An “open resolver” is a DNS server that accepts and resolves a domain name recursively for anyone on the internet. In this blog post, we will share the security risks of open resolvers and best practices.
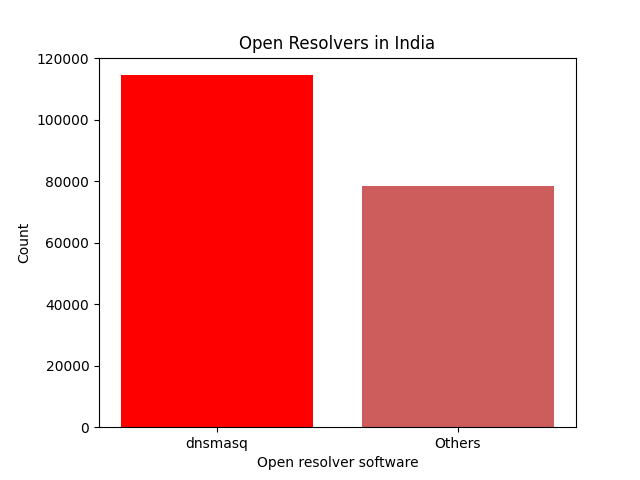
At the time of writing, there were 192920 open resolvers in India with recursion enabled. While most of these are broken consumer premise equipment (CPE), few are open probably due to misconfiguration on the part of the DNS administrators.
Out of the total count, 114521 were running dnsmasq. A popular DNS server software found in CPE firmware.
What security risks do open resolvers pose?
An open resolver can be abused by threat actors to initiate a Denial of Service(DoS) attack. Simply put, running an open resolver is a bad security practice.
Case in point – DNS amplification attack or a Denial of Service attack using an open resolver ?
A Domain Name Server (DNS) amplification attack is a popular form of distributed denial of service (DDoS) that relies on the use of publically accessible open DNS servers to overwhelm a victim system with DNS response traffic.1
Between Jan 15, 15:01:17 and Apr 10, 01:28:31, a single instance of our honeypot, received 135972316 DNS queries from Brazil for the domain higi[.]com
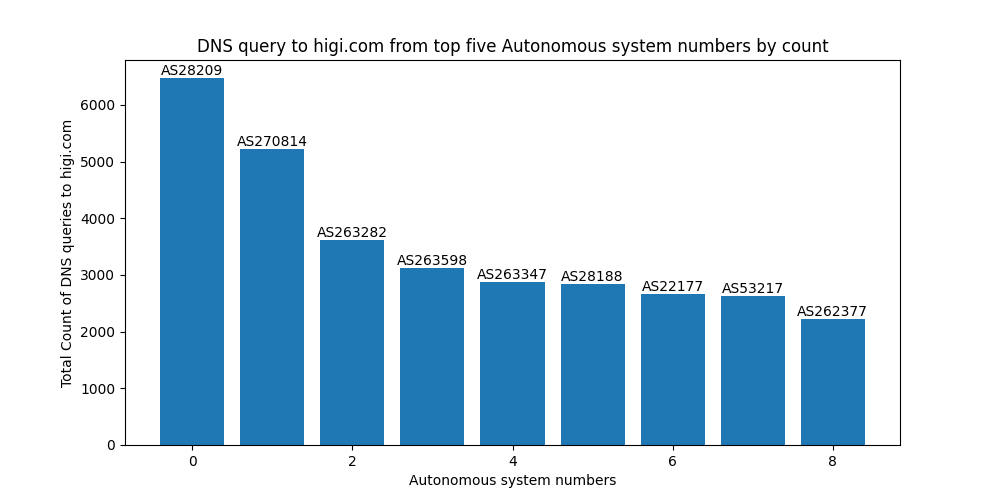
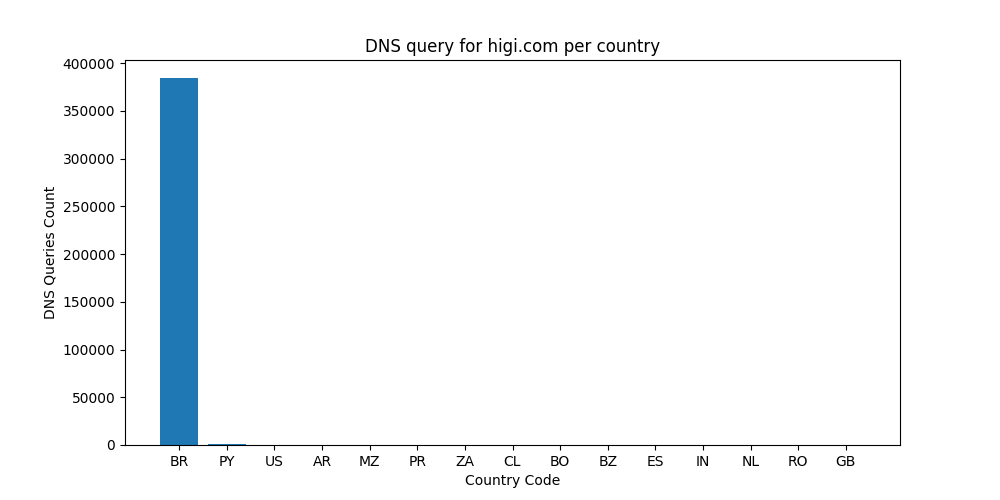
According to https[:]//www[.]higi.com,
Higi is a consumer health engagement company that combines physical access via a network of digital Smart Health Stations with complementary web and mobile tools that enable a consumer’s health engagement, making it easier for them to understand and act on their health and healthcare needs.
Objective of the attack
On primary evidence, it is most likely that the objective of the attack is to send a large influx of DNS query traffic to the authoritative name servers of higi[.]com. When writing the DNS A record of higi[.]com had a TTL value of 600 seconds.
A global coffee chain serving an open resolver ☕
It’s not just CPE boxes with broken firmware/configuration which have the problem of open resolvers, Shreshta threat analysts have detected enterprise DNS resolvers, resolvers part of network operators and even a global coffee chain running an open resolver!
Best practices
As a recursive resolver operator, below are some of the best practices that you should follow
- Allow access to the recursive resolver only to authorised IP addresses/netblock
- Response rate limiting
- On an authoritative only name server, disable recursion
- For network operators – Implement BCP38 (Network Ingress Filtering)
We also urge recursive resolver & authoritative name server operators to explore KINDNS – Stands for Knowledge-Sharing and Instantiating Norms for DNS and Naming Security. It’s a program supported by ICANN to develop and promote a framework that focuses on the most important operational best practices or concrete instances of DNS security best practices.
We have contacted higi[.]com as well as the DNS administrators of the global coffee chain to share our findings.
As seen in this post, it’s important to follow best practices to eliminate the risks of running an open resolver.
