” is 7848994b7a5bf36ffaedbe9049bb15b215811a82ecd2ff548ea76e4a48819685
-
- The SHA256 hash of “Tax Payment Challan.exe” is f2777ba8469053dbb35353cf54caf343329dbd721f31de2225eccbfd33d1fd6a
-
- After execution, “Tax Payment Challan.exe” connects to newbosslink[.]xyz[/]baba/new4[.]php
-
- The domain name newbosslink[.]xyz registered by Namecheap
-
- The domain name newbosslink[.]xyz resolves to the IP address 91.223.82.124
-
- The IP address 91.223.82.124 belongs to AS199968 IWS NETWORKS LLC
- The AS199968 is based in Amsterdam
Malware hosted on the website kmtractors[.]in/img/images/itz[.]htm
Get free access to Newly registered domain names (NRD) community feeds
Newly registered domain names or recently registered domains can be a potential security risk for organisations. They are often used to host phishing, malware, and other malicious content.
By monitoring or blocking NRDs, enterprises can eliminate the risk of cyber threats posed by NRDs.
Get no-cost access to our newly registered domain names(NRD) community feeds.
Download the free NRD community feeds

