Executive Summary
Since October 2023, our threat intelligence team has been tracking online shopping frauds in India, targeting e-commerce platforms such as DMart, JioMart, Flipkart, Amazon, Tata Croma and Tata 1mg.
These deceptive websites lure users with substantial discounts, enticing offers, and prizes in an attempt to extract Personally Identifiable Information(PII) and payment details of the user. The phishing websites closely resemble the appearance of authentic e-commerce websites.
Motive
The motive of the threat actors is financial fraud and to harvest the Personally Identifiable Information (PII) of the user not limiting to,
- The name and address
- The contact number
- Debit/Credit Card details
Technical analysis of online shopping fraud websites
In this section, we will explore a few of online shopping frauds in India.
Phishing website #1 impersonating Flipkart
Figure 1 – Screenshot of the phishing website impersonating Flipkart
The deceptive website lures users with a good-to-be-true offer – a Tata Nexon car!

Figure 2 – The product page of the phishing website
Figure 3 – The page displays a list of prizes on offer
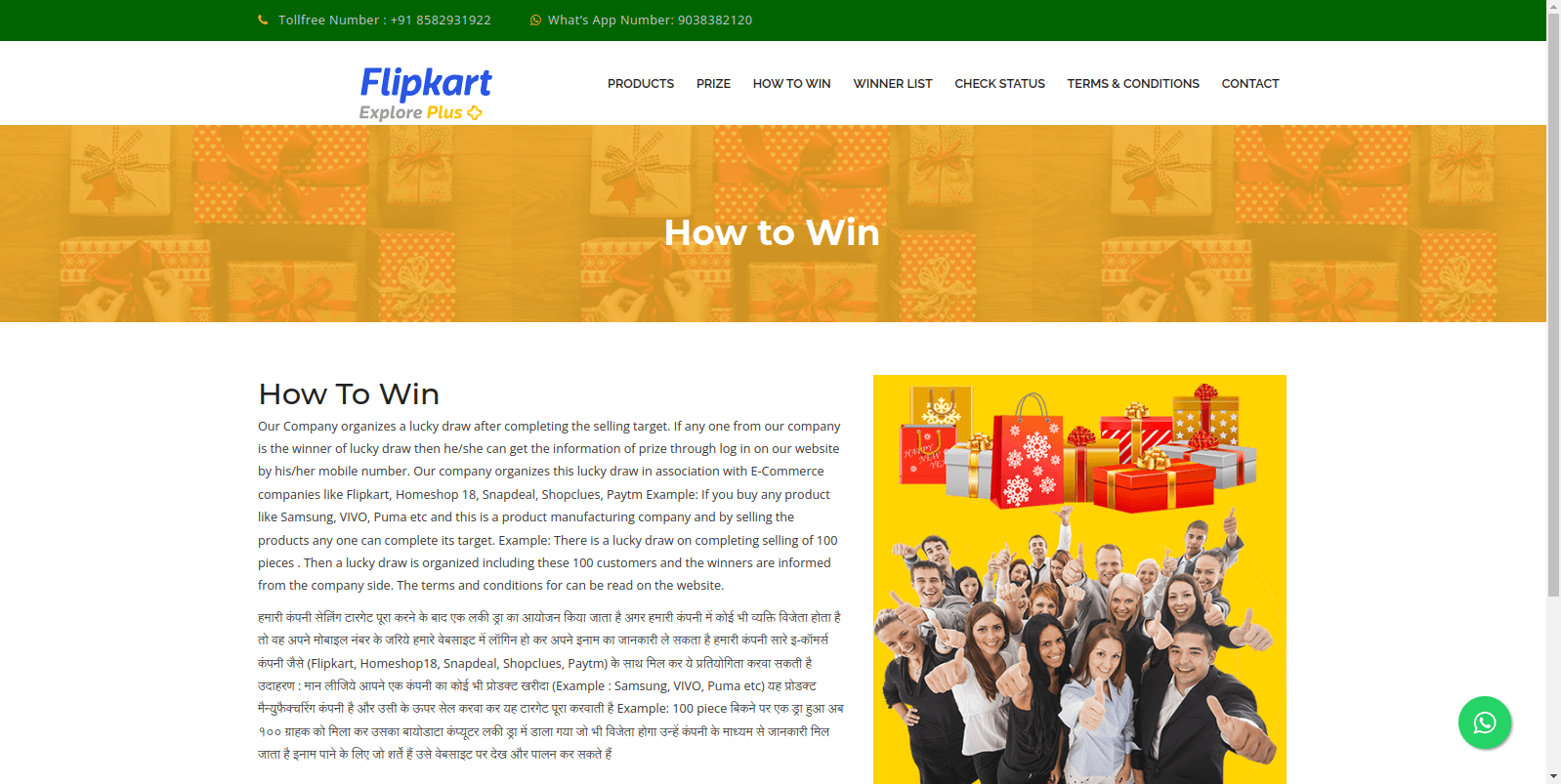
Figure 4 – The page provides instructions on how users can win the prizes
Figure 5 – The page displays a list of winners
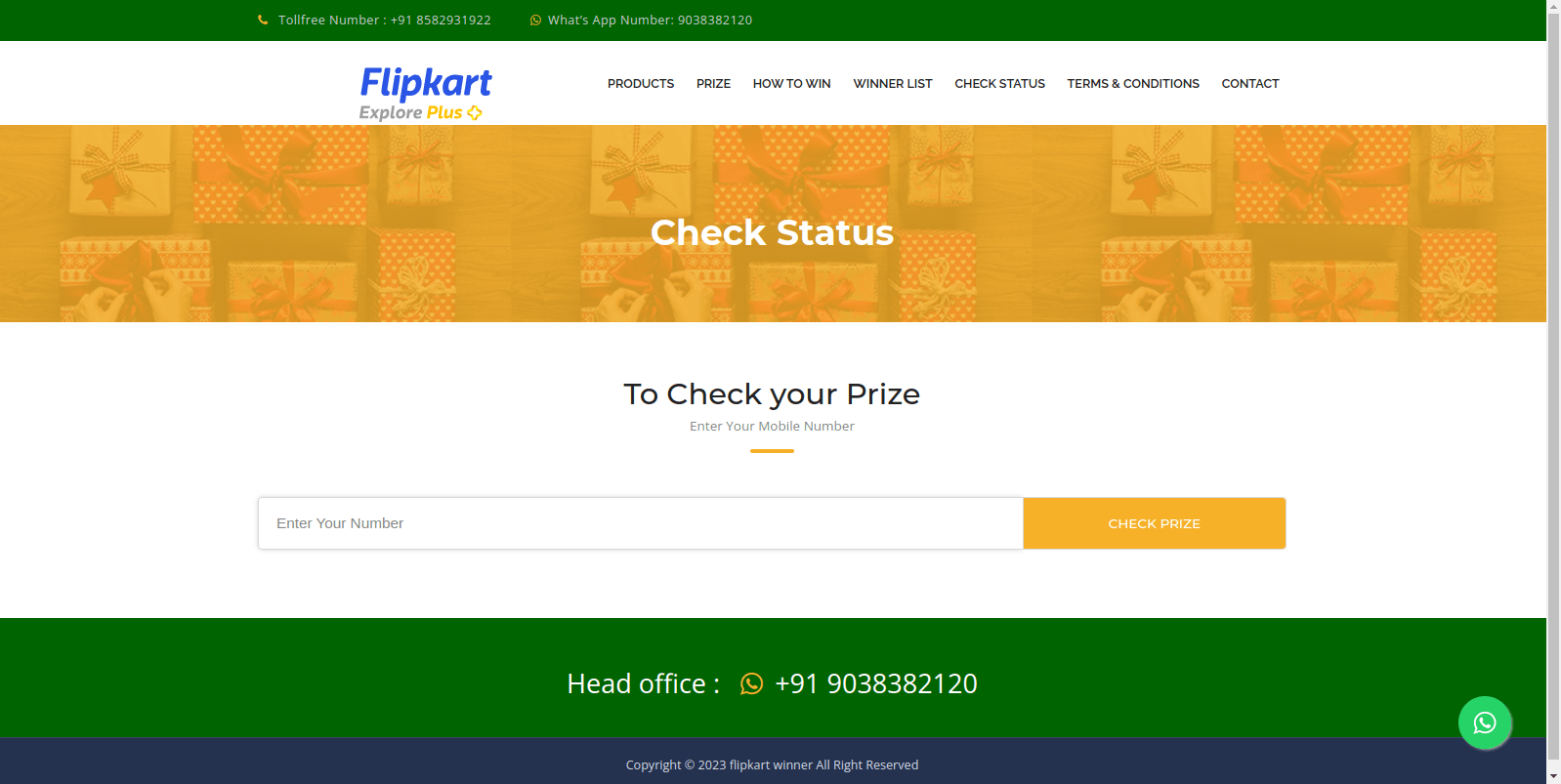
Figure 6 – The page urges users to enter their contact number to verify if they have won a prize.
Figure 7 – A page displaying the terms and conditions page of the phishing website
Figure 8 – Screenshot of the contact page on the phishing website.
Phishing website #2 impersonating Flipkart
Figure 9 – Screenshot of the phishing website #2 impersonating Flipkart
Figure 10 – Upon clicking on “Buy Now” the user is prompted to enter their address
Figure 11 – The website accepts any details and prompts the user to continue
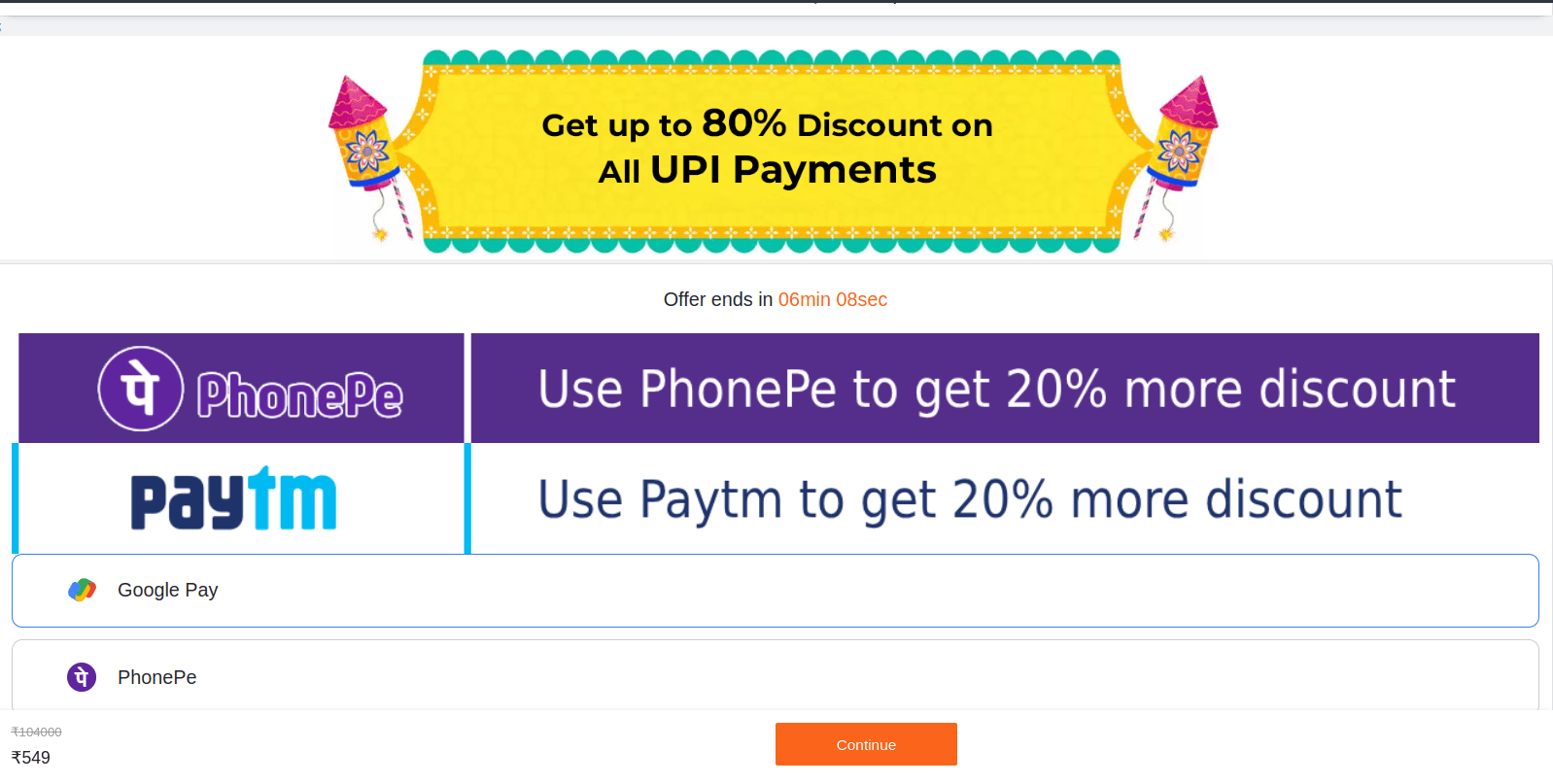
Figure 12 – The payment page prompts the user to select a payment method
Figure 13 – The website generates a fake order ID and prompts the user to make the payment using UPI
Phishing website impersonating Amazon

Figure 14 – Screenshot of the phishing website impersonating Amazon
Figure 15 – The product page of the phishing website
Clicking on “MORE DETAILS” redirects the user to the next page, where they are prompted to purchase the device.
Figure 16 – Upon clicking “BUY NOW,” the user is redirected to the authentic Amazon site.
Phishing website #1 impersonating DMart
Figure 17 – Screenshot of the phishing website impersonating DMart

Figure 18 – Screenshot of the “ORDER NOW” page of the phishing page
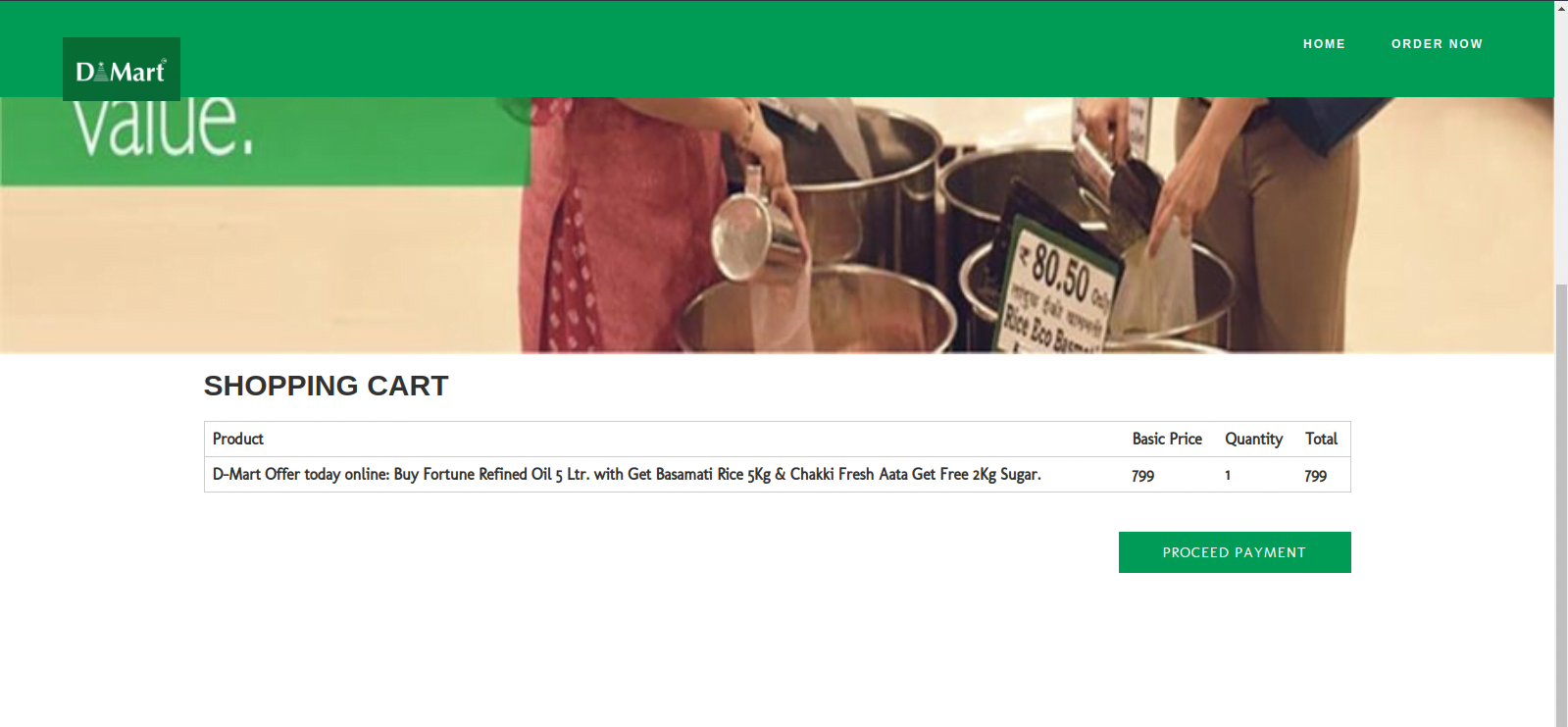
Figure 19 – The Shopping Cart of the phishing website
Figure 20 – Payment page requiring the users PII and payment details
Figure 21 – After clicking on “Pay,” the user is redirected to another page and prompts the message.
Phishing website #2 impersonating DMart
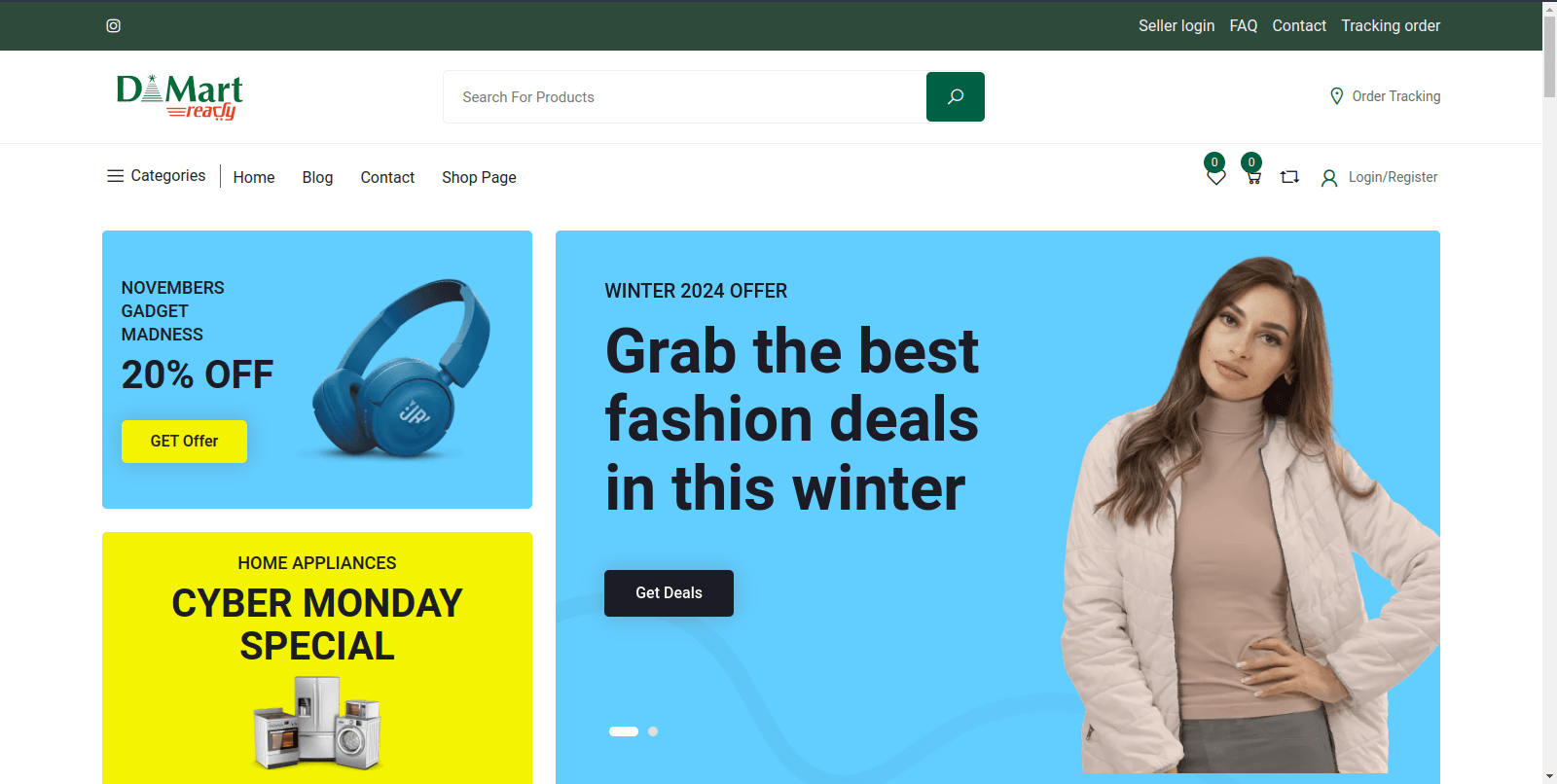
Figure 22 – Screenshot of the phishing website #2 impersonating DMart
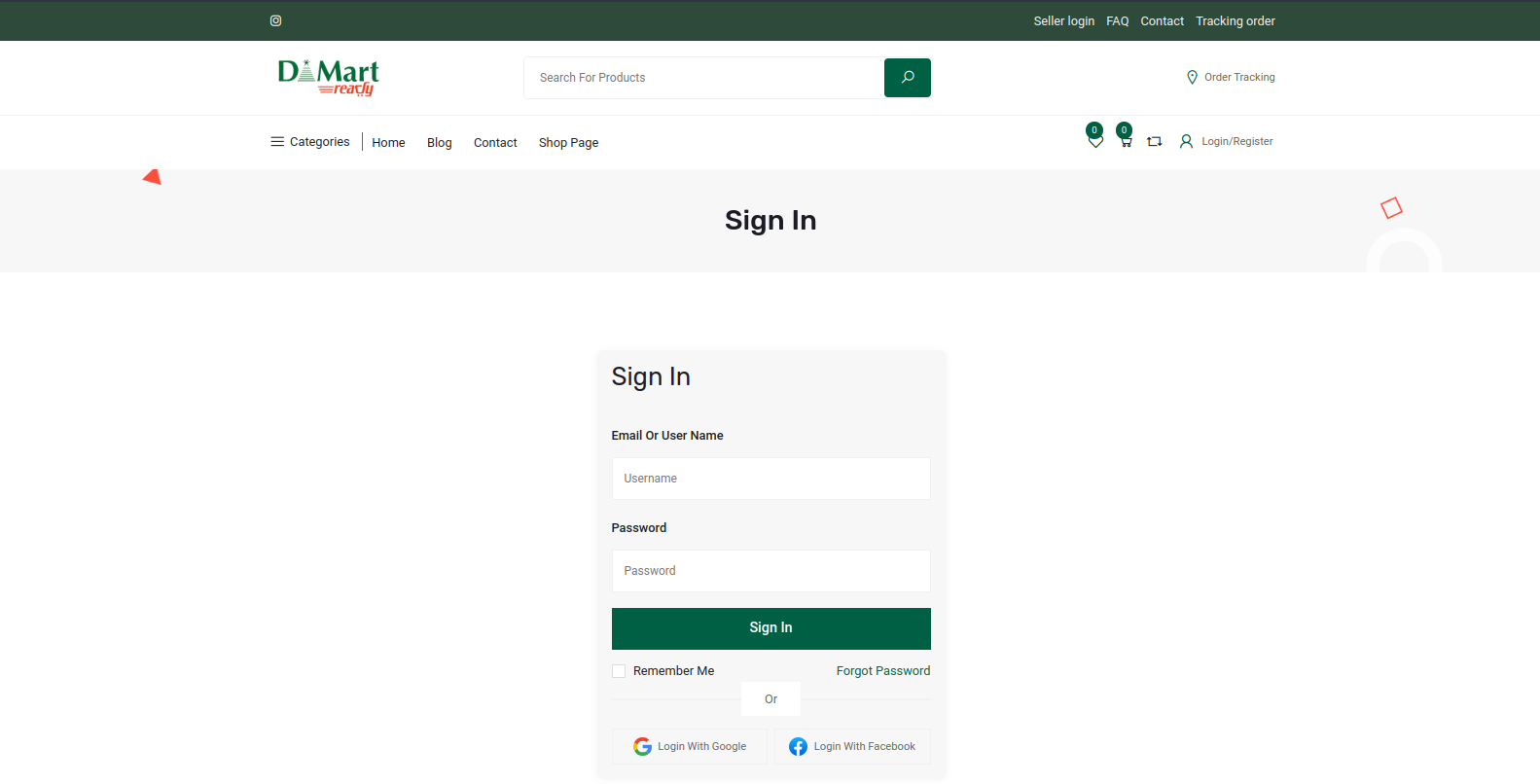
Figure 23 – Login page on the phishing website
The website displays an error when attempting to log in with invalid credentials.
Figure 24 – Create account page on the phishing website
The phishing website accepts any details and allows the user to login without email verification.
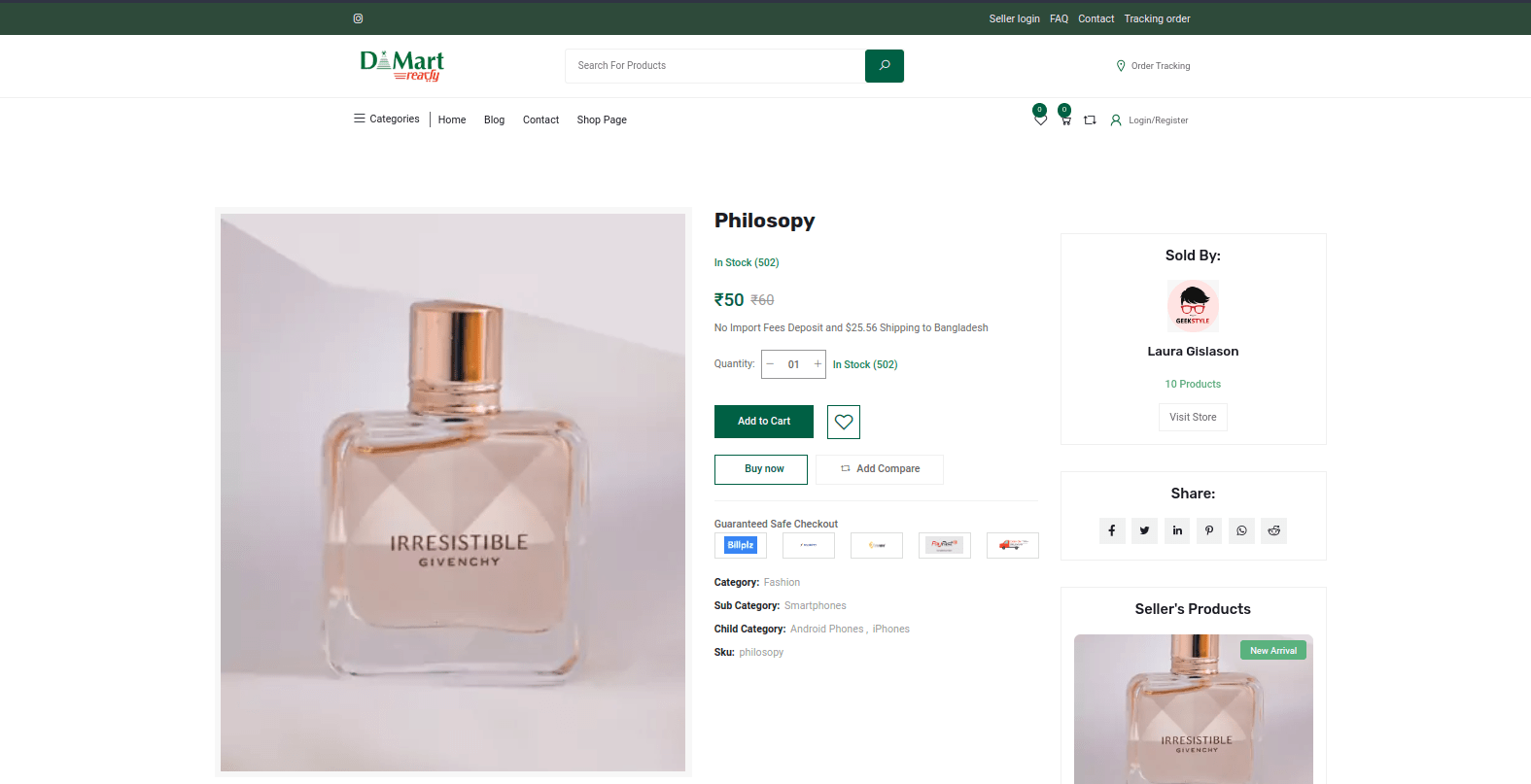
Figure 25 – Shopping cart on the phishing website
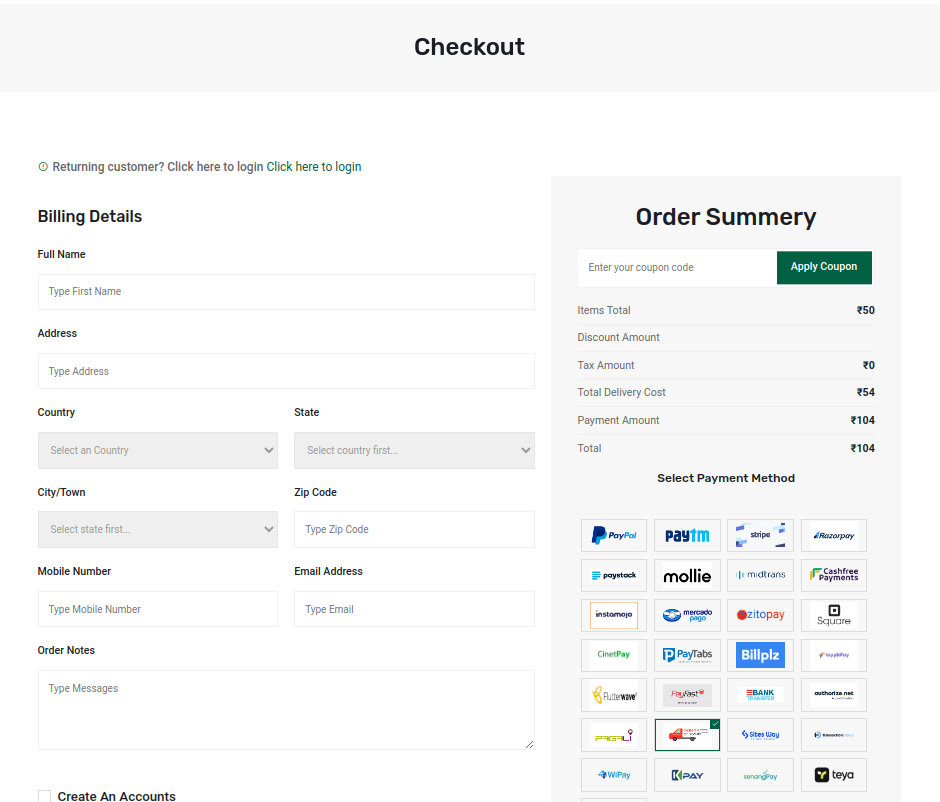
Figure 26 – The payment page prompts the user for PII details
After entering the details, selecting the payment method and submitting the form, the website throws an error “Client_id Missing From The Provided Configuration. Please Add Your Application Client_id.”
Phishing website #3 impersonating DMart
Figure 27 – Screenshot of the phishing website impersonating DMart
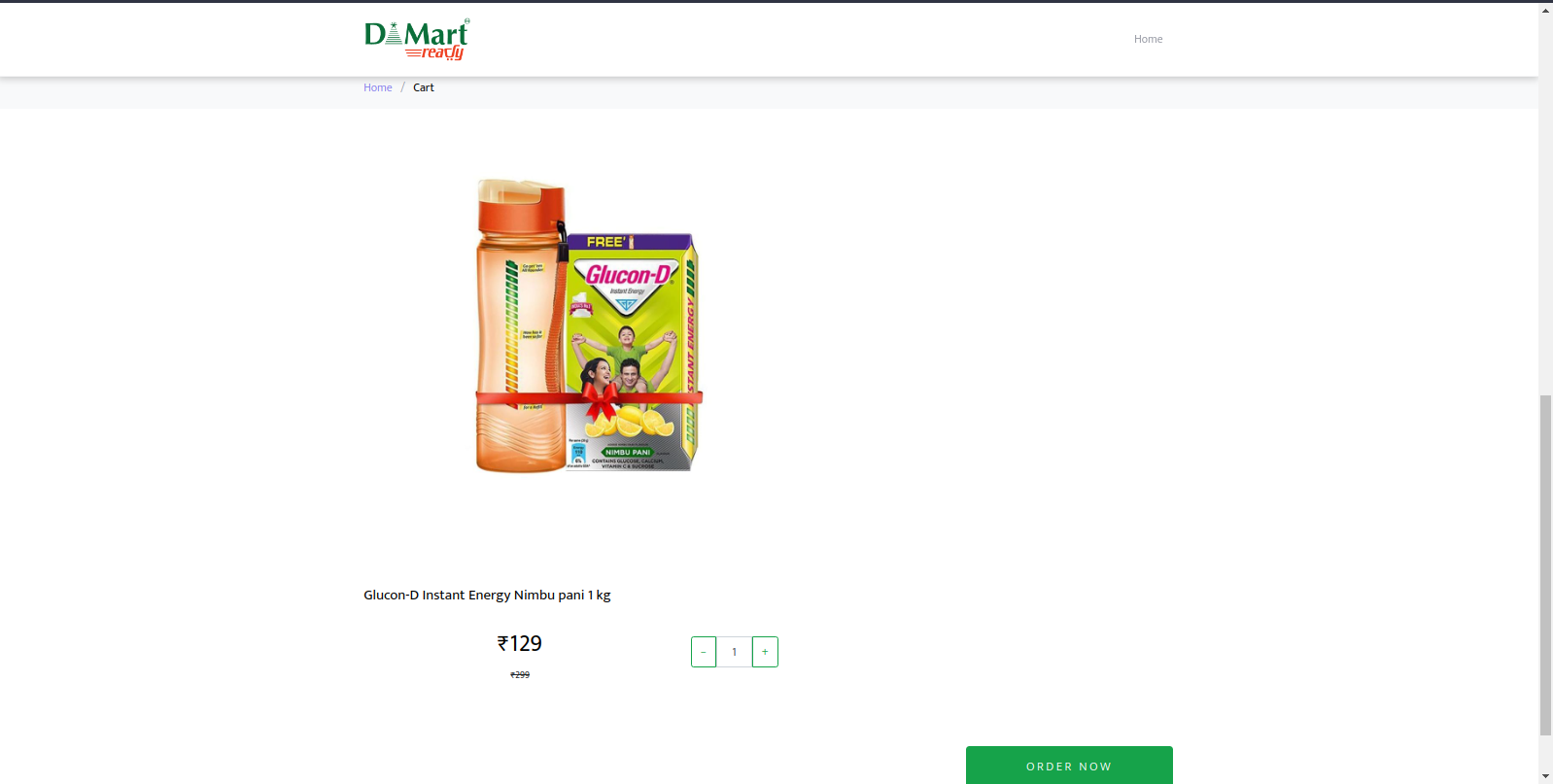
Figure 28 – After choosing the product, the user is redirected to the cart.
Figure 29 – The Billing Details page prompts the user to enter their PII details and card details
Figure 30 – The billing page accepts any details.
The phishing website prompts the user to download a DMart APK to finalize the pending order.
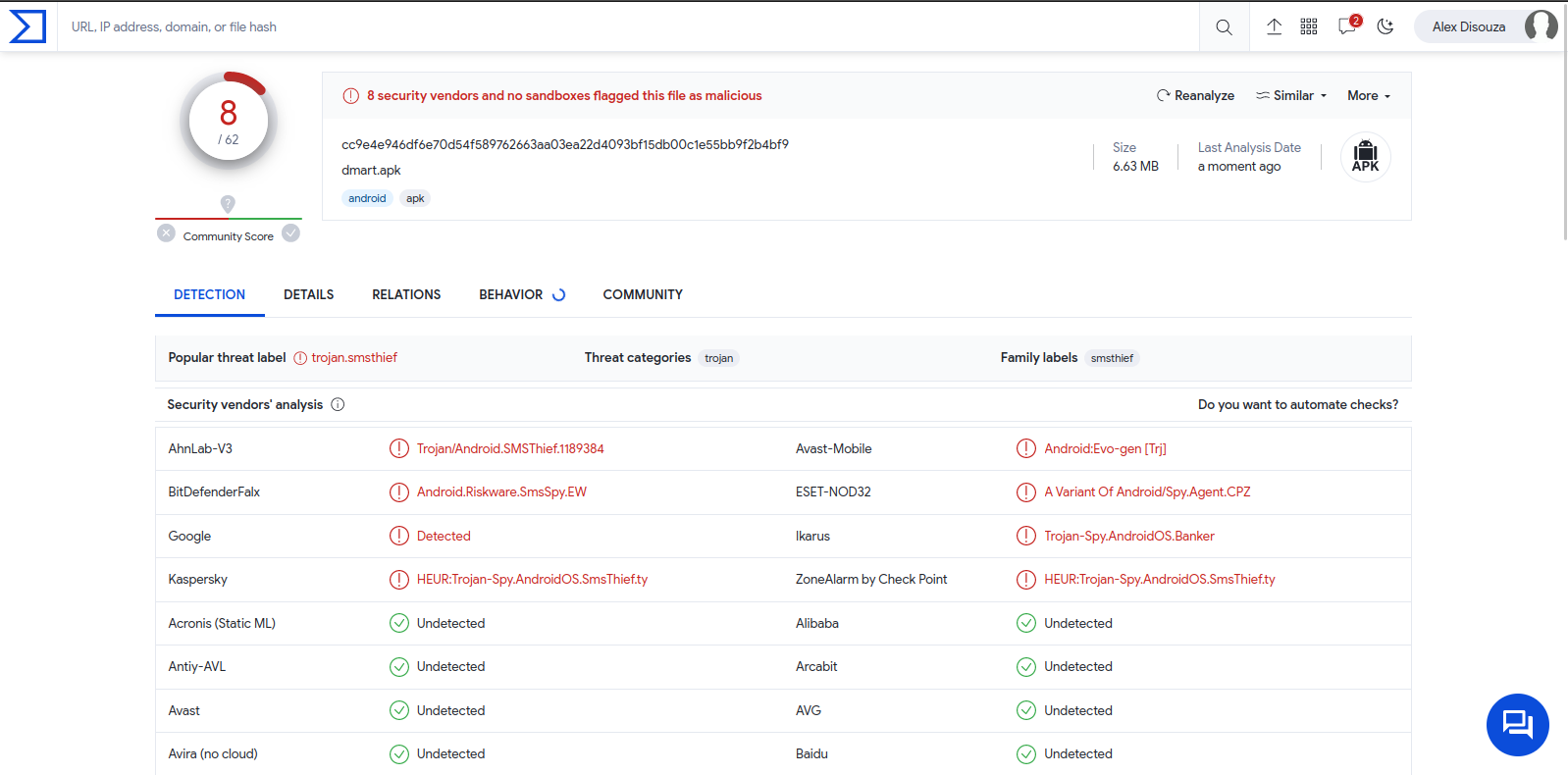
Figure 31 – VirusTotal identifies the APK from the phishing website as malicious
Phishing website impersonating Tata Croma Electronics
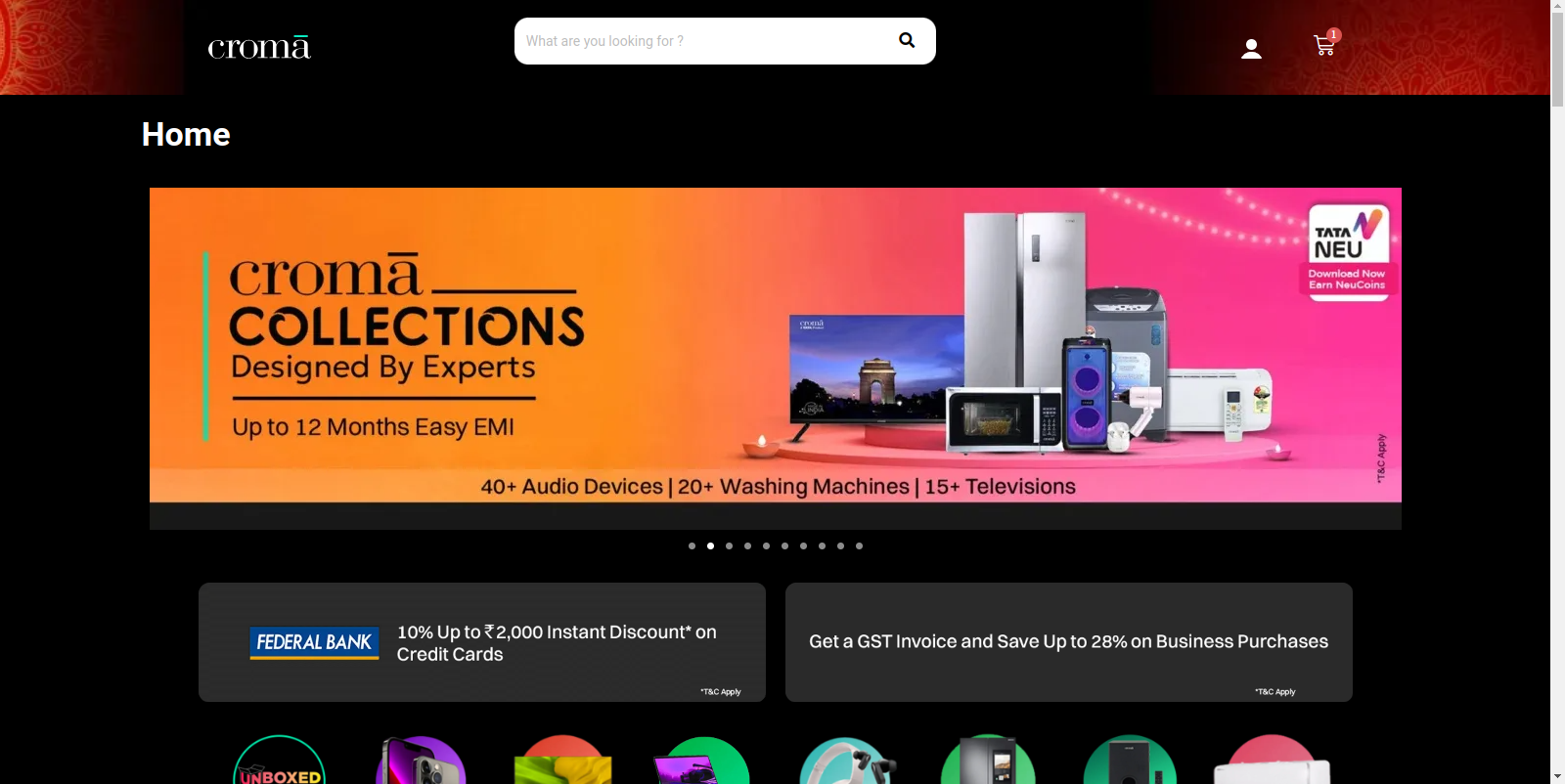
Figure 32 – Screenshot of the home page of the phishing website impersonating the Croma store
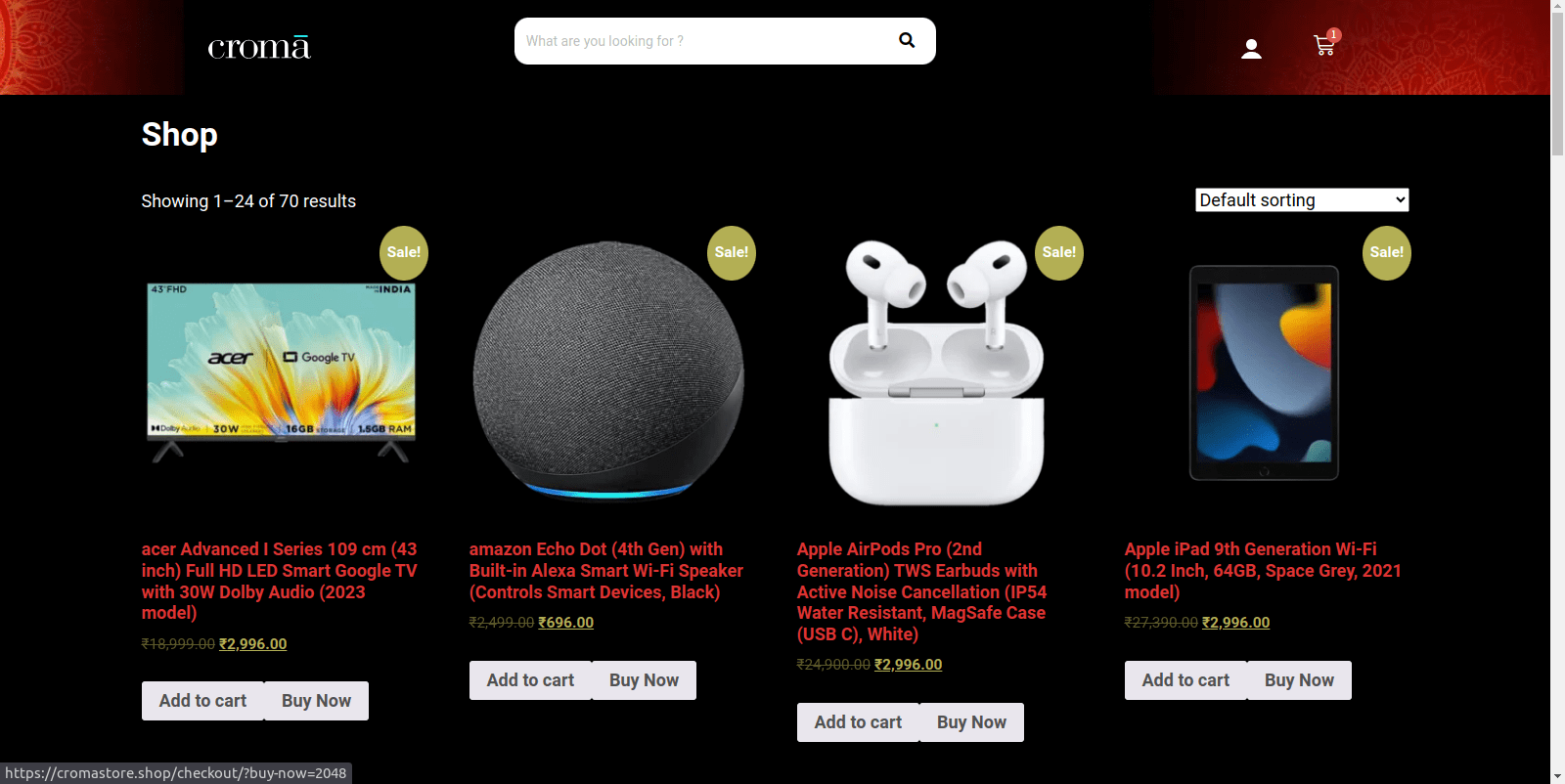
Figure 33 – Screenshot of the products page of the phishing website
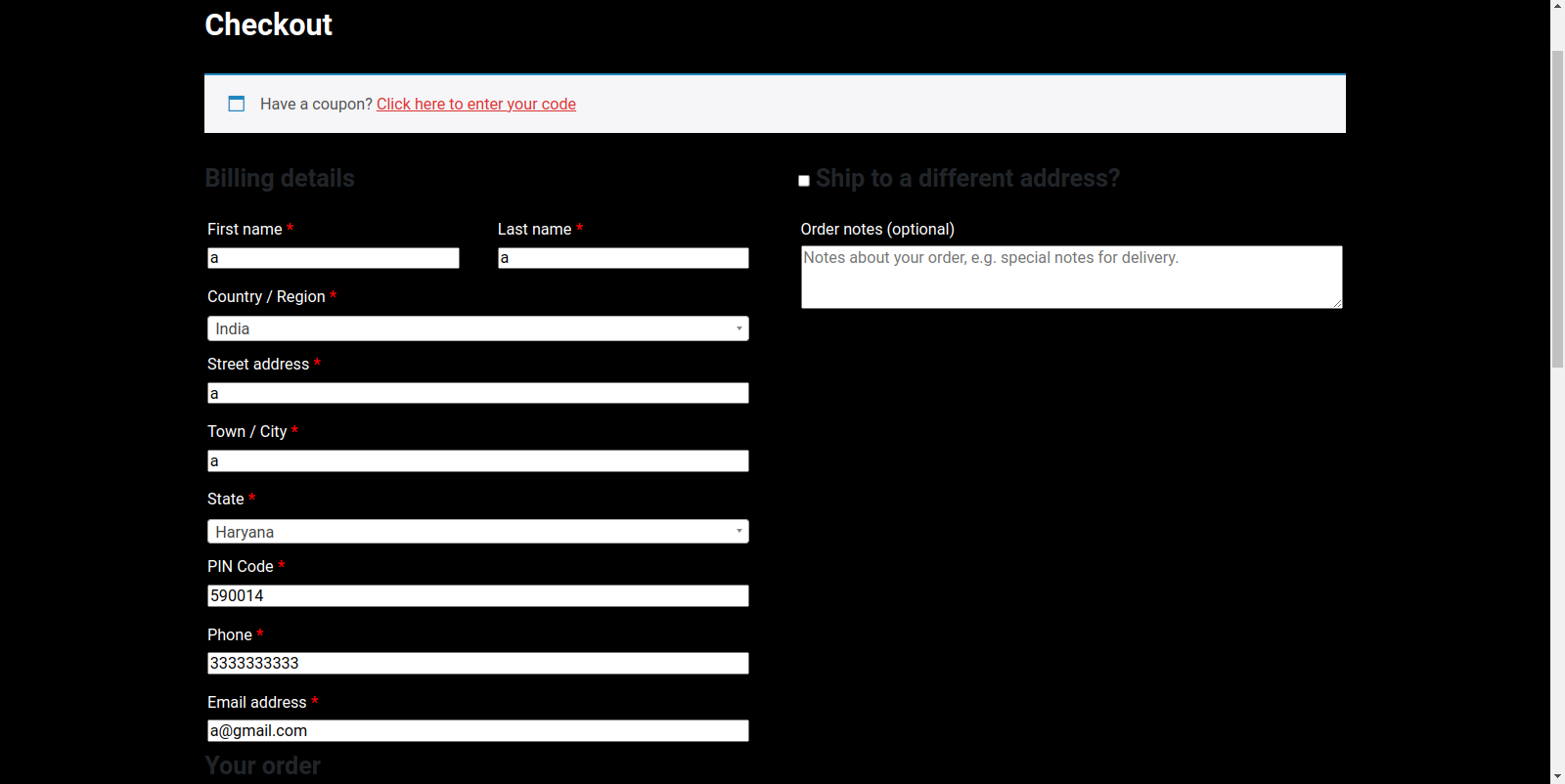
Figure 34 – Upon selecting “Buy Now,” the user is prompted to enter PII and payment details.
Phishing website impersonating JioMart franchisee application website
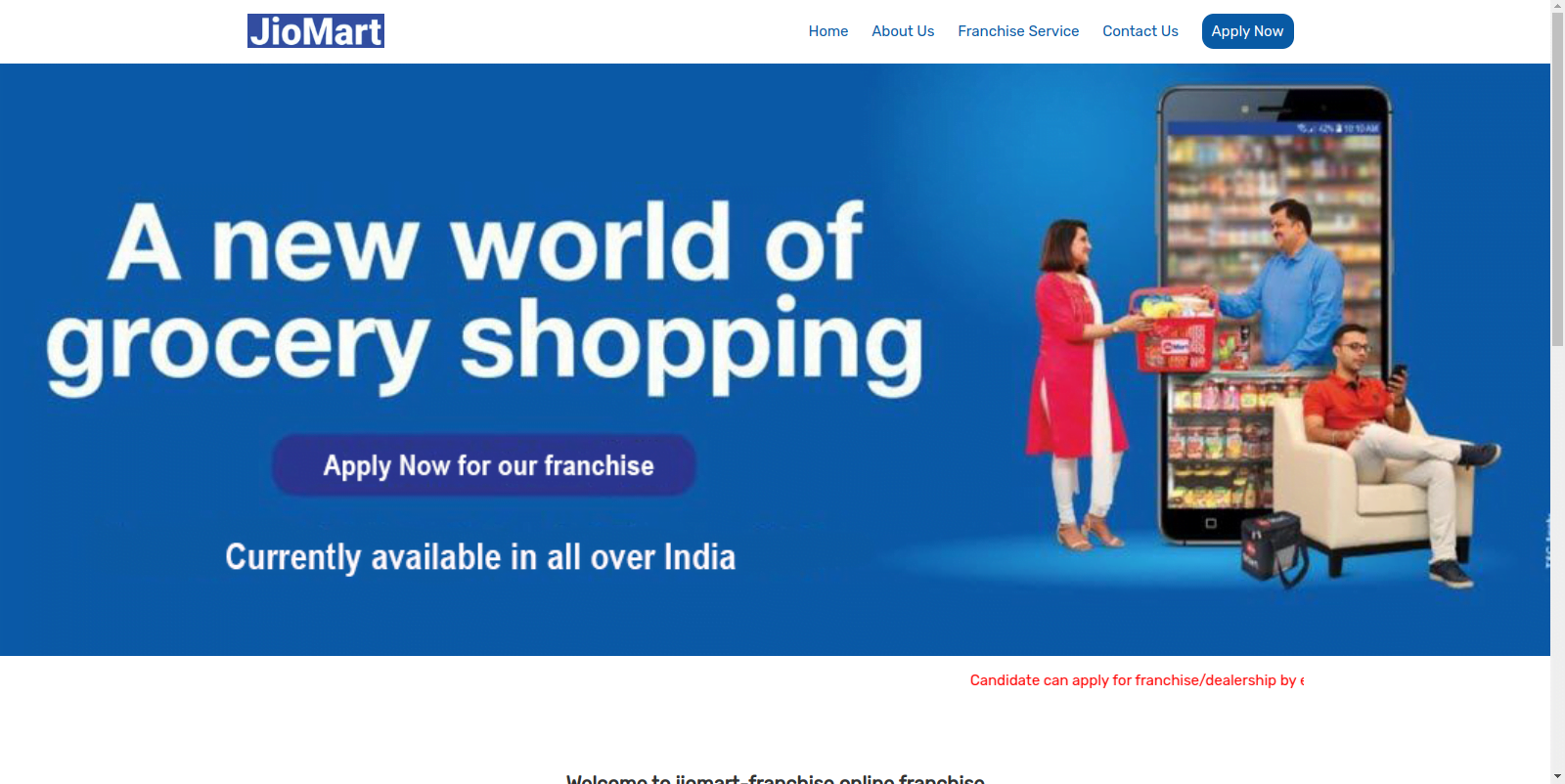
Figure 35 – Screenshot of the phishing website impersonating JioMart franchisee application website
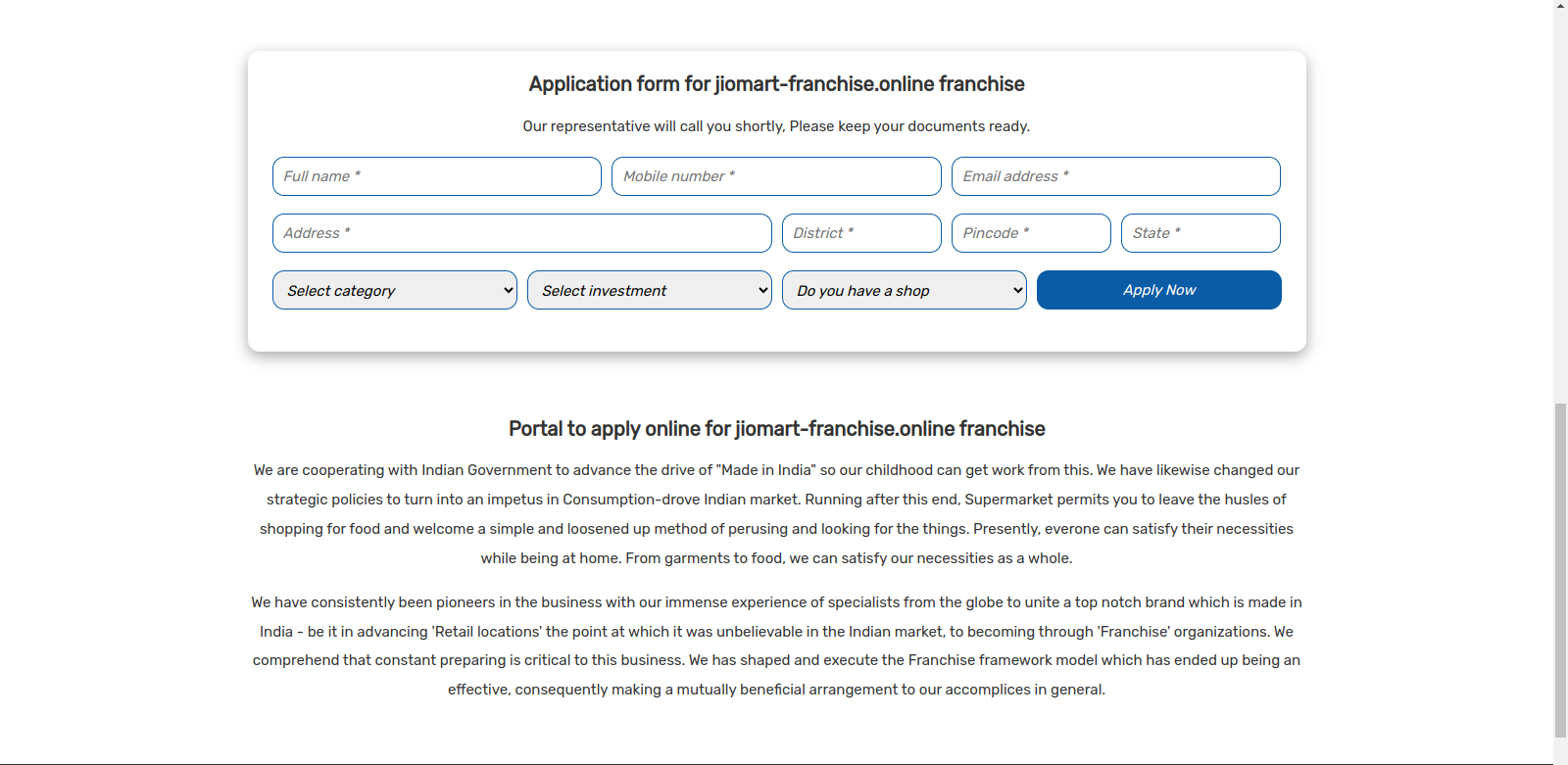
Figure 36 – After clicking on “Apply Now,” the user is prompted to fill out a form.
Figure 37 – After the user submits the form, the user is informed that their application was successful and a representative will contact them soon.
Phishing website impersonating JioMart
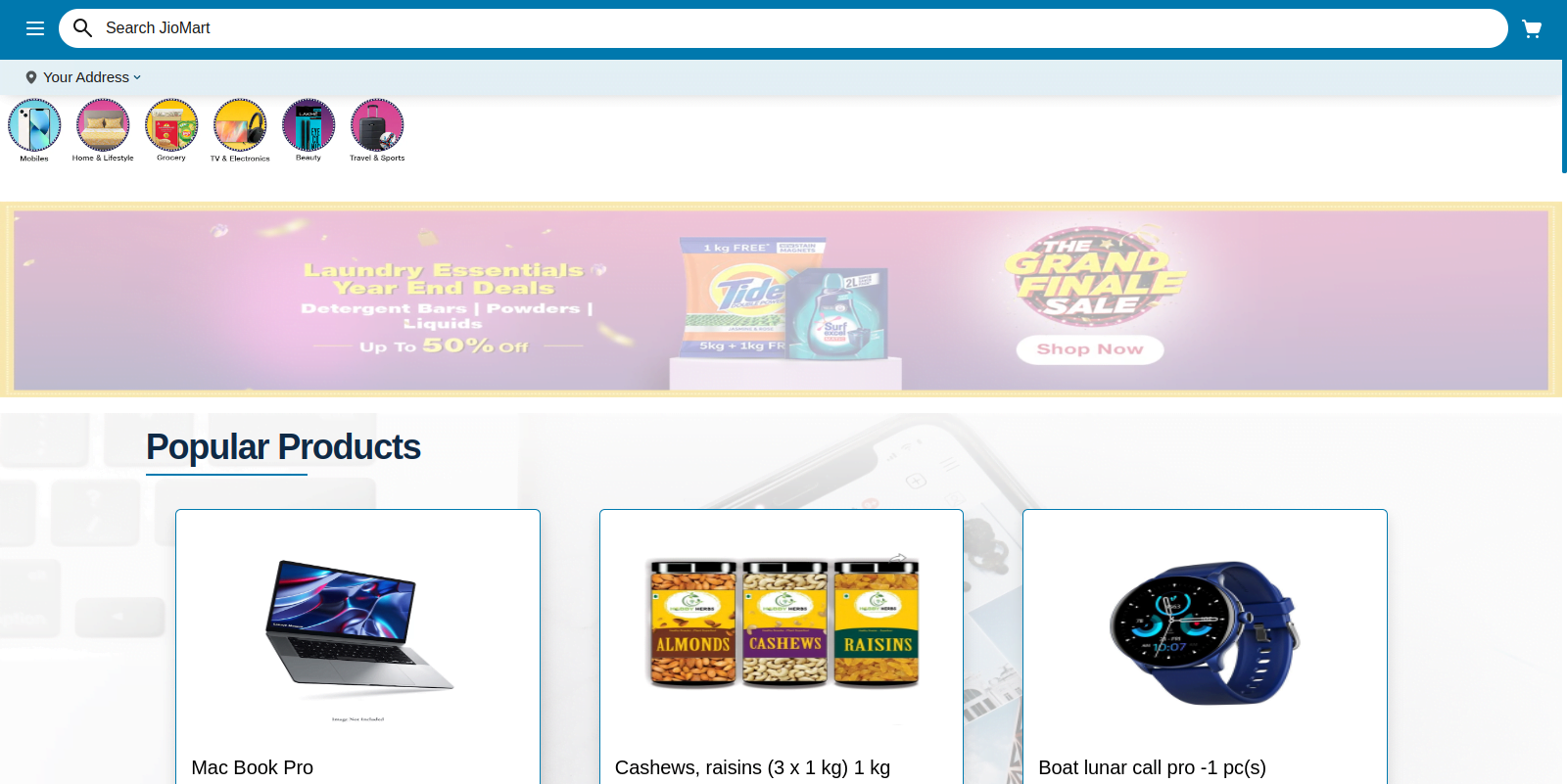
Figure 38 – Screenshot of the phishing website impersonating JioMart
Figure 39 – After clicking on “Buy” the user is asked to Proceed to payment page
Figure 40 – The payment page prompts the user to enter their personal details and credit card information.
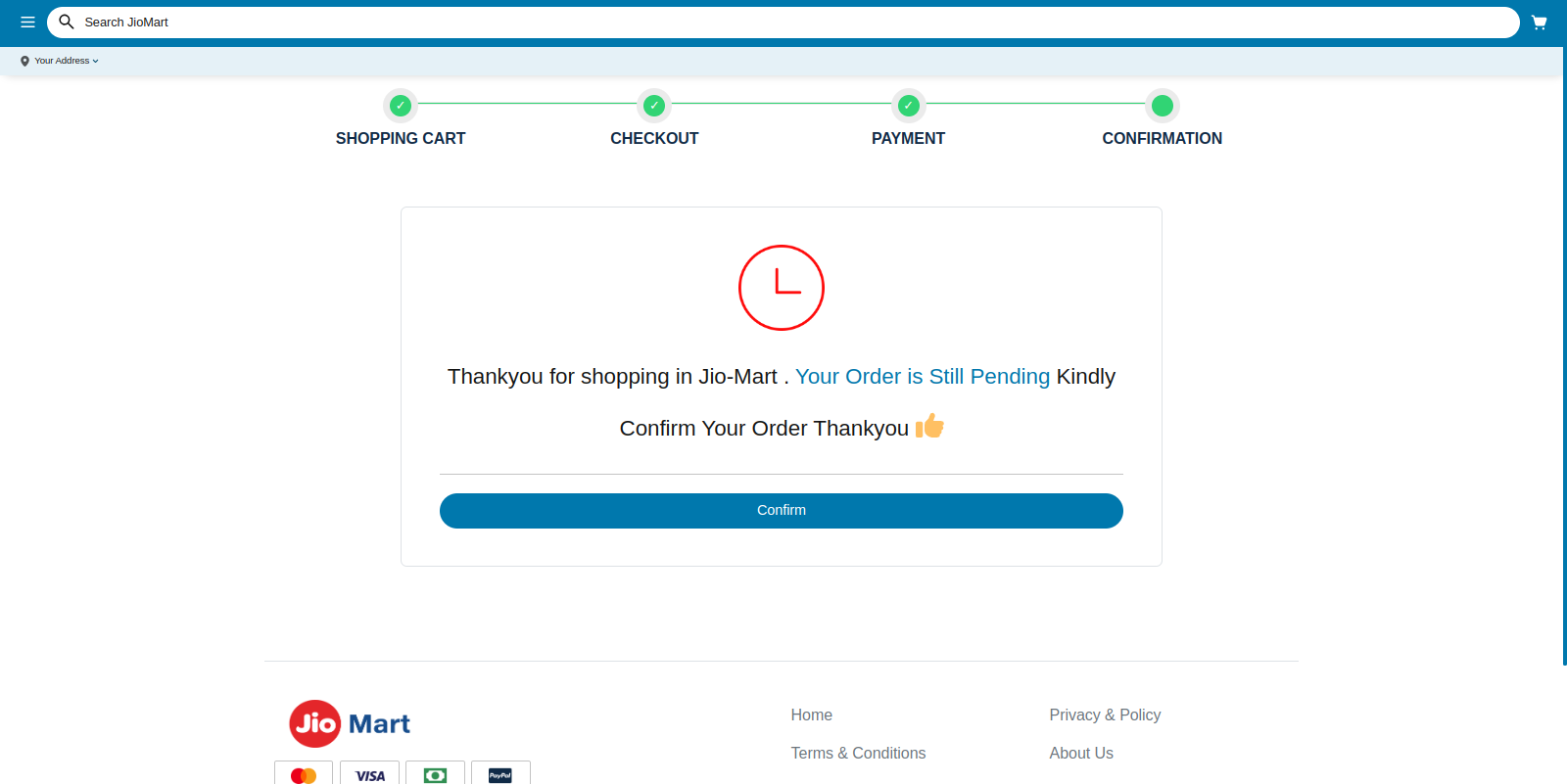
Figure 41 – The payment page accepts false details and asks the user to confirm their order
After confirming, the website prompts the user to download a JioMart APK.
APK – The Android Package with the file extension apk is the file format used by the Android operating system
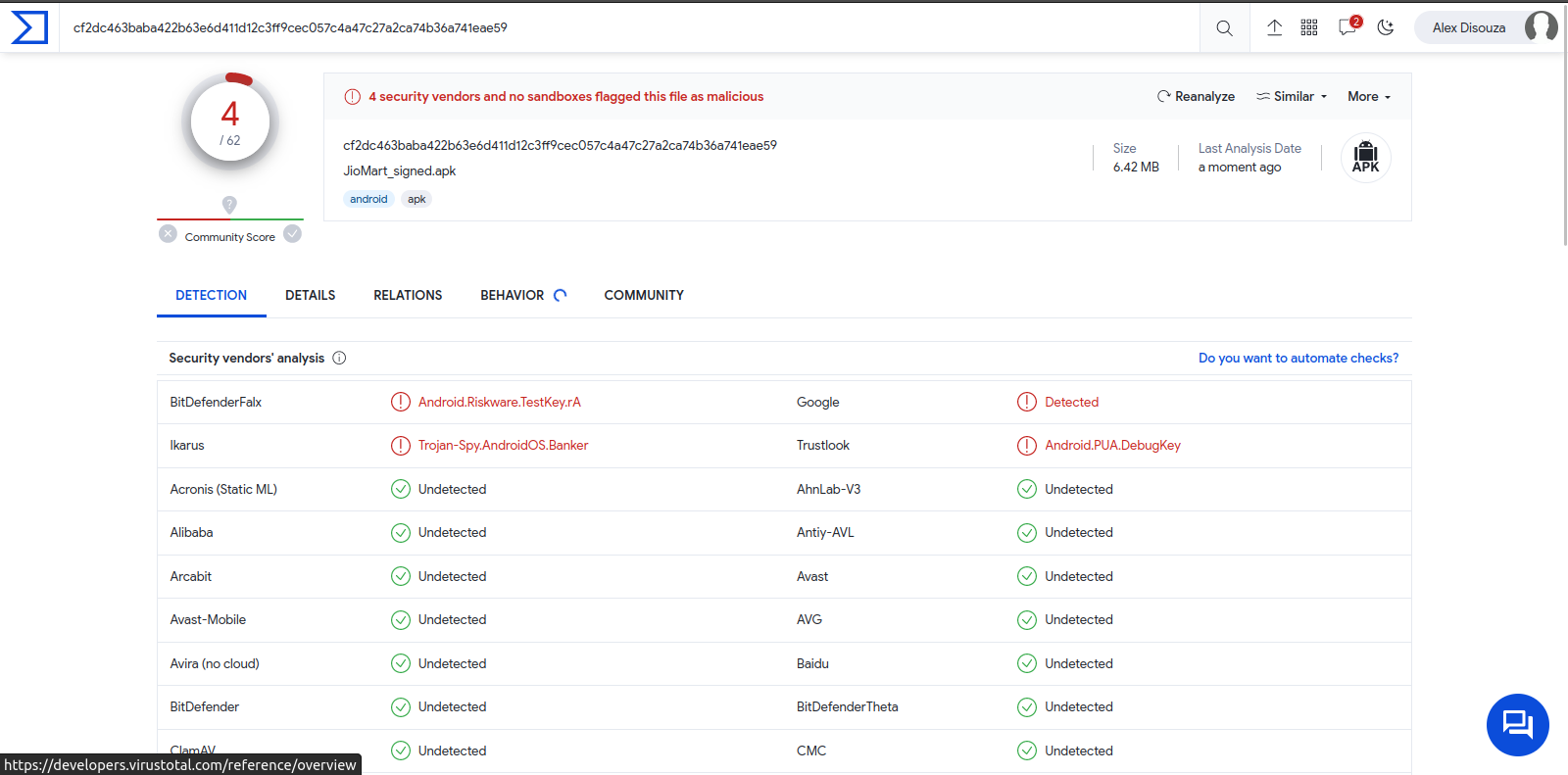
Figure 42 – The APK is flagged by VirusTotal as Android.Riskware.TestKey.rA, Trojan-Spy.AndroidOS.Banker and Android.PUA.DebugKey
Phishing website #1 impersonating Tata 1mg
Figure 43 – Screenshot of the phishing website impersonating TATA 1mg pharmacy
The website prompts the user to apply for the TATA 1mg pharmacy franchise
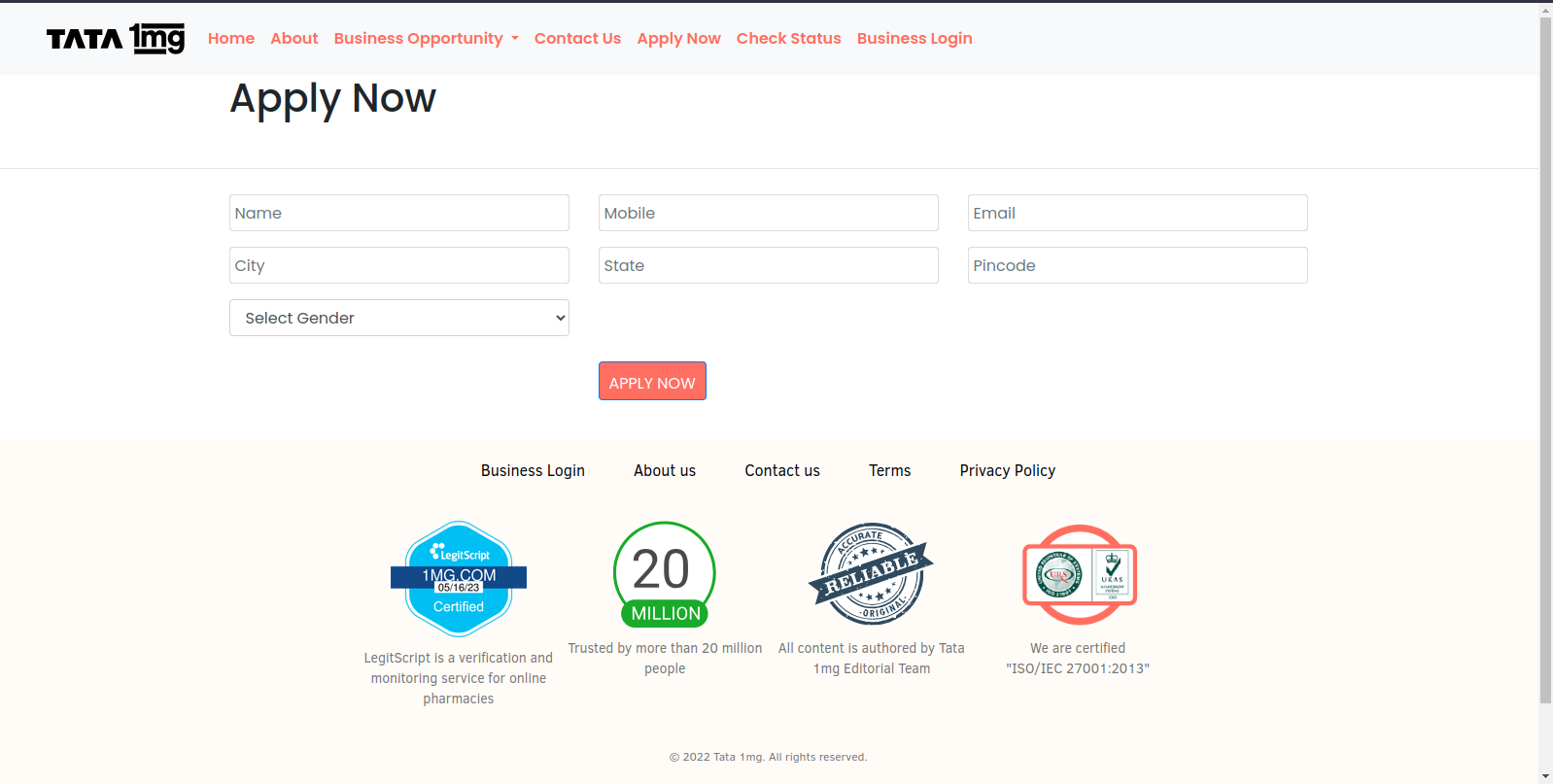
Figure 44 – Clicking on “Apply Here” prompts the user to enter their PII details.
Upon submitting the details on the “Apply Now” page, the user receives a “Successfully Applied” message
Phishing website #2 impersonating Tata 1mg
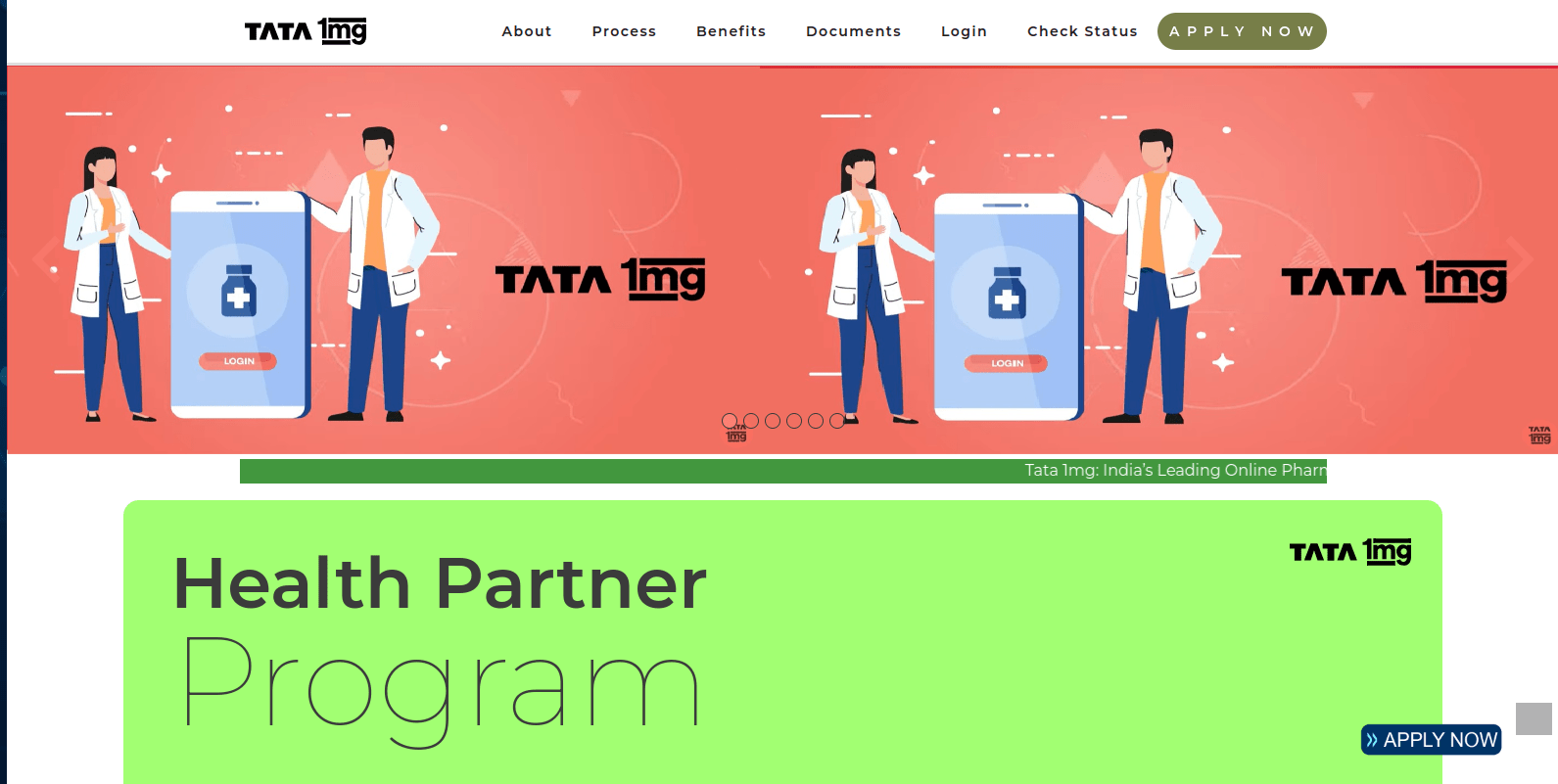
Figure 45 – Screenshot of the phishing impersonating TATA 1mg
The phishing website prompts the user to apply for the TATA 1mg pharma franchise
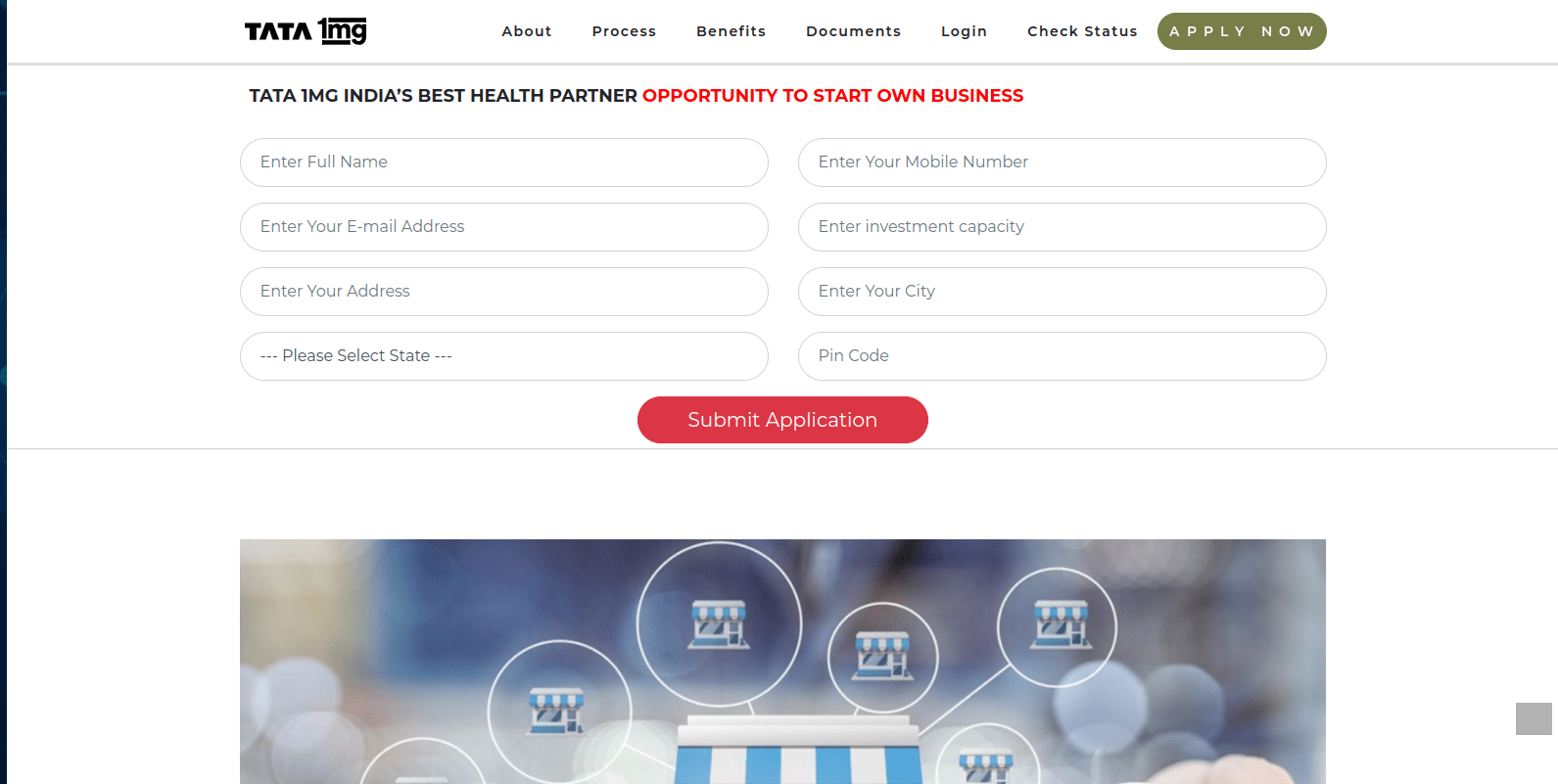
Figure 46 – After clicking on “APPLY NOW,” the user is prompted to enter their PII details.
Upon submitting the details, the user is greeted with a message informing that their information has been successfully added.
Safety Recommendations
- Purchase products directly from the official website of the brand or from recommended authorized retailers
- Research the seller before purchasing the product
- Be cautious of purchasing products from websites offering prices significantly lower than those on the official website, or offering free coupons/items.
- If you become a victim of cybercrime, particularly financial crime, call the national (India) cybercrime helpline 1930 or file a complaint at https://cybercrime.gov.in/
Conclusion
Online shopping frauds in India are on the rise. Threat actors are impersonating not only the online shopping platforms in India but also targeting business users who are interested in operating a franchise store of popular brands.
Interested to monitor your brand on the Internet?
Please send us an email to info@shreshtait.com for an early bird access to our brand monitoring product.
Recommended reading
A few other threat intelligence blog posts that you might be interested in,
