Executive Summary
Shreshta Threat Intelligence has uncovered a rise in phishing attacks targeting Adobe users in India. The attack begins by sending emails to employees working at Micro Small and Medium Enterprises(MSME), large enterprises, and luring them to click on a link which impersonates a Purchase Order or a Work Order document.
The attack uses social engineering to deceive the user into believing that the PDF document contains a Purchase Order or a Work Order document and that they need to click on the link and login in order to access or download it.
After reviewing the phishing campaign, we have concluded that this campaign operates by sending phishing URLs to enterprise users via email.
The emails lure the user to log in, in order to view or download the documents, thereby deceiving them into providing their login credentials.
The phishing attacks targeting Adobe users in India has seen a massive uptick in the past few months.
About Adobe
Adobe Inc., formerly Adobe Systems Incorporated, is an American multinational computer software company incorporated in Delaware and headquartered in San Jose, California. It has historically specialized in software for creating and publishing a wide range of content, including graphics, photography, illustration, animation, multimedia/video, motion pictures, and print. Its flagship products include Adobe Photoshop image editing software; Adobe Illustrator vector-based illustration software; Adobe Acrobat Reader and the Portable Document Format (PDF); and a host of tools primarily for audio-visual content creation, editing and publishing.1
Motive
We can share with moderate confidence that the motive of the threat actors is to harvest the user’s enterprise login credentials such as Microsoft Outlook, Office 365 etc that are used to access the services of Adobe.
Technical analysis of phishing attacks targeting Adobe users in India
In this section, we will unpack how Adobe users in India are being specifically targeted and also share the techniques the threat actors are using to lure enterprise users in clicking the phishing websites.
Phishing website #1
Figure 1- The phishing page prompts the user to enter their Adobe Acrobat login credentials
The phishing website contains links to the official Adobe Acrobat to make it appear legitimate.
Figure 2 – After entering the password, the website throws an error , stating, “Your email and password do not match. Please try again.”
Phishing website #2
Figure 3 – The phishing website prompts the user to enter their login credentials to access the PDF document
Figure 4 – After entering the login credentials and clicking the “VIEW DOCUMENT” button, the user is redirected to a genuine Microsoft support page
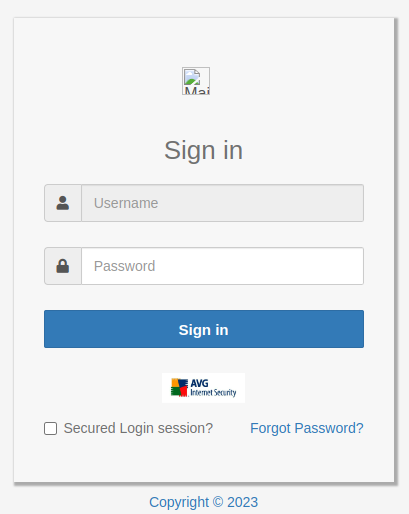
Figure 5 – The phishing page prompts the user to enter their credentials.
The “Forgot Password” is plain text without any associated links
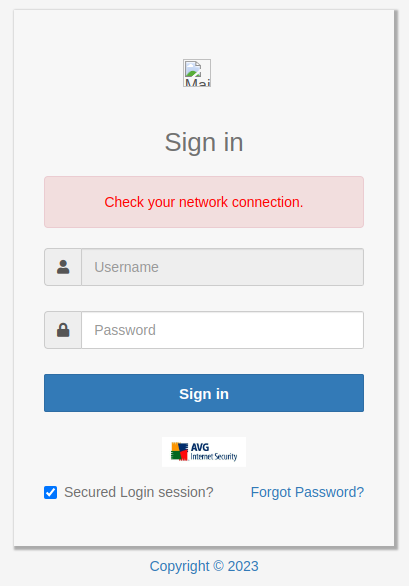
Figure 6 – The phishing page throws a network connection error
The phishing website is poorly constructed, users can only input data into the password field as the username field is grayed out.
Phishing website #3
Figure 7 – The phishing page prompts the user to enter their Adobe credentials to access, download or send files.
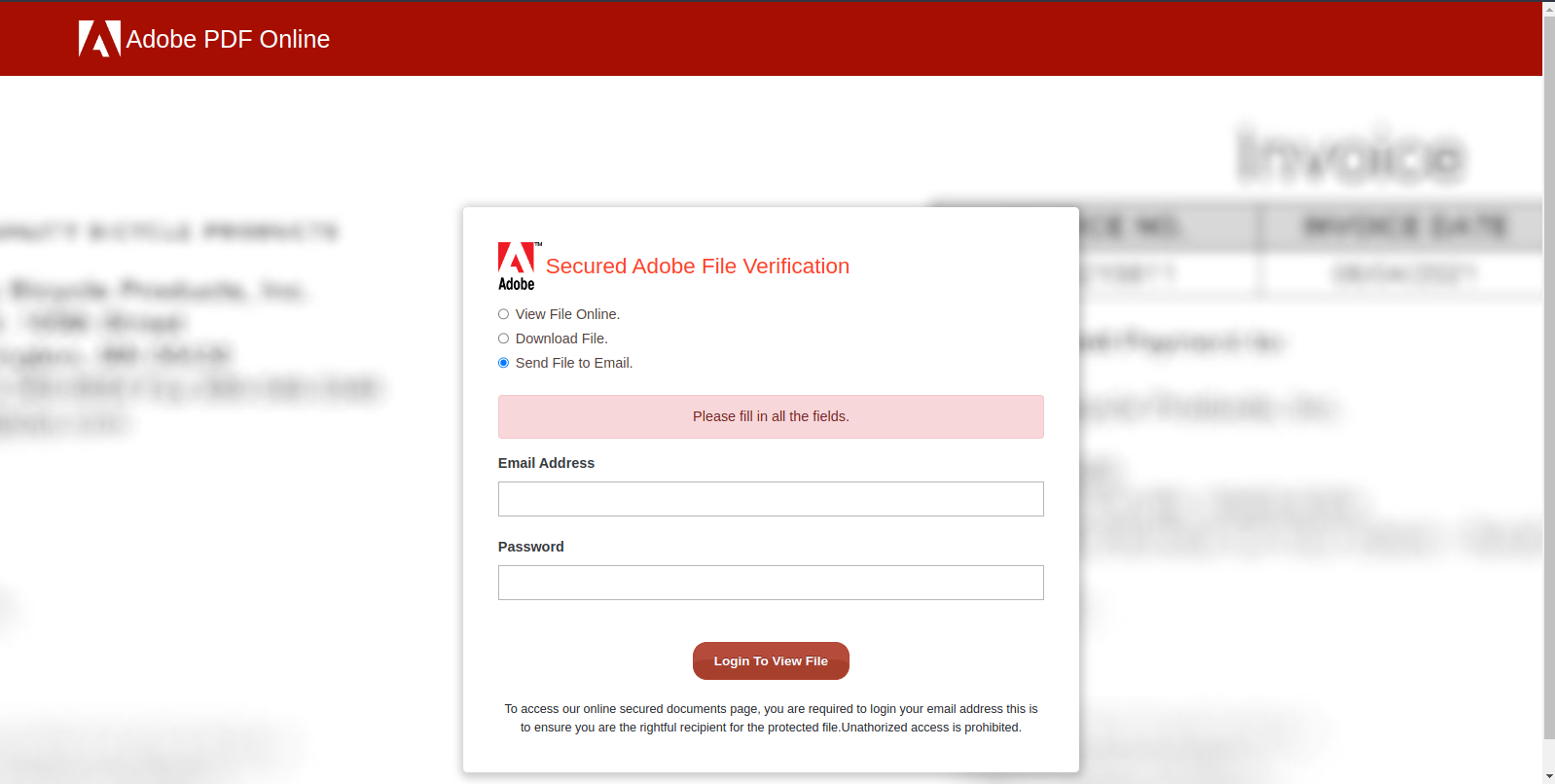
Figure 8 – The phishing page prompts the error “Please fill in all the fields.” after clicking “Login To View File”
Phishing website #4
Figure 9 – The phishing website prompts the user to download the document by clicking the “Download” button
After clicking the “Download” button, a login pop-up prompts the user to enter their credentials in order to login and access the document.
Figure 10 – The phishing page prompts the user to enter his Adobe login credentials
Phishing page #5
Figure 11 – The phishing website prompts the user to login via their Outlook, Office365, or other mail credentials to view the protected document
Figure 12 – The phishing page prompts the user to enter their Outlook
login credentials
Figure 13 – After entering credentials the phishing page shows an
error message to the user
Figure 14 – The phishing page prompts the user to enter their
Office 365 login credentials
Figure – 15 After entering credentials the phishing page shows
an error message to the user
Figure 16 – The phishing website also prompts the user to enter
via other mail credential of the user
Figure 17 – Upon entering the credentials the phishing page shows
and error
Safety Recommendations
- An SMS/email/Whatsapp message with a tone of urgency should be dealt with with extreme caution. This is true, especially in the case of any message from any organization.
- Always reach out with the organization and verify suspicious messages/emails before taking any action at your end.
- If you become a victim of cybercrime, particularly financial crime, call the national (India) cybercrime helpline 1930 or file a complaint at https://cybercrime.gov.in/
- Shreshta Protective DNS blocks phishing, malware, newly registered domain names and other malicious communication in real-time. For enterprises, please email info@shreshtait.com for a free 30-day trial.
Conclusion
With the growing cyber threat landscape, threat actors continue to operate phishing campaigns at scale and it’s important to stay vigilant and not fall prey to phishing scams.
By staying informed and vigilant, users can significantly mitigate the risk of falling victim to these sophisticated attacks.
Free 30-day trial of our threat intelligence
Threat actors constantly optimise and evolve their attacks to steal credentials and data and infiltrate networks. Our threat intelligence feeds are highly actionable and curated to protect against phishing, malware, C2 and newly registered domain names.
Interested? Please send us an email to info@shreshtait.com for a free 30-day trial.
References
A few other blog posts that you might be interested in,

